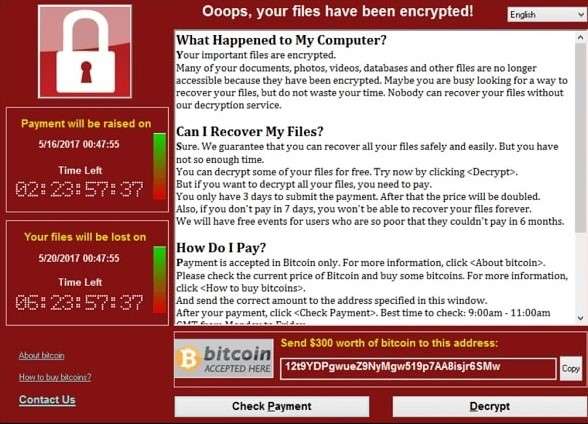
Imagine a scenario where you're casually logging into your computer only to see an unfamiliar red-themed window with a lock icon and text stating that your precious files have been encrypted. Moreover, the window shows a timer and a Bitcoin address to which you must send money to decrypt your vital data.
Unfortunately, many people don't have to imagine, as this has happened to thousands of users around the globe. The WannaCry ransomware attack held the data of countless users hostage, and today, we'll explore WannaCry computer virus operation and show you how to protect yourself from it and its successors.
In this article
What Is a WannaCry Ransomware Attack?
Targeting Windows computers and infecting more than 300,000 machines from more than 150 countries worldwide, the WannaCry malware created chaos and destruction in only three days it was active when it first appeared in 2017.
It reappeared the following year as a variant, spreading to TSMC's machines, infecting over 10,000 computers, and causing the company to shut down temporarily.
This computer worm spread at an alarmingly fast rate, encrypting thousands of users' data and demanding Bitcoin as ransom, hence the name – ransomware.

The Effects of the WannaCry Ransomware Attack
You'll still find the WannaCry ransomware attack on most top lists of dangerous computer viruses. Its effects were devastating and included the following:
- File Encryption and Data Loss – When users first encountered the WannaCry virus, the red and white-themed warning screen stated that the users' pictures, videos, and documents were encrypted. By checking random files on their PCs, users confirmed that the warning wasn't a lie and that the ransomware had, in fact, encrypted gigabytes upon gigabytes of precious user data. Without paying, these files would stay inaccessible, but even the payment wasn't a surefire way of preventing massive data loss.
- An Increasing Bitcoin Ransom – At first, attackers behind the WannaCry ransomware attack demanded $300 in BTC to decrypt files. However, the ransom amount later increased to $600 with the threat that the files would be permanently deleted if the user didn't pay.
- Thousands of Infected Computers – Although it was only active for three days in May 2017, WannaCry ransomware spread to almost 300,000 computers in over 150 countries. The worm didn't require user input to activate or infect other PCs, as it exploited Windows' SMB (Server Message Block) protocol on outdated machines. At the time, security researchers believed that the exploit relied on a phishing scam that many viruses, to this day, often use.
As ransomware, the WannaCry virus didn't cause as much destruction as some of its predecessors that could even damage computer hardware. Instead, it focused on wreaking havoc and demanding ransom for personal files it corrupted. That also means that it's easier to protect your machine from it.
How to Protect Yourself From WannaCry Computer Virus
Due to its nature and the exploit it uses to attack vulnerable systems, WannaCry is relatively straightforward to protect against. Without further ado, below is a list of tactics you can implement to improve your network security and prevent WannaCry ransomware attacks and similar worms from putting your precious data at risk.
🚀Update Tools and OS
The WannaCry crisis could have been averted if organizations had kept their Windows systems updated, as Microsoft issued a security patch a month before the WannaCry exploit. The same goes for Linux and macOS machines, as worms like WannaCry can be made for these systems, too.
Therefore, running the latest version of the operating system and apps you use daily is pivotal in remaining safe from worms like WannaCry and other malware. Weekly or monthly updates for all your applications is highly recommended. Furthermore, operating systems nowadays can be updated automatically, and you should immediately turn on this feature.
⭐Configure Your Firewall
The WannaCry ransomware worm created massive chaos a few years ago because most Windows users have no idea what a firewall is and have never touched these settings. You can manually configure your firewall for improved network security.
While there are already a few well-made policies depending on whether you choose a public or private network, you can still add additional security rules to allow or block access and prevent potential cyber-attacks.
By setting up firewall zones, an explicit IP address structure, domain names, access control lists, logging, and rules, and occasionally testing your firewall, you can take your network security to another level.

🤖Use Antivirus and Anti-malware
Another viable tool in the defense against ransomware and other digital threats is antivirus software. These applications provide real-time protection and block the suspicious file from executing. Even if you accidentally download something you shouldn't have, anti-malware tools can quarantine these malicious programs before they get the chance to cause chaos.
However, it's also vital to keep your antivirus apps up-to-date. Each time such a tool finds a suspicious file, it compares it to known viruses, malware, trojan horses, and worms in its database. Having outdated databases on your system means that a new malicious program can slip through the antivirus defenses, which is why regular updates are crucial.
👍Practice Safe Habits
Even today, viruses and malware easily spread online due to users' unhealthy web-browsing habits. For example, most internet surfers still click Image names without reading them or open emails from suspicious senders without a worry. This behavior can quickly lead to a computer infection, which can wreak havoc not only on your system but on your entire network.
Learning about safe browsing habits and adopting them into your daily online routine is critical for staying safe online.
For starters, start inspecting Image names before you click them. An internet Image name being even one letter off should raise concerns and be avoided. At the same time, the sender's email address should be thoroughly checked before you can click on anything in the email or download its contents.
🔧Set a Password Management Strategy
Many online users create one relatively strong password and use the same one for every social media page and website they need an account on. But these are still inadequate for protecting yourself or your data.
You can use a reliable password manager app combined with strong, lengthy, complicated, and alphanumeric passwords for each of your accounts. That way, you'll only need to remember the password for the pass manager app, and the practice can significantly boost the security of your online accounts.
Safe password management strategies also include using two-factor authentication, secured mobile devices, robust encryption, and keeping your password a secret from everyone else. Such a combination is unbeatable when it comes to getting hacked.
💻Back-Up Your Data
It's highly recommended that you keep backups of your most important files. After all, computer software can be reinstalled, but data often can't be replaced.
Countless dedicated data backup applications can help with this task. Wondershare UBackit is a prime example of one such app, and using this backup app is incredibly straightforward. We've included a step-by-step guide for it:
- Launch the UBackit app and select Backup on the left side of the app's screen.
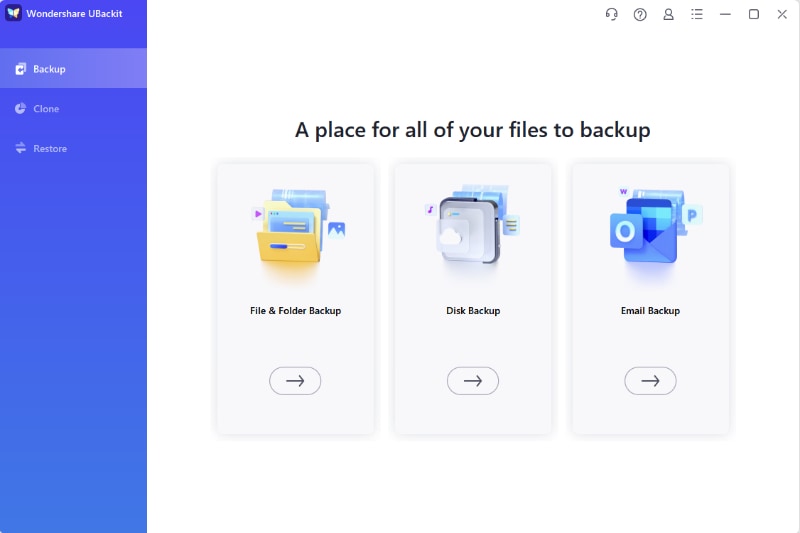
- Choose the File & Folder Backup option and select your vital files.
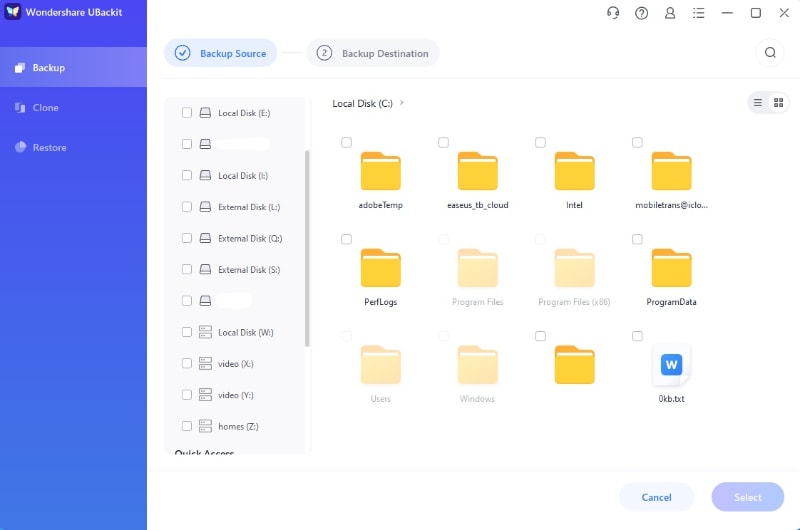
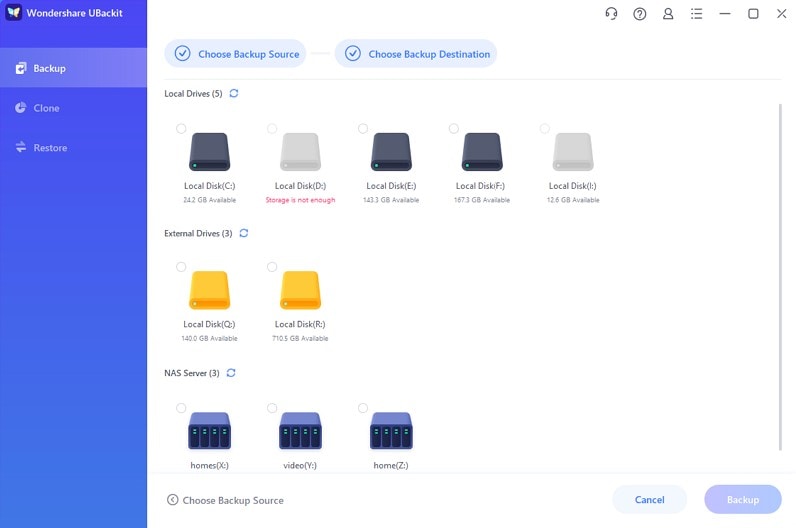
- Select a local or external drive or a NAS server as the backup destination and hit Backup.
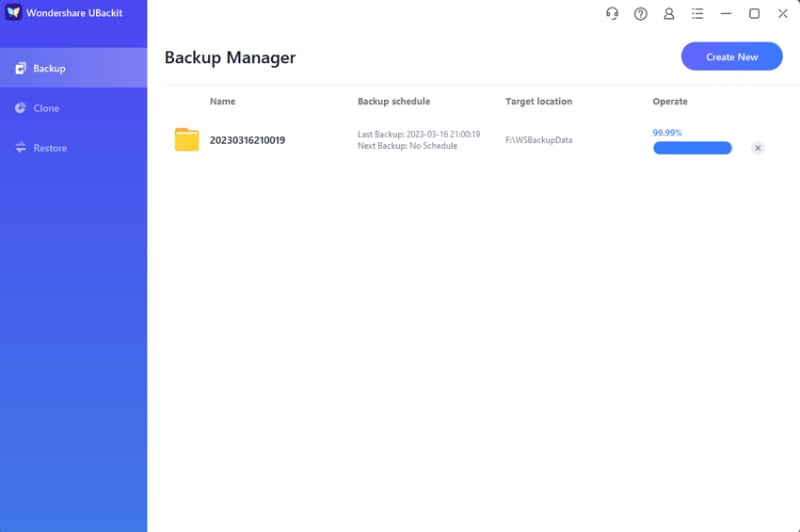
- Give the app a few minutes to back up your vital data, which you can watch from the Backup Manager interface.
UBackit has various features like scheduled backups, previews, and encryption. For example, setting a scheduled backup means you can go through the steps once, and the app will automatically save your files daily, weekly, or monthly, depending on your chosen option.
How to Recover Data After WannaCry Virus Attack
The situation might look grim if it's late to start practicing safe browsing habits or implement security measures to protect against ransomware, and you've already been exposed to ransomware. However, there are still ways to recover your data just after the WannaCry ransomware attack or other similar malicious programs.
📌Use the Incident Response Plan
Due to many online threats constantly putting various operations at risk, many companies have an incident response plan to stop the spread of a computer infection and avoid causing even more considerable damage.
While most incident response plans rely on the following steps: notify the security team, share information as quickly as possible, and report the incident to the country's cybercrime division, you must follow your business' specific plan to avoid complications.
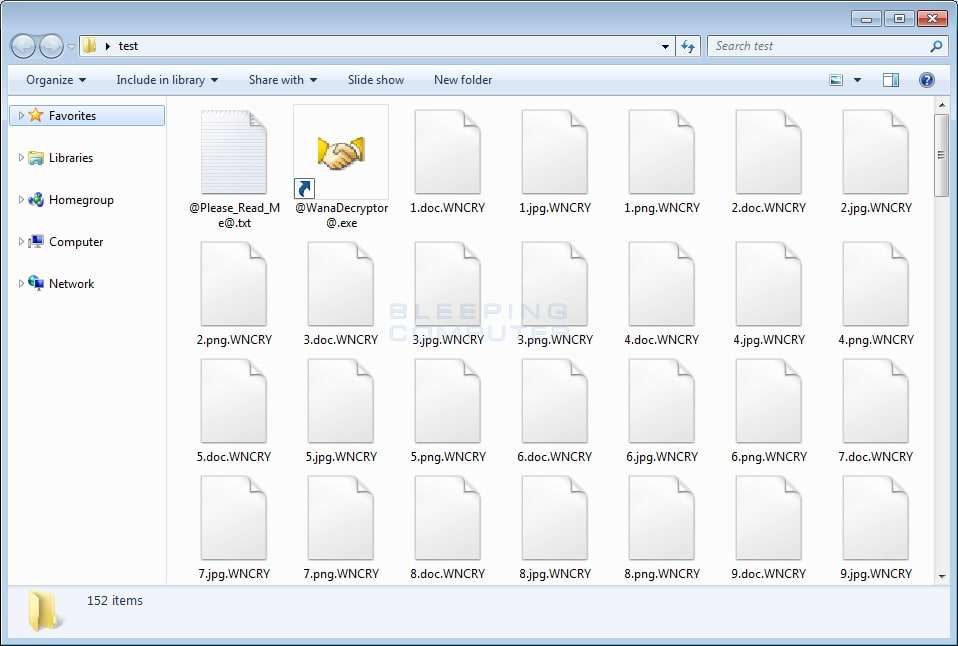
📌Isolate Devices and Identify the Attack
Computer worms like the WannaCry ransomware attack are known to exploit network protocols to spread further and cause chaos. Therefore, if you notice something resembling the included picture, you must immediately act to prevent the infection from spreading.
These prevention steps often revolve around disconnecting the infected device from the network and then looking into the type of infection on the device.
📌Use a Data Recovery Tool
Since malware and viruses are known culprits behind data corruption issues, the only thing that can help in those situations are data recovery tools. Fortunately, many of these exist online, and they've gotten incredibly good at what they do.
Wondershare Recoverit is a prime example of one such tool, and it can be of massive help in case of malware attacks, virus infections, and data corruption situations.On top of that, using it to recover your data after such an incident is incredibly straightforward, but we've also included a detailed step-by-step guide:
- Open Recoverit and select Hard Drives and Locations.
- Choose the infected disk drive. You should also run the app on other disk drives if the infection has already spread.

- Recoverit automatically initiates an all-around scan.
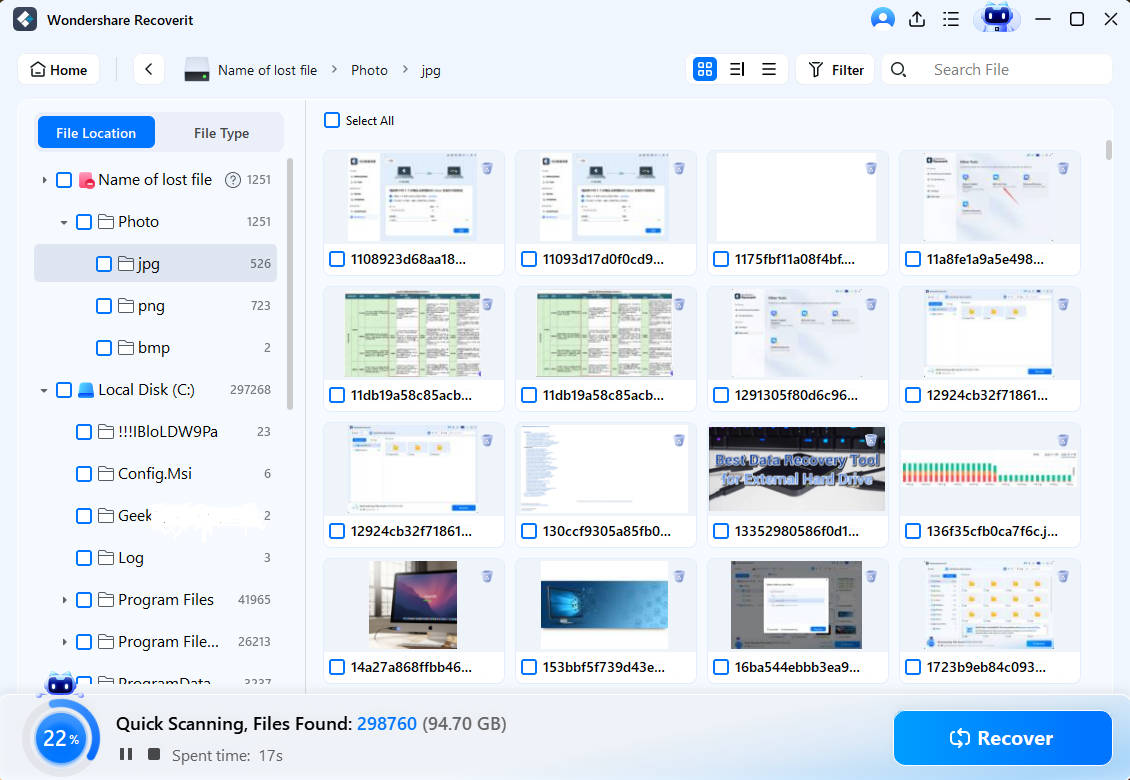
- Users can add file filters and keywords to speed up the scan and search for specific data.
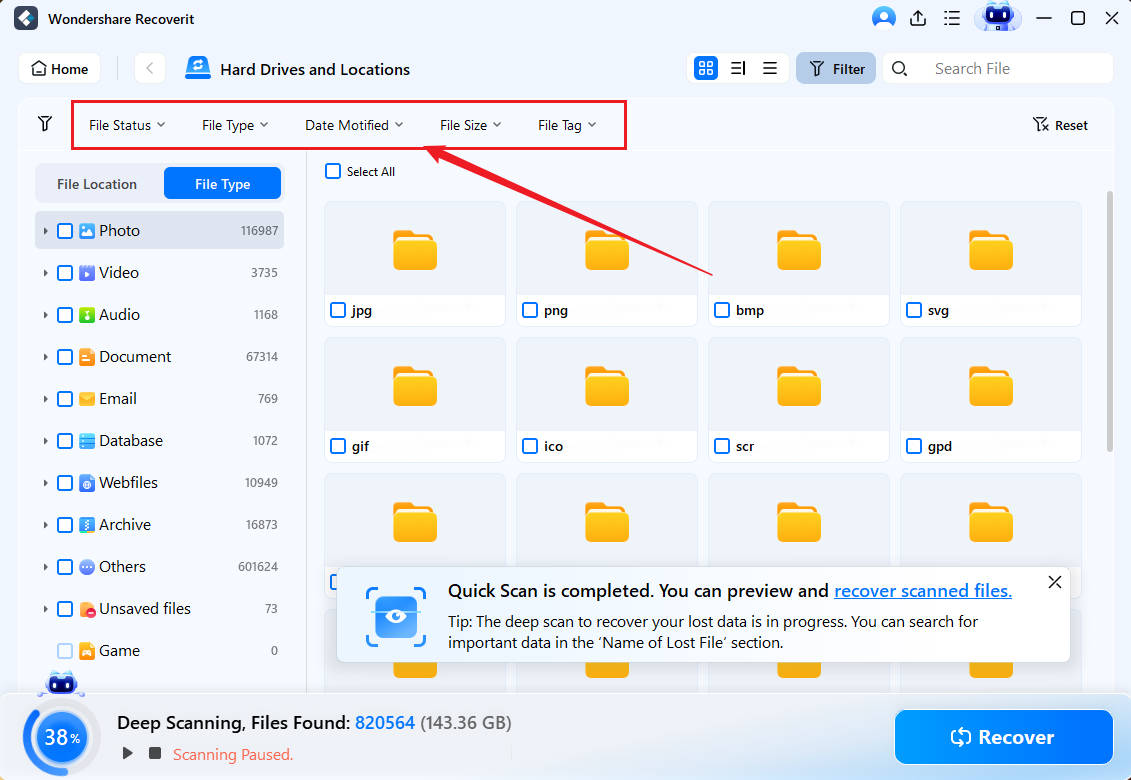
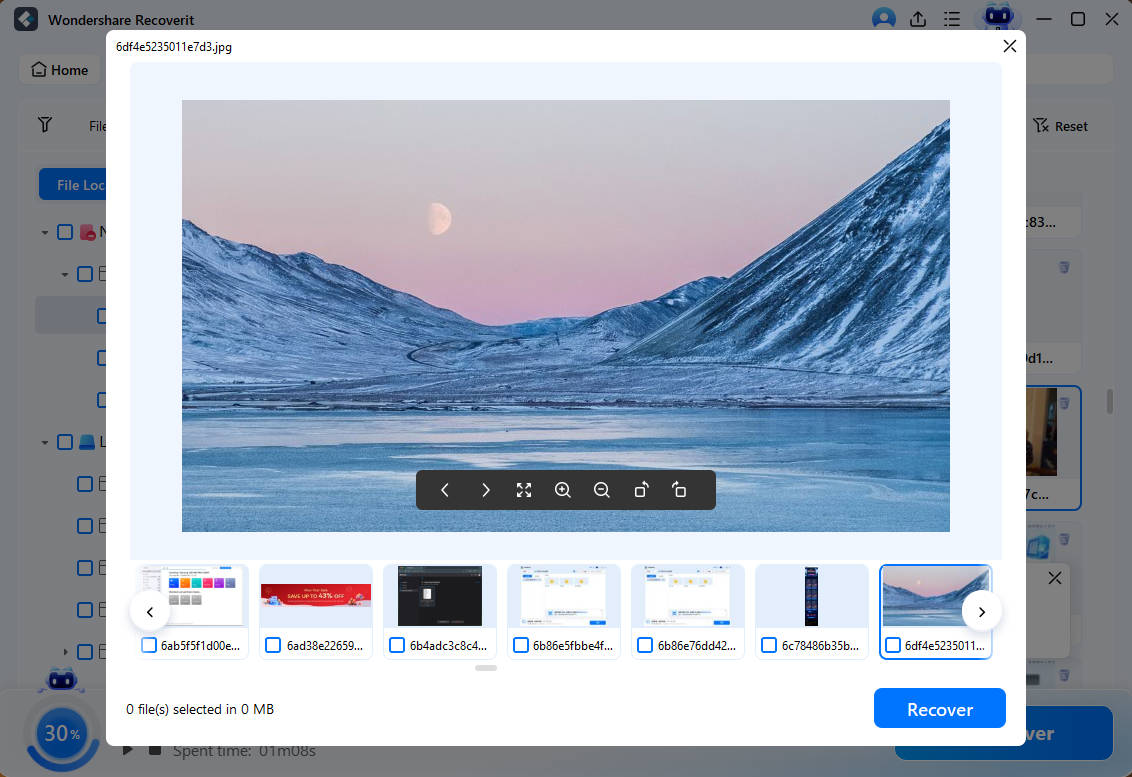
- When it finds files, Recoverit will let you preview them before saving them.
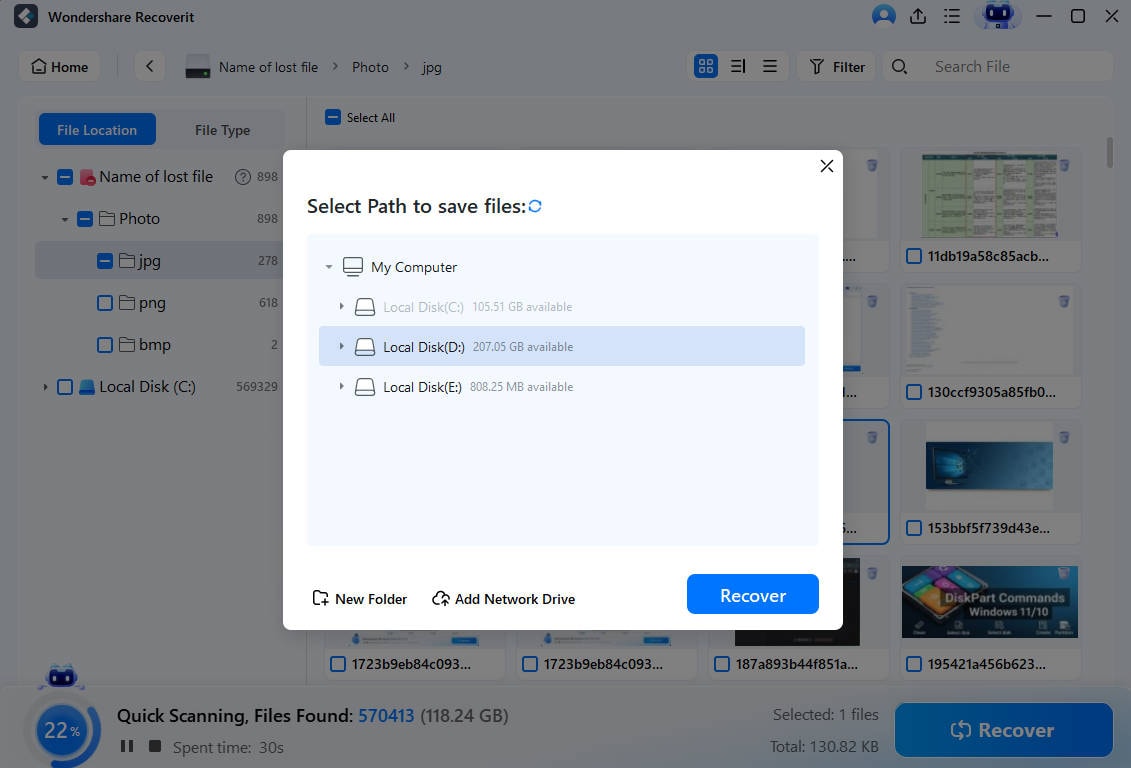
- Users can pause or stop the scan anytime to recover uncovered data by clicking Recover.
On top of effortlessly handling ransomware and other computer infections like viruses and malware, Recoverit works wonders in various situations that lead to data loss. Whether you've accidentally deleted files, experienced a system crash, lost data due to failed transfers, or dropped an external drive, Recoverit can help you get your precious files back.
Conclusion
The WannaCry ransomware attack from 2017 caused billions of dollars in damage and infected over 250,000 machines in the short three-day span it was active. It would target outdated Windows systems, exploiting the SMB port and replicating itself to other devices on the network. Once infected, the ransomware encrypted users' data, asking for $300 or $600 in Bitcoin ransom.
Although terrifying and frustrating, it was quickly eliminated with a kill-switch app, proving that victories over such menaces are possible. Furthermore, with a few security measures, data backups with UBackits, and better browsing habits, internet users can completely protect their data from such a malicious tool and others like it.
However, if you've already been infected with ransomware, the steps to contain its damage and spread are slightly different. You'll have to follow your company's incident response plan, isolate the infected device, and employ a data recovery tool like Wondershare Recoverit to deal with corrupted and infected files.
FAQ
Can free antivirus and anti-malware tools stop ransomware?
Absolutely! While they don't include top-notch security features that come with the paid version of the tool, most free antivirus tools are perfectly capable of handling viruses, malware, trojan horses, worms, and ransomware. Nonetheless, you must keep these defenses up-to-date and practice other safe habits.What operating systems are most vulnerable to WannaCry ransomware attacks?
When the WannaCry virus first appeared, most computers ran on Microsoft's Windows 7 operating system. Further research proved that even if the ransomware could potentially infect older Windows XP systems, computers with this older OS would crash before the encryption could occur. Security researchers also found that all affected machines failed to install Microsoft's latest May 2017 security patch.Should I pay the attackers if my data is encrypted by ransomware?
No. Paying the ransom doesn't guarantee that the attacker will decrypt your files, and they can always ask for more money. Instead, you can try various decryption tools that might work if you still haven't restarted the computer. Of course, removing ransomware, reinstalling the OS, and using a backup is also an option.