Machine learning helps users automate tasks using advanced algorithms. While it has applications in various fields, ML has shown high potential in cybersecurity.
This detailed guide walks you through machine learning and cybersecurity. It covers the basics of ML in cybersecurity and the current applications and limitations of machine learning in computer security, helping you grasp this innovative field. Let's start from the beginning.
In this article
What Is Machine Learning?
Machine learning is an artificial intelligence study focusing on statistical algorithms that mimic how humans learn. Data scientists train algorithms for classifications, predictions, and decisions within applications and programs.
Machine learning models start with vast amounts of training data. They train themselves on the given data to understand patterns and make predictions. They later get new data and process it faster using established practices.
Thus, machine learning models evolve and become better. Their most prominent applications include chatbots, text generation, self-driving cars, and medical diagnostics. Now let's dive into machine learning and security.
The Basics of Machine Learning in Cybersecurity
Machine learning models use algorithms and data sets to make patterns and statistical analyses about your computer's behavior. They can make assumptions and take action, even if it's not in their programming. Given its features, machine learning is crucial in cybersecurity.
With the increase in cyberattacks and their constant improvement, traditional cybersecurity measures aren't sufficient enough to protect you. However, machine learning is a game-changer in cybersecurity, as it can identify threats and adapt to solve them accordingly.
ML Predictive Analysis
Machine learning algorithms detect patterns and make predictions accordingly. Once a machine learning model detects patterns, it can predict a likely outcome. That means it can recognize a potential threat before it impacts your computer security and take measures to prevent cyberattacks.
Moreover, machine learning constantly evolves, allowing it to predict and prevent even the latest, most undetectable cyber threats.
Anomaly Detection

Besides making predictions, machine learning can play a role in behavior analytics. ML models can monitor and analyze user activity to learn from it and understand patterns. They can protect the system from a potential security breach if it notices any strange behavior.
Monitoring user behavior patterns includes network traffic, system logs, app usage, typing speed, and other activity. While humans can't detect those, computers can. Machine learning models undergo training to understand typical user behavior in a particular network. Once they notice anomalies, they flag them and prevent a potential security breach.
Traditional computer security tools can't detect anomalies in network traffic and user behavior, resulting in security breaches and other cyber threats. Machine learning provides that security, as it constantly learns and improves to detect unusual patterns and prevent cyberattacks.
Automated Security Operations
Another excellent benefit of machine learning models is their ability to automate processes. Since they improve by repeating specific tasks, they learn new functions by implementing existing patterns in new scenarios. That creates an automated workflow.
Machine learning models for computer security can learn and get better at performing security operations, helping users automate them. Thus, security teams can leave repetitive security processes to machine learning and focus on more pressing and advanced tasks.
Current Applications of Machine Learning in Cybersecurity
Machine learning offers many benefits to cybersecurity. It has already planted its seeds in computer security, making it better and safer. Here are the most common applications of machine learning in cybersecurity.
Intrusion Detection Systems

Intrusion detection systems (IDS) are network security tools that monitor and detect malicious activity in network traffic. An IDS detects a network threat and alerts security administrators to address them. Thus, even though these systems can't resolve security threats, they identify them and instantly inform IT admins, enabling them to fix issues.
Machine learning algorithms in IDSs automate the threat detection process. They automatically detect cyber threats and inform security teams to help resolve them. Moreover, machine learning technology allows IDSs to learn and gradually improve by analyzing previous data and scenarios.
✅UEBA Systems
User and entity behavior analytics (UEBA) systems are cybersecurity tools for detecting user, router, server, and network behavior anomalies. They monitor various activities and create patterns for standard behavior. Once they notice abnormalities and suspicious behavior, UEBA systems inform IT administrators.
Machine learning is essential for UEBA systems. It helps them learn about typical behavior and create patterns, making anomaly detection a breeze.
✅Malware Analysis and Detection

Another application of machine learning in cybersecurity is malware analysis and detection. Malware is malicious software for causing disruption to a computer or server, leaking information, or gaining unauthorized access. It's harmful to servers and devices and can cause intentional damage.
Machine learning models are highly efficient in identifying and catching malware. They can detect new and transforming malware by analyzing its characteristics and code. Analyzing its behavior enables machine learning to detect even nearly undetectable malware and inform the security team of its existence.
✅Phishing Attack Detection
Phishing attacks occur by deceiving people into unknowingly installing malware on their devices. Usually, phishing attacks happen over emails and SMS.
Attackers imitate reputable institutions or trusted individuals, manipulating victims into downloading malware or asking for sensitive information. They rely on victims' trust in the persona they mimic to compel them to install malicious software unwittingly.
Machine learning models can be effective in detecting phishing attacks. They can analyze email content, including URLs and attachments, to determine if it's a phishing attempt. Moreover, they can learn user behavior and detect suspicious emails and phishing attacks through patterns.
✅Event Management Systems
Event management systems help recognize and resolve vulnerabilities and threats before they wreak havoc on devices. SIEM (Security Information and Event Management) tools are the most prevalent for threat protection in cybersecurity.
Cutting-edge event management systems use machine learning algorithms to spot patterns in user activity, network traffic, and other events and logs. The predictive aspect of machine learning lets them anticipate potential threats and help system administrators handle them.
Limitations of Machine Learning for Cybersecurity Applications
Machine learning models are among the mightiest tools for the future of cybersecurity, but they are imperfect and have specific disadvantages and limitations, although they constantly evolve and improve performance.
Let's explore some limitations of machine learning in cybersecurity.
Data Quality and Bias Issues
Machine learning models use extensive training data sets that help them spot and create patterns and learn to act accordingly. However, ML models get that data from humans. That means humans can decide which data ML algorithms will use. Data quality and bias issues are among the most notable limitations of machine learning in cybersecurity.
Adversarial Attacks

Adversarial attacks focus on machine learning models, providing defective input and causing them to malfunction. They cause the misinterpretation of given data or the implementation of malicious data into an ML model. That helps attackers exploit vulnerabilities.
Adversarial attacks are relatively new cyber threats, considering machine learning is a fairly new domain. Still, they can be highly dangerous, especially when attacking machine learning models for medical software or self-driving cars.
Resource Requirements and Scalability
Another significant challenge of machine learning is resource requirements and scalability. They present considerable limitations in machine learning models' training and implementation.
Training complex machine learning models requires high computational power. Considering vast data sets, your computer resources may be unable to support that. That also includes memory, storage, and training time.
Developing and training machine learning models also requires high costs. Scaling them comes with even higher expenses and other requirements.
[Strengthen Cybersecurity] How to Recover Data After a Cyberattack
Machine learning plays a critical role in cybersecurity. However, what happens if you've already suffered a cyberattack? Sometimes, cyberattacks result in data loss.
Don't worry if that happens because your data isn't lost forever, even deleted files. They become inaccessible and wait for new data to overwrite them, but they still exist on your computer.
Therefore, you need a data recovery tool like Wondershare Recoverit to restore deleted files. Wondershare Recoverit is a trusted data recovery solution for retrieving files in just a few clicks.
- Manages over 500 data loss situations, such as losing data in cyberattacks.
- The user-friendly interface allows you to recover data in just a few clicks.

Wondershare Recoverit can recover any data, including photos, videos, audio, emails, etc. It can restore corrupted or deleted files from any device that suffered a malware attack. It even has a patented Enhanced Recovery function to patch fragmented videos and images.
Follow these steps to recover lost files using Wondershare Recoverit:
- Install and launch Wondershare Recoverit on your computer.
- Go to Hard Drives and Locations. Click Start and select the storage with your lost files.

- The program will automatically scan the unit. You can pause or stop the process anytime.
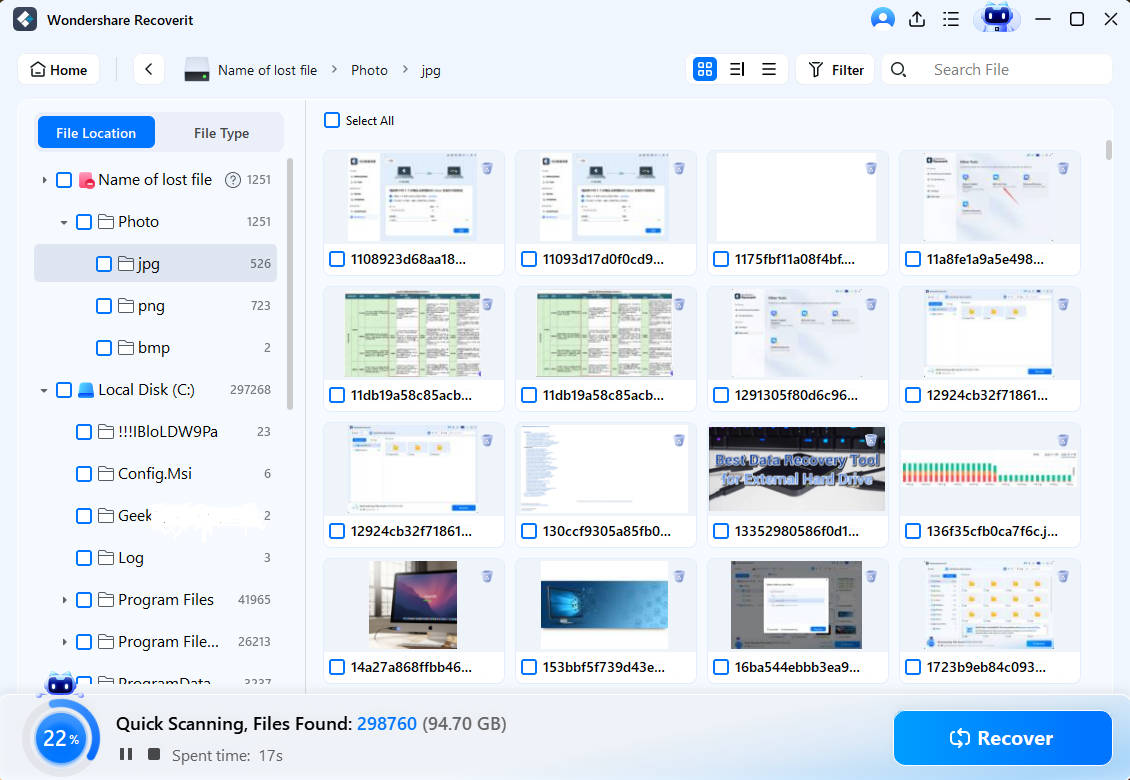
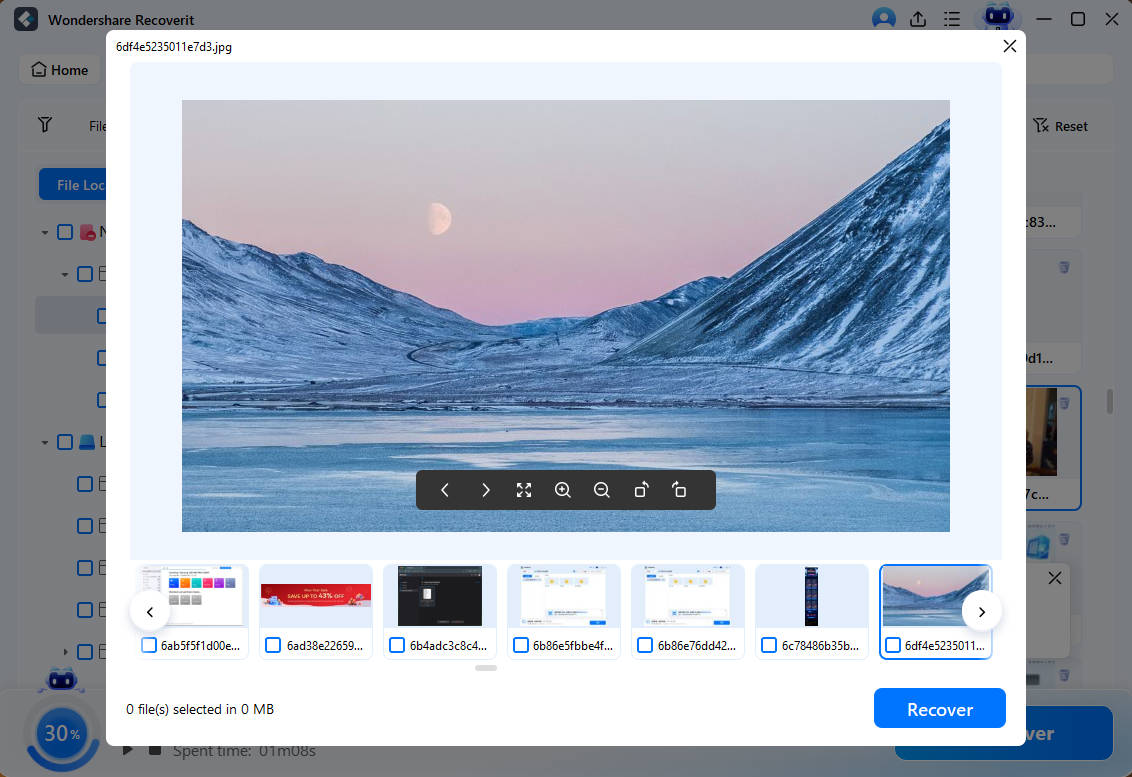
- After the scan, preview the files the program has found. Select them, click Recover, and save them to an external drive to protect them from malware.
Conclusion
Machine learning is a subfield of artificial intelligence that uses algorithms to create patterns. It's valuable in many cybersecurity domains, including predictive analysis, anomaly detection, and automated security operations. It plays a very important role in many prevalent cybersecurity applications, including malware analysis, phishing attack detection, UEBA systems, IDSs, and event management systems.
Machine learning still has limitations. The most notable challenges of ML models include data quality and bias issues, resource requirements and scalability, and adversarial attacks.
Due to the limitations of machine learning, it's better to have a backup plan to cope with the scenario where machine learning fails to stop cyberattacks. Wondershare Recoverit is exactly a tool you can trust to recover lost data.