DDoS attacks can disrupt your operations or business in the bImage name of an eye. Even though they have been around for a long time, they are still a preferred option for many hackers. Why? DDoS attacks will always be problematic, especially when individuals and organizations don't set the proper protection measures.
There are also many different types of DDoS attacks, and they're constantly evolving. In some cases, these attacks can be unmistakable, but they can get very sophisticated and cause severe damage to your website. You must learn to protect yourself against them and prevent the damage.
Before learning what to do if you get DDoS-ed, let's explain what DDoS attack is and how it works.
In this article
What Is a DDoS Attack?
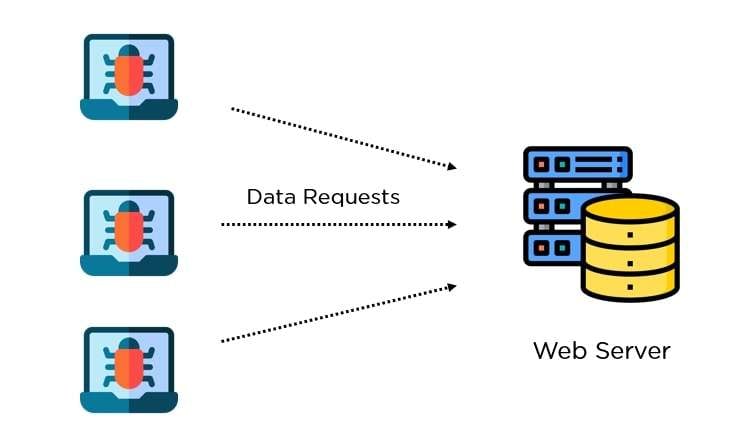
DDoS stands for Distributed Denial of Service. This attack involves attackers attempting to flood a server with high traffic volumes, disabling site or service access.
There are different motivations for carrying out DDoS attacks, and they can come from both organizations and individuals. Some are simply unsatisfied individuals who want to make a statement, showcase their dissatisfaction, or get "revenge" on individuals or organizations.
In addition, financial motivation is usually behind large-scale DDoS attacks, which look to disrupt businesses while asking for money to stop the attacks. DDoS attacks are growing, targeting even some of the largest companies, including the attack on Amazon Web Services in 2020.
How a DDoS Attack Works
Distributed Denial of Services attacks are a subcategory of general Denial of Service attacks. DDoS attacks use a single internet connection to bombard a network with multiple fake requests and try to exploit any vulnerabilities.
DDoS attacks have a far larger scale of requests and can use thousands of devices to achieve their goal. The increase in the volume makes it more challenging to deal with the attack.
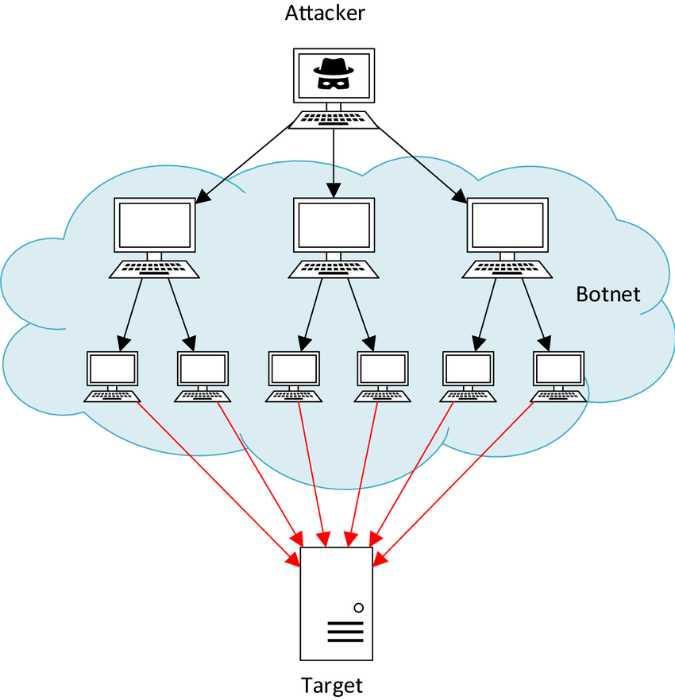
When they're ready, the attackers instruct the whole botnet to attack a specific device or server by sending out as many requests as possible. One typical example is the Mirai botnet, where hackers exploit the vulnerability of IoT devices to gain access and use them to create DDoS attacks.
Different Types of DDoS Attacks
There are many DDoS attacks, so containing them can be challenging. Even though they are the same at their core, they have different methods and characteristics. Here are some of the most common DDoS attacks.

Resource Exhaustion
Attackers often use brute force attacks where they try to overwhelm a network by exhausting all resources with countless login attempts. These attempts usually target authentication systems. On the other hand, resource exhaustion attacks can also send many SYN/ACK packets to disrupt services.
Application Layer Breaches
The most common application layer attack is the bombardment of web servers with HTTP or HTTPS requests to exhaust all resources. On the other hand, some of them send partial HTTP requests to consume server resources and keep connections open to cause a denial of service.
Protocol Attacks
Hackers sometimes exploit open DNS (Domain Name System) servers to increase the traffic directed toward a target while making the requests look like they're coming from legitimate sources.
They also similarly use open NTP (Network Time Protocol) servers to amplify traffic volume. Some DDoS attacks look to exploit vulnerable UPnP (Universal Plug and Play) and SSDP (Simple Service Discovery Protocol) devices to increase the scale of the attack.
Volumetric Attacks
Volumetric attacks can overwhelm the target by flooding it with UDP (User Datagram Protocol) packets with spoofed IPs. Another type of volumetric attack uses ICMP (Internet Control Message Protocol ) packets to consume the resources and bandwidth of the target.
Hybrid Attacks
Hybrid DDoS attacks combine several techniques to maximize the damage. An attack can start with a volumetric assault and switch to application layer attacks to exploit multiple differences and saturate bandwidth.
What to Do if You Get DDoS-ed
A DDoS attack is a severe threat that can hinder your online services. You must act accordingly to mitigate the damage and fight off the attack.

Identify the Attack
The first step is identifying an attack, which can be challenging because the attack can come from multiple sources. However, several tell-tale signs indicate a DDoS attack:
- If you get a ransom demand after your website crashes, it's clear an attack happened. Attackers usually require ransom in crypto like Bitcoin.
- If your web application has a significant surge of traffic from different IPs from regions where you don't have many users, it might be a sign of a DDoS attack.
- If you notice that your system is running slowly, you have high outgoing traffic, and your CPU usage is constantly high, it might be a sign of a DDoS attack.
- If your DDoS detection service notifies you of an attack and shows strange traffic patterns, it is a sign of a DDoS attack.
Use DDoS Mitigation Services
Many website owners use cloud and internet service providers offering DDoS attack mitigation services. Activate these services once you recognize an attack to quickly filter out malicious traffic and prevent your site from crashing.
Ask your ISP (Internet service provider) or hosting service to temporarily increase your bandwidth so your website can remain operational and absorb high traffic volumes without crashing.
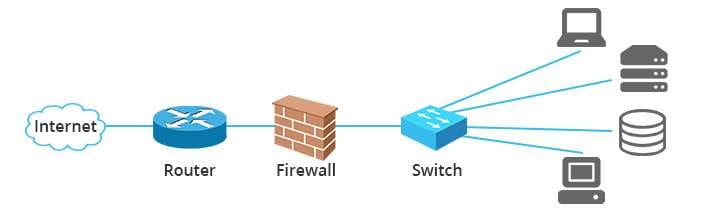
Configure Routers and Firewalls
Switching your IP address is critical in a DDoS attack, and you can do that using the web browser or router interface. Adjust your router and firewall settings to block all the malicious traffic you've identified. You can adjust both networking systems to limit the allowed requests from a single traffic source.
Get a Content Delivery Network
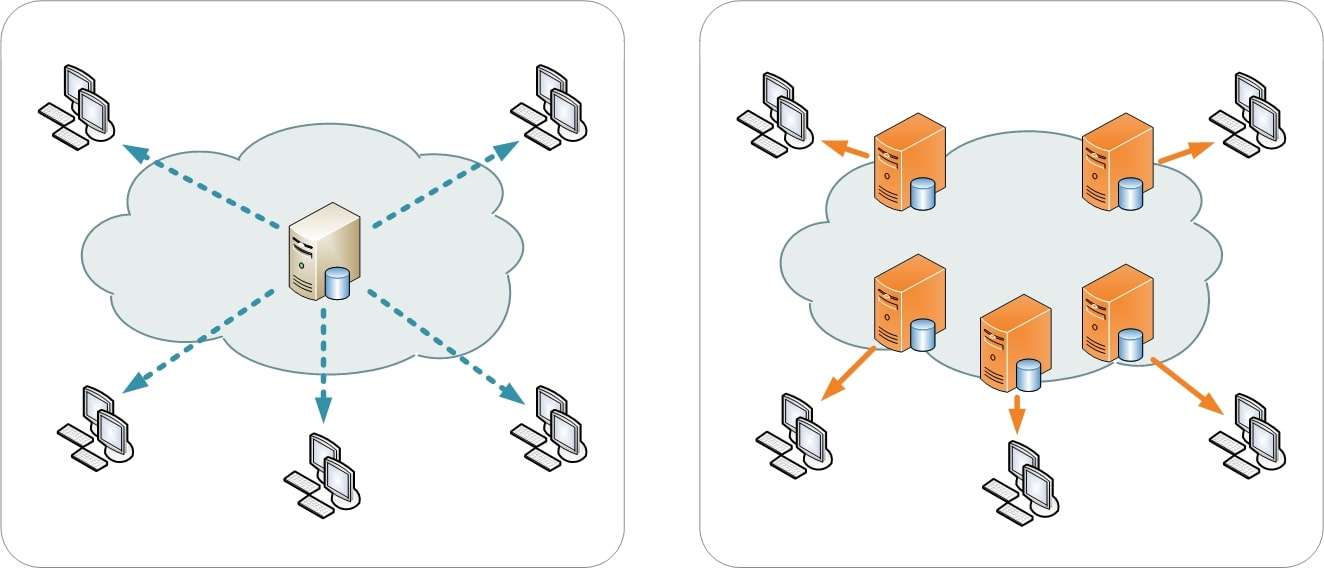
Consider contacting a CDN (content delivery network) service to distribute your content across several data centers and servers. That will allow you to boost the performance of your website, absorb traffic, isolate data, and ensure your website is still up and running while dealing with the attack.
At the same time, you can use Anycast DNS to distribute all the requests across multiple servers, allowing you to take the load off your primary server and prevent website crashes.
Continuously Monitor and Analyze Your Network
By monitoring your network, you can recognize patterns and determine where the attack originated. Containing one source at a time can make a massive difference in hindering the effectiveness of the attack. Analyze the traffic to understand the nature of the attack and make the best decisions for preventing it.
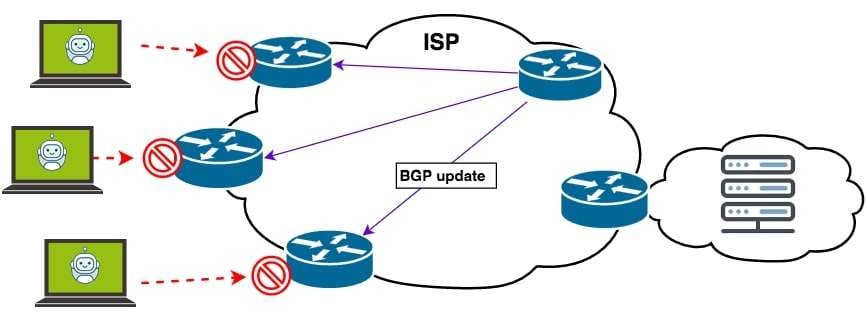
Implement Black Hole Routing
Another way to defend yourself against a DDoS attack is to use black hole routing. The network administrator or the ISP can create a black hole route that sends all the traffic into a black hole.
That means all the traffic will go to a non-existent route and drop from your network. However, it also means that your legitimate traffic will be lost.
Post-Attack Recovery Process
The following post-attack steps will help you recover after a DDoS attack and prevent future invasions on your network.
Recover Your Lost Data
Many DDoS attacks include network compromise, ransomware, and data theft. That's why it's essential to have a data recovery plan in place.
First, consider backing up your data so you can quickly restore it. On the other hand, it's generally a good idea to have a professional data recovery tool like Wondershare Recoverit to retrieve deleted data and make it available once again.
Here's how simple it is to use:
- Launch Wondersahre Recoverit, click Hard Drives and Locations, and select where you want to scan for lost files.

- Wondershare Recoverit will automatically scan the drive you selected, and you can track progress in the bottom left corner.
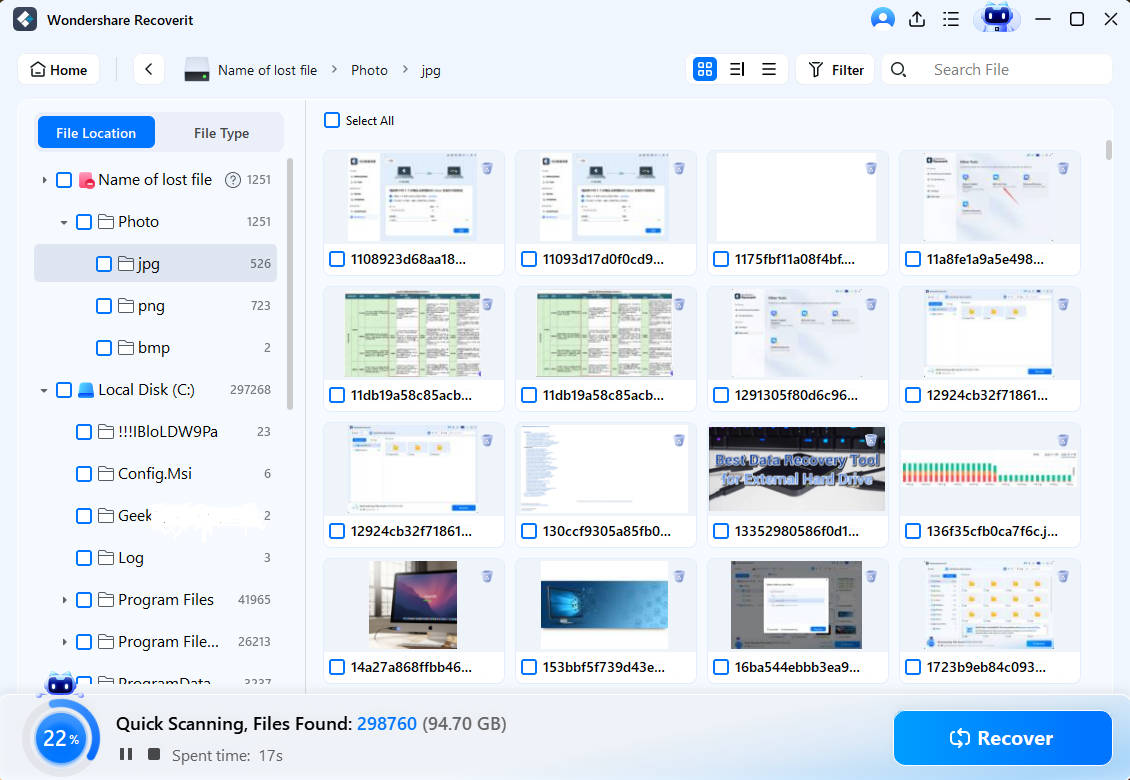
- Preview the files to check if they're the ones you're looking for. Click Recover if they are.
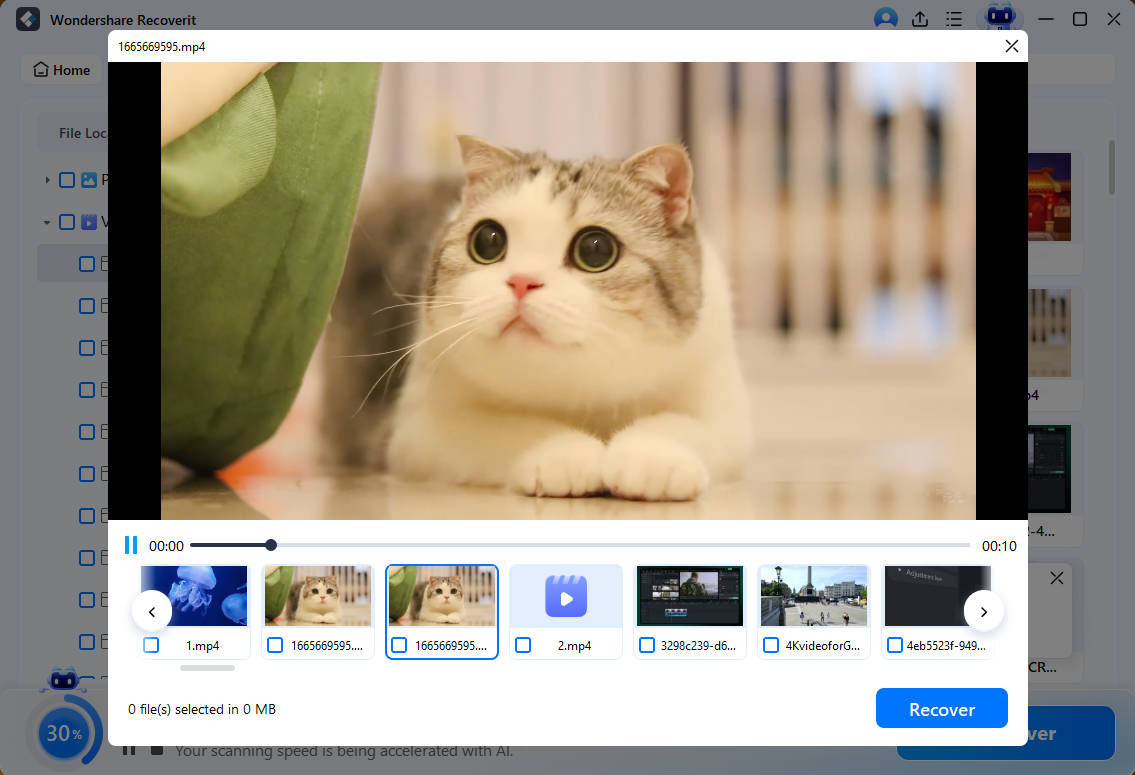
- Name the file and select the save destination. Click Save when you're ready.
Document and Analyze the Attack
Record all the attack details, including patterns, characteristics, type, and duration. Conduct a thorough analysis to see how the attack happened and which vulnerabilities led to it. See which measures were helpful and which weren't. Take the time to review traffic data and logs to gather information for future prevention.
Update Systems and Security Measures

Review your network configuration and incident response plan, and work with your hosting provider or ISP to create a better security strategy. At the same time, ensure that all your software, including apps, operating systems, and tools, has the latest security patches.
Conclusion
DDoS attacks are evolving, and attackers exploit new vulnerabilities and use different techniques. Organizations and individuals must upgrade their defense systems and mitigate attacks effectively.
If you notice a DDoS attack, the key is to act quickly because that will help you prevent further damage. After the attack, take the time to recover your data, analyze the attack, clear out the threat, and update your security systems, tools, and operating systems to prevent future attacks.
FAQ
What happens when you get DDos-ed?
When a web server gets DDoS-ed, it typically results in a significant slowing down or becoming completely unavailable. All of the customer services and internal server access will be cut off, which could cause major harm to any organization.Do DDoS attacks target small businesses?
DDoS attacks target even small organizations. Even though attackers can't get much money from targeting them, the lack of robust security measures makes them an easy target.How long does a DDoS attack last?
The attack's duration can differ depending on the type and the security systems. It might last a couple of minutes up to a few days.