It seems like your computer has been infected with a VHD virus.
Stop worrying. You'll get your files back. Now, read on to find out more about how to recognize a VHD virus, what to do if you have one, and how to avoid it in the future.
In this article
What Is a VHD File Virus
Briefly explained, a VHD file virus is a nasty type of ransomware that encrypts important files on your computer, changes their extension by adding a .vhd appendix, and leaves you a .txt message with a request for money in exchange for unlocking your files. Simple, yet effective.

Have a quick look at this malicious virus.
| Virus Name | VHD Virus |
| Threat Type | Ransomware, Files locker, Cryptovirus |
| Encrypted Files Extension | .vhd |
| Spreading Paths | Infected email attachments, torrent websites, malicious ads, etc. |
| Detection Names | Avast (Win32:Dh-A [Heur]), BitDefender (Gen:Variant.Graftor.717353), ESET-NOD32 (Win32/Filecoder.OBF), Full List Of Detections (VirusTotal), Kaspersky (Trojan-Ransom.Win32.Agent.awny) |
| Symptoms | Files get a .vhd extension and can't be opened; Ransom messages demand a payment (often in cryptocurrency). |
| Negative Consequences | A VHD virus is sometimes installed together with other types of malware, like a password-stealing Trojan; Victims are often left with their files locked after paying a ransom. |
Where VHD Viruses Come From
Some of the online places and files that viruses could come from include:
- Unofficial websites for downloading software, movies, music, etc.;
- Obscure third-party online tools and apps from unofficial stores;
- Malicious online ads and "too good to be true" pop-up messages;
- Unsolicited email with attachments sent from unknown addresses.

A VHD file virus can come from any of these places. When you download an infected file together with malicious software or attachments, the virus will pass to your computer in the form of a .exe, JavaScript, PDF, or RAR. You activate the virus by clicking on the file.
How to Check a VHD File Virus
If some of your files have just been renamed from file.pdf to file.pdf.vhd, we're sorry to inform you that your computer has been infected with a VHD file virus. If you look around, you'll be able to see a HowToDecrypt.txt file with a ransom request message similar to this one:
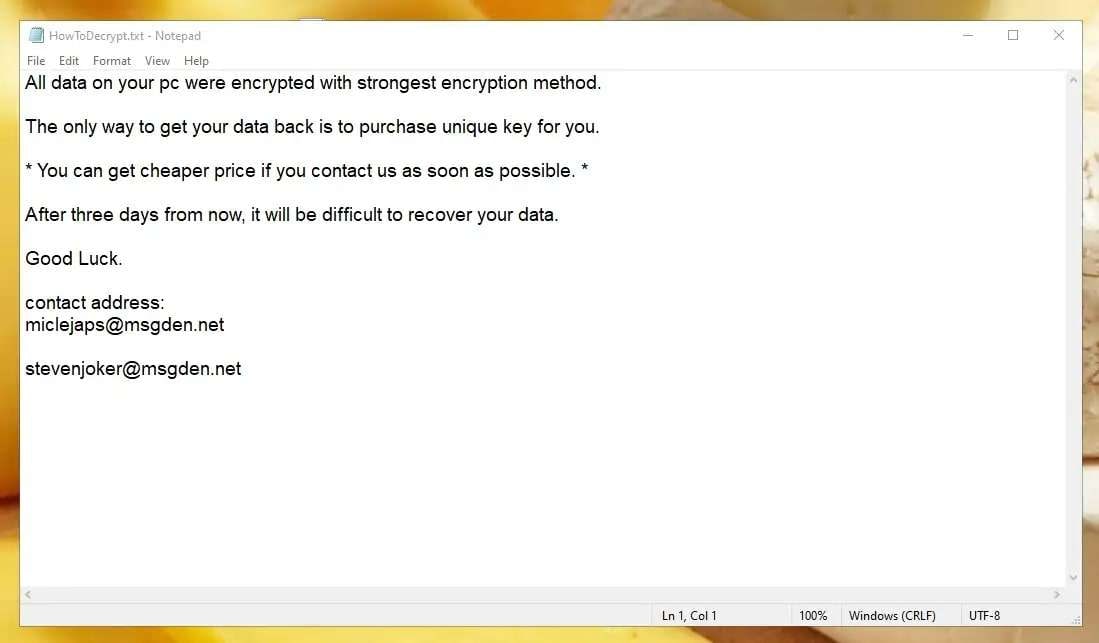
Sometimes, victims of VHD ransomware viruses will see pop-up messages instead of .txt files. Still, the content of the message is always somewhere along the lines of this request. You get a few days to email the virus developer and pay them for a description key.
Why does a VHD ransom message come with a ticking clock? One, because that gives you less time to try to decrypt the files yourself or contact the authorities. The second reason is that creating a sense of urgency gets you into panic mode, with no choice but to pay.
One of the signature marks of VHD file viruses is that criminals who use this type of ransomware almost always demand payment to be made in cryptocurrency like BitCoin.
Unfortunately, all this isn't the worst part of catching a VHD virus. As many victims have learned the hard way, cybercriminals are not a trustworthy bunch. As often as not, VHD victims don't receive a way to decrypt and access their files even after they pay a handsome ransom.
How to Mitigate the Damages of VHD File Viruses
Hopefully, it's not too late to tell you this – you should never pay ransom to cybercriminals. There's a good chance it won't buy you a description key, and you will lose your files and money. What should you do in this situation instead? Here's our step-by-step guide:
Report the Attack to the Authorities
Right now, you might be in panic mode and not realize you're not alone in this. Wherever you are in the world, the country you're in likely has the authoritative body/organization that deals with cybercriminals. You need to contact them and report the attack right away.
Here's a contact list for some of the most frequently attacked countries:
- USA – Internet Crime Complaint Center
- Canada – Cyber Centre
- United Kingdom – ActionFraud
- Ireland – An Garda Síochána
- The Netherlands – Politie
- Germany – Polizei
- France – CERT DFR is the French
- Italy – Polizia di Stato
- Spain – Policía Nacional
- Australia – ReportCyber
- New Zealand – CERT NZ
Stop the VHD Virus from Spreading
Like all viruses, a VHD virus can spread to other files and computers. Your first step after contacting the authorities is to stop this from happening. It is crucial to isolate the infection regardless of your environment – whether you're using a personal or work computer.
You first need to disconnect your computer from the internet to do this. It will put the infected computer in an offline quarantine zone, where it can't infect computers and devices on the same network.
If you don't know how to disable the internet connection, here's a quick guide:
- Go to the Control Panel > Network and Internet and search for Network and Sharing Center.
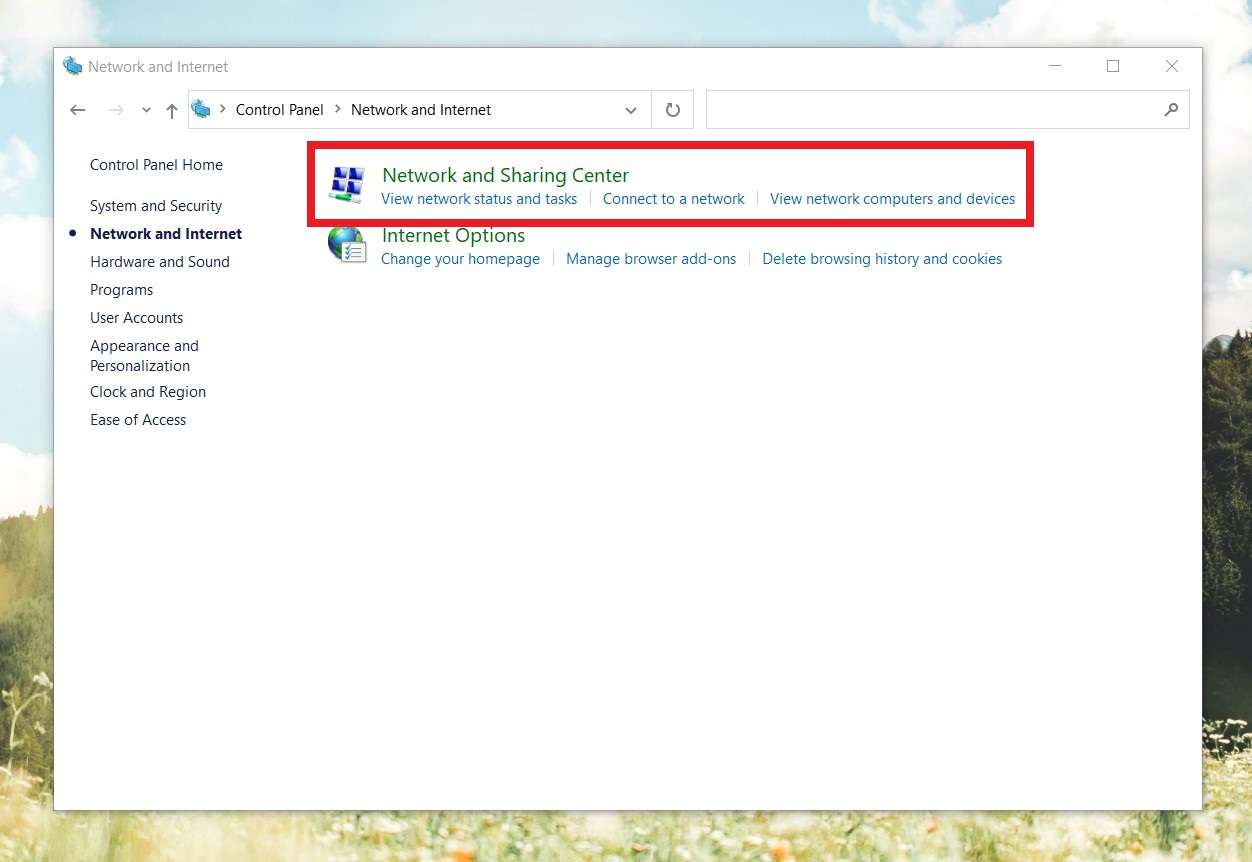
- In the sidebar on the left, select the Change adapter settings tab.
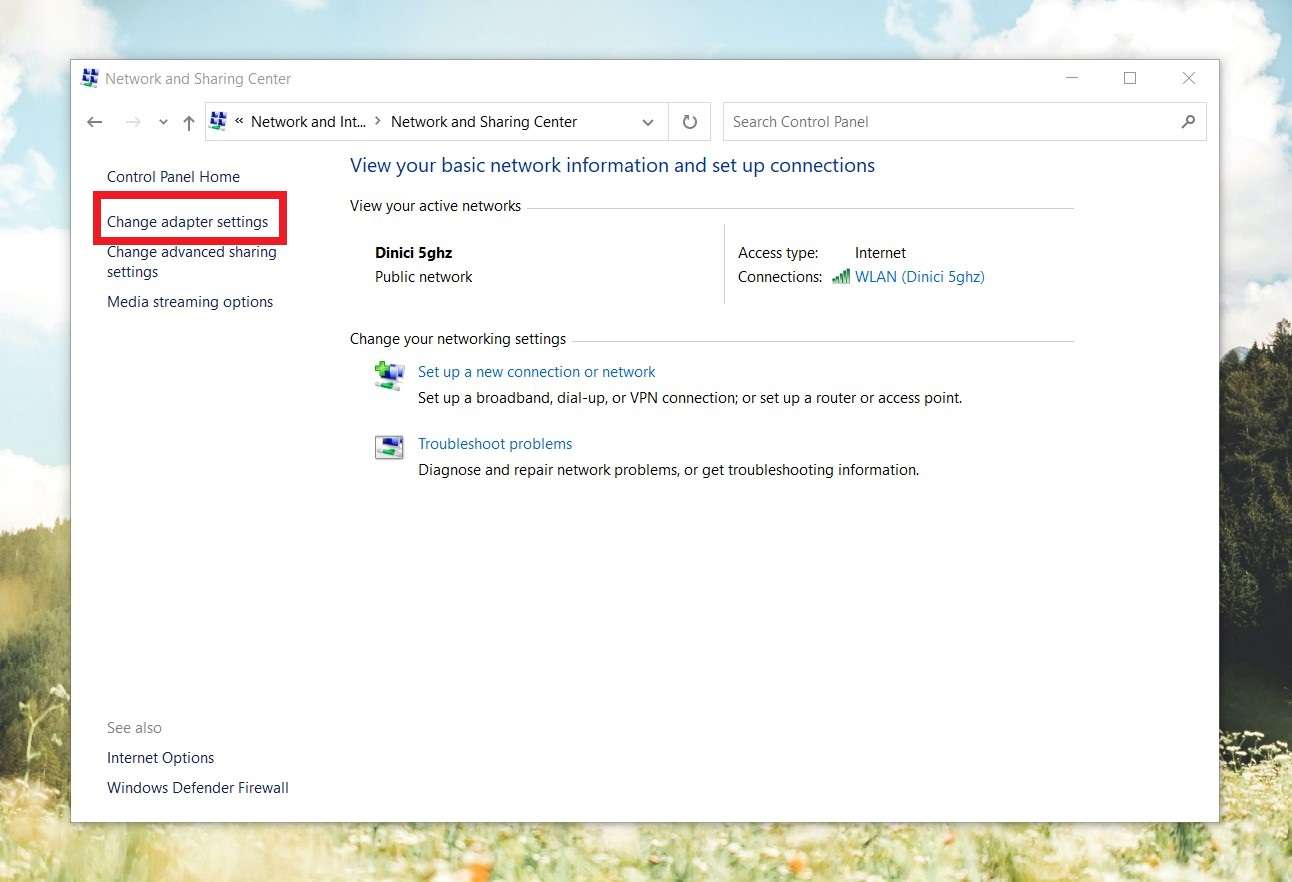
- Right-click on each internet connection point and click Disable.
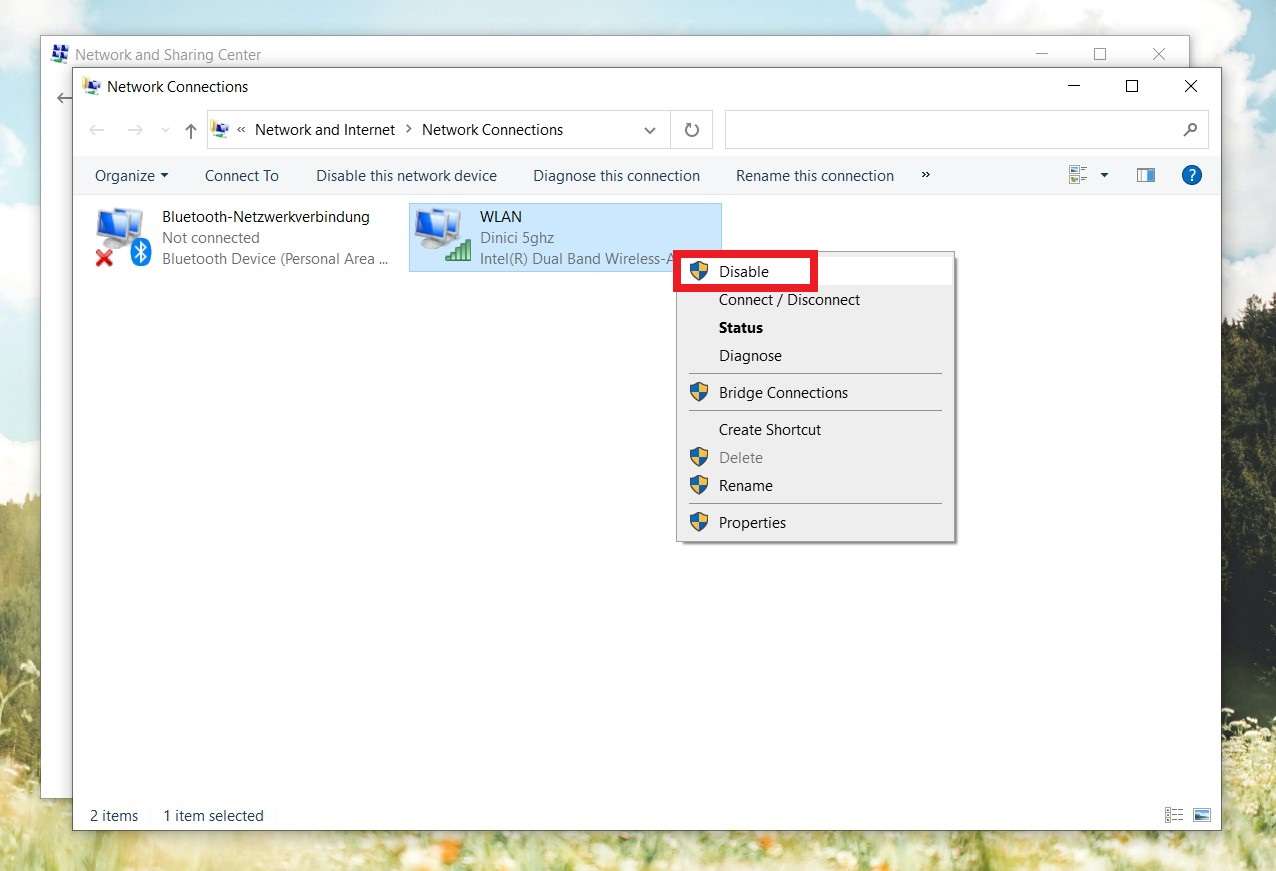
After you do this, you need to make sure that the VHD file virus is completely sealed off inside of the infected computer. So, if you have devices plugged into your computer, plug them off. That applies to everything from portable disks and storage devices to keyboard and mouse.
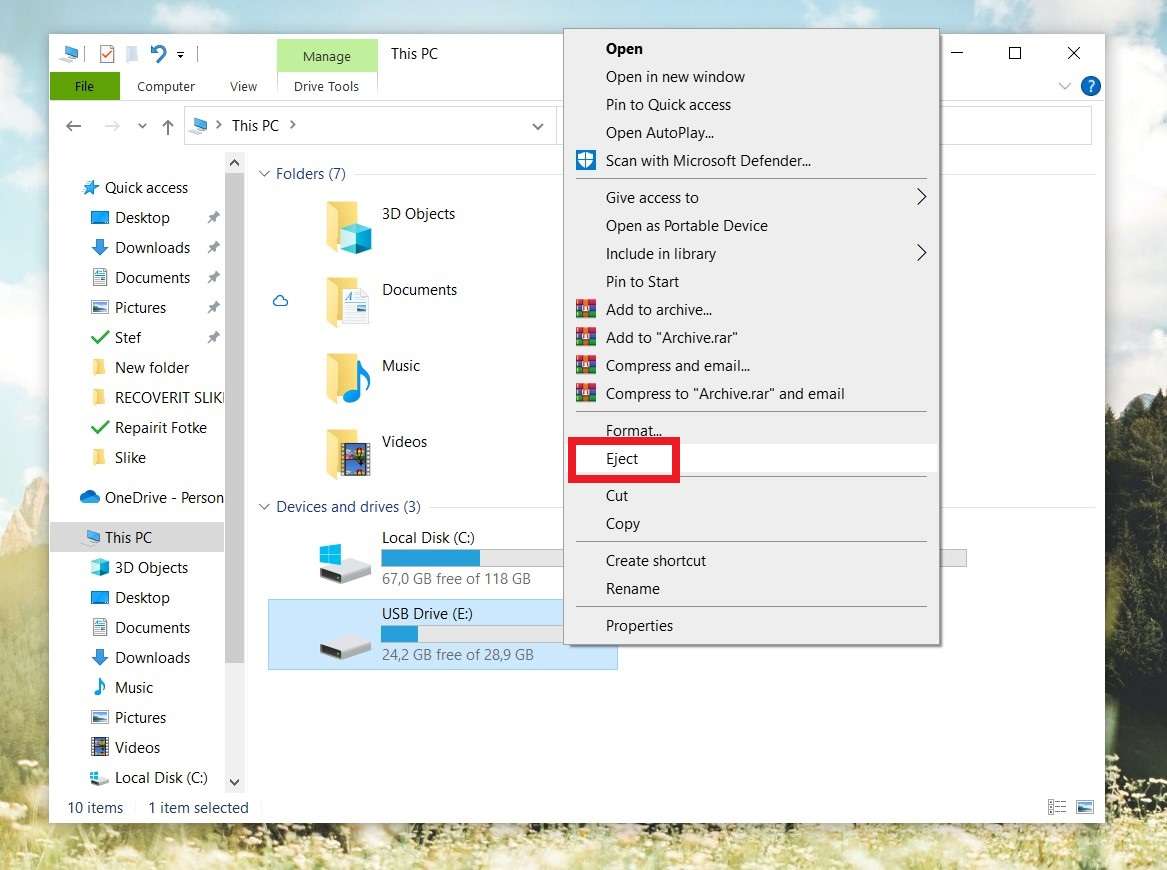
The proper way to unplug the device from the computer is from My Computer. Locate the device you want to disconnect. Right-click the icon and then select the Eject option.
Use a VHD File Virus Remover Tool
Once your VHD file virus is safely contained, it's time to remove it. You'll need a specialized malware remover tool for this. Many anti-virus and anti-malware software solutions have these tools on their feature lists, so there's a good chance you already have one. Go check right now.
If your anti-virus doesn't have a special feature for removing malware from your computer, you'll need to get one. In our opinion, these are two of the best VHD virus file removers:
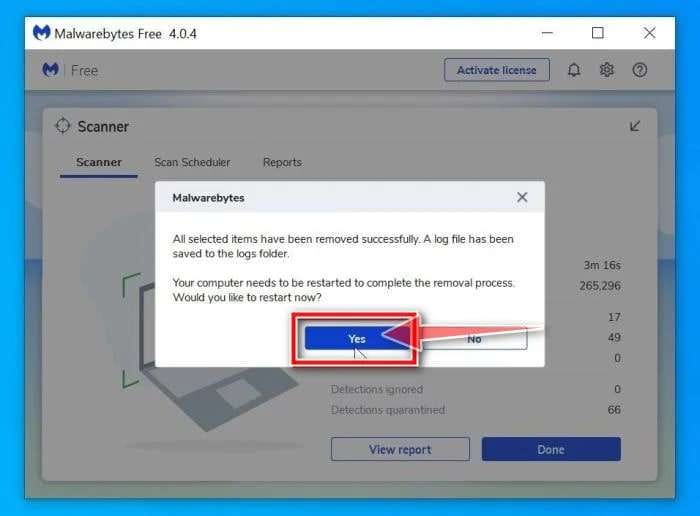
Malwarebytes
Price: From $59.99 annually
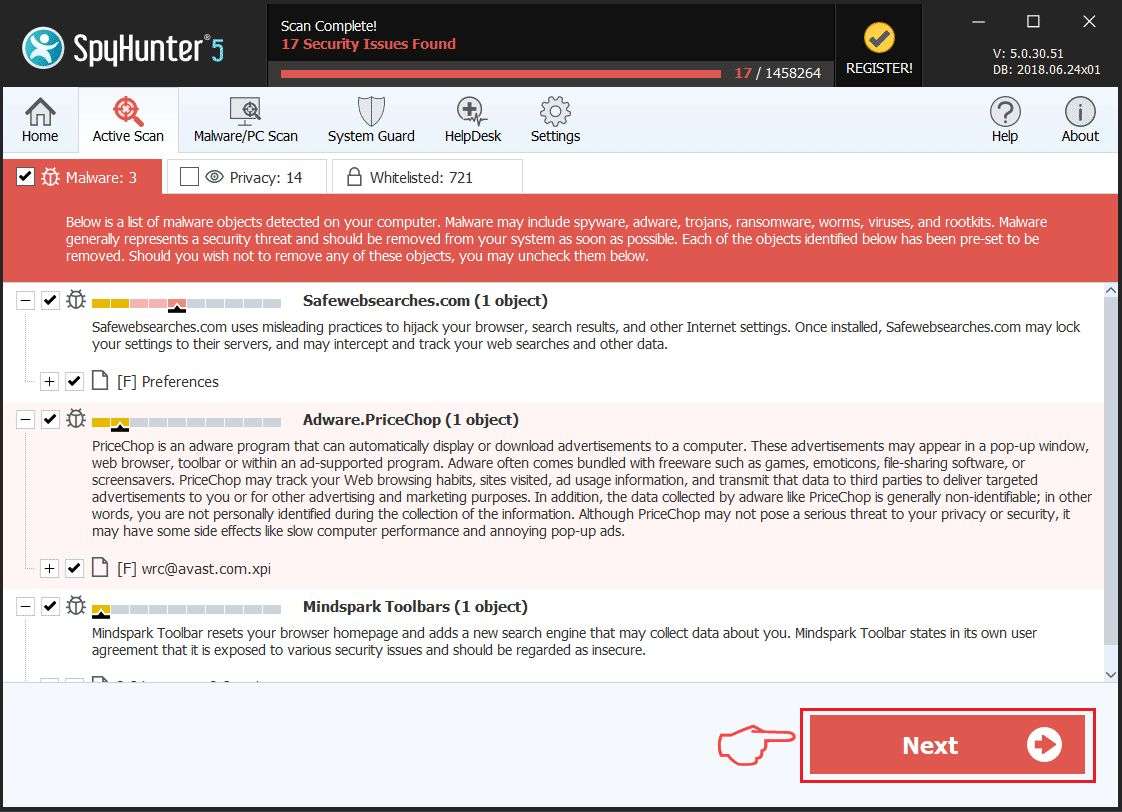
SpyHunter 5
Price: From $42 for 3 months
After downloading and installing either of these anti-malware tools, they will scan your computer to locate the threat. However, while Malwarebytes does most of the job itself – you only need to click Yes to restart your computer in the end, as SpyHunter 5 demands an on-hand approach.
Even though it's not as user-friendly as Malwarebytes, SpyHunter 5 is a powerful tool that gets the job done. In most cases, either one of these tools will be able to help you out.
Recover Files with a Data Recovery Tool
There are two parts to VHD file virus recovery, and we've just completed the first one. Now that you have removed the VHD virus from your computer, it's time for you to get your encrypted files back. You can do that with the help of a professional data recovery tool like Wondershare Recoverit.
It's a go-to solution for many data loss scenarios, including various virus infections. It boasts a recovery rate of 98% in retrieving virtually all file formats.
Follow these steps to return your infected files using this app:
- Download Wondershare Recoverit from the official site and install it on your computer.
- Select a computer location that you want to scan for files. For example, C:.

- Track the progress while waiting for Wondershare Recoverit to dig up recoverable files.
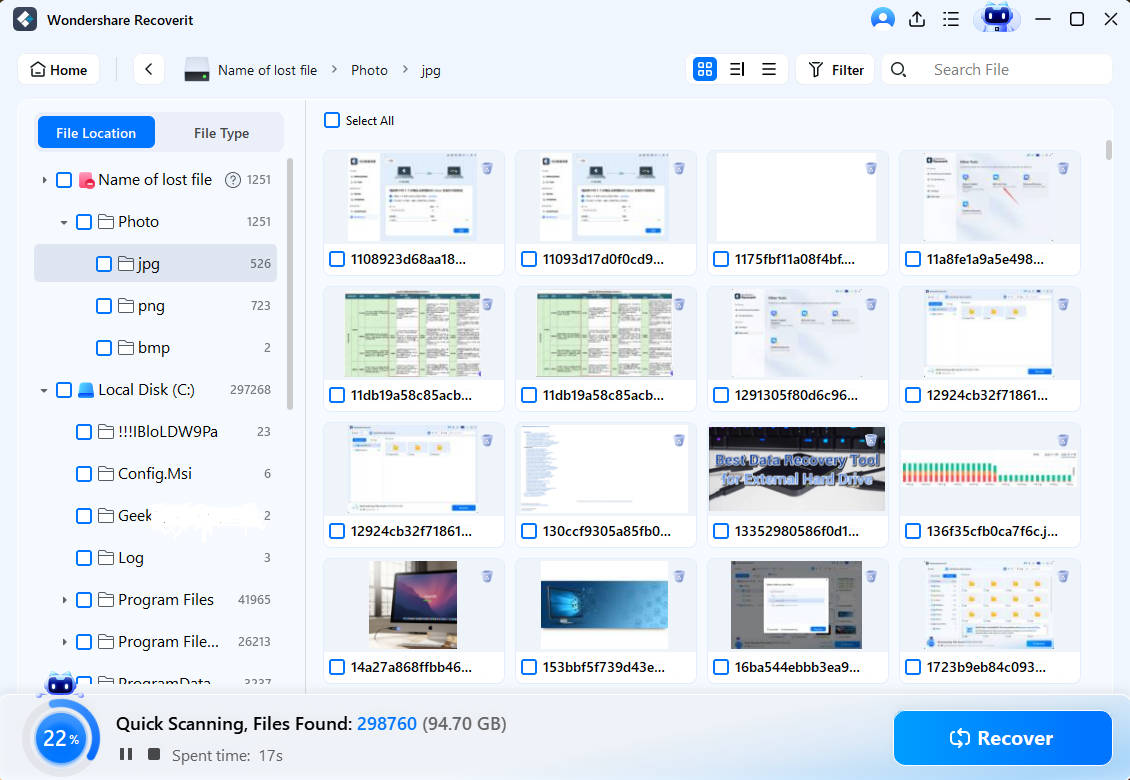
- Filter through scan results using file type, size, timestamp, or keyword.
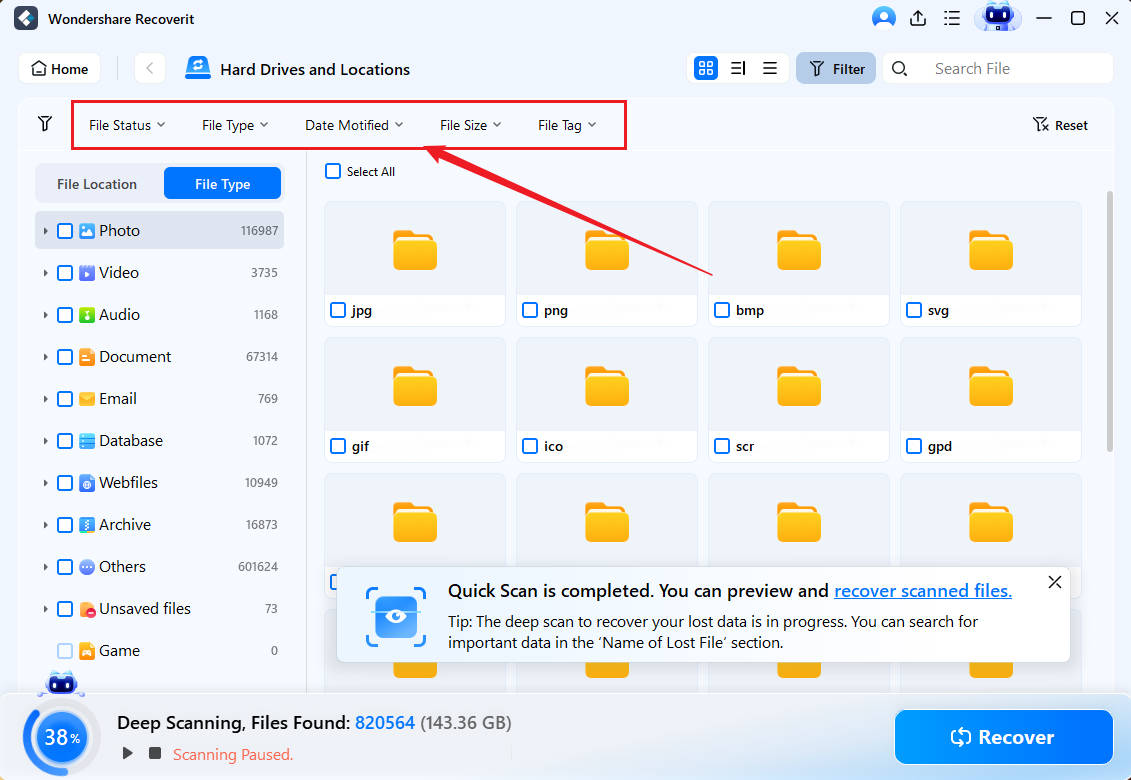
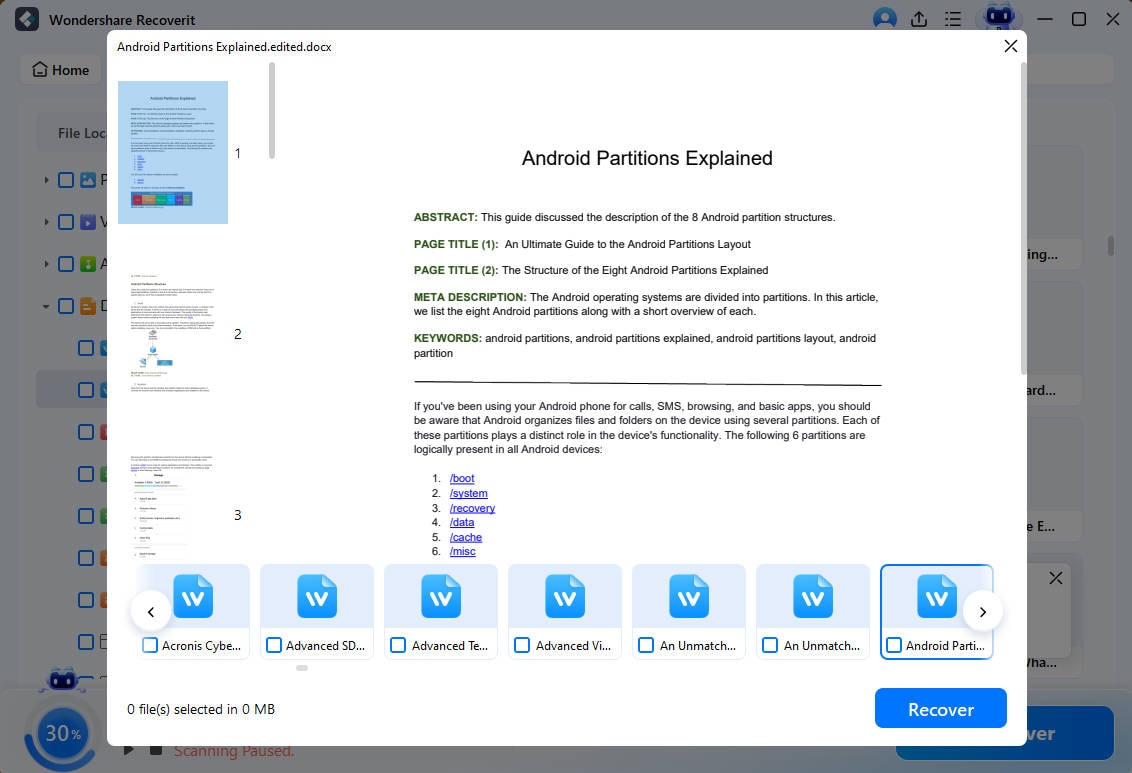
- Preview the files you want to retrieve and click Recover if all is OK.
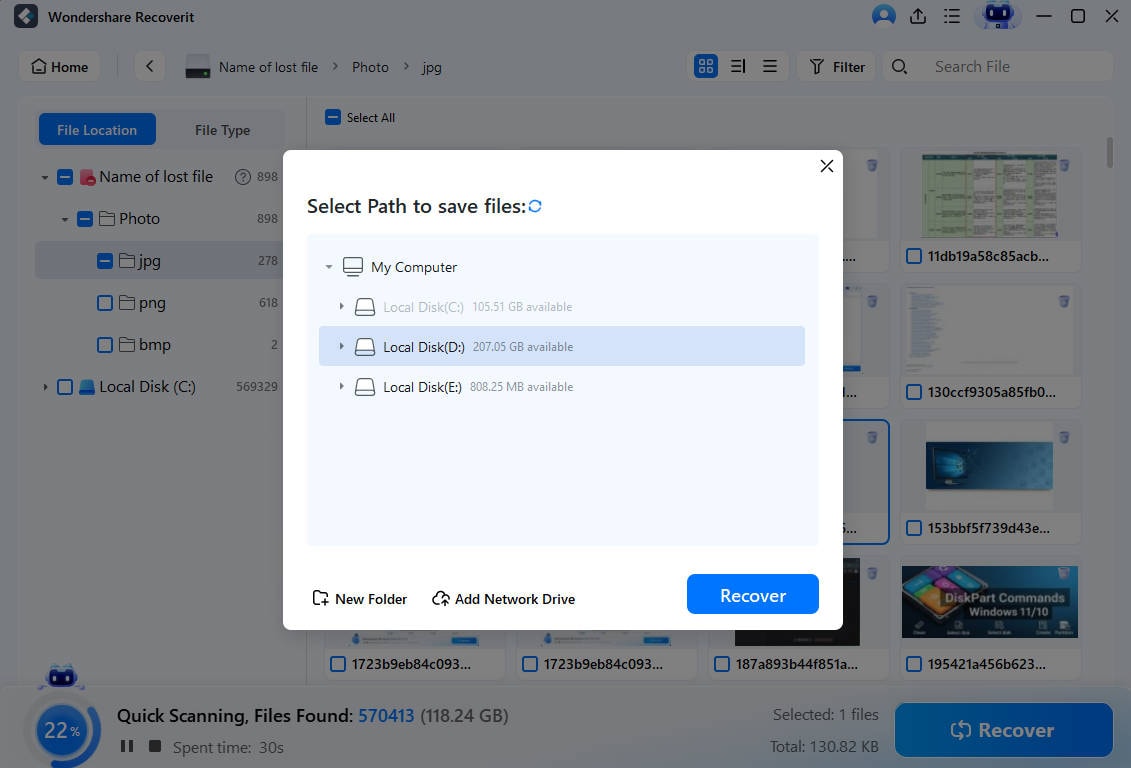
- If you want to save multiple files, select them and then click Recover.
- Find a place to store recovered files on your computer and click Save.
Back Up Important Files in the Future

Backing up your files cannot fend off dangerous malware attacks such as a VHD file virus but can save you the trouble of data recovery. A backup helps restore files to a state before they've been decrypted, but it doesn't eradicate the VHD virus altogether.
It means you'd still have to remove the VHD file virus from your computer even if you had a backup. Restoring files from backup will remove the virus from the restored files. The virus will likely still be in your computer's system and will infect more files.
That said, backups are super important as they prevent catastrophic data loss.
If you don't mind backing up your files manually, you should copy them to an external storage device that you can unplug and store somewhere safe. However, if you can't do this regularly, it's better to set up automated backups using your computer's native solution or cloud.
Bonus: Start Practicing Cybersecurity Right Now

In addition to backing up your files, what else can you do to avoid becoming a victim of a VHD virus or similar attacks involving ransomware or malware in general? Practice safety.
Here's a little checklist to keep you safe from this virus:
- Install a reliable anti-ransom tool and update it regularly.
- Update your computer as soon as the new patches are out.
- Consider encrypting sensitive files with BitLocker or FileVault.
- Don't visit shady and questionable websites with weird URLs.
- Don't click on suspicious pop-ups, flashy ads, and hyperImage names.
- Don't open unsolicited email attachments from strangers.
- Don't download files until you've scanned them for viruses.
Conclusion
A VHD virus is easy to recognize by a .vhd file extension and a ransom message demanding money (often in cryptocurrency) in exchange for unlocking your files. Generally, it is much easier to avoid a VHD file virus than to get rid of it. Some of the most effective ways to dodge a VHD file virus are using a trusty anti-ransom tool, keeping your PC up-to-date, encrypting sensitive files, and practicing online safety.
However, if you get unlucky and catch one anyway, equip yourself with a trustworthy ransomware remover like Malwarebytes and Spy Hunters 5 and a data recovery tool like Recoverit.
FAQ
-
Can I get in trouble for paying a VHD virus ransom?
Legally, you can't be prosecuted for paying a ransom to cybercriminals. However, you have an ethical responsibility to report cybercriminals to the authorities and not support criminals financially, albeit against your will. You should do everything in your power to avoid paying a VHD ransom. -
Can criminals use VHD virus attacks to steal my data?
Yes, getting your files infected and locked by the VHD file virus means criminals now have your data. Sometimes, cybercriminals behind this type of virus attack threaten to release the victim's data online unless a ransom is paid. -
What is the most common way to get infected with ransomware?
The easiest and most frequent way computer users become victims of ransomware is through email phishing. Email phishing is a type of online scam involving an electronic message that was made to appear as if it was sent from a trustworthy source, such as a bank or post office. These messages include a malicious attachment or download Image name, tempting the victim to click and thus download ransomware.