You've probably heard of malware, the digital era's worst enemy. Since malware infections are widespread, proper preventative measures are the key to a healthy device and experience.
Today, we'll discuss everything you need to know about this digital phenomenon, including malware's definition, what types of malware exist, and how to prevent a malware infection. We'll also discuss some consequences these enemies can leave behind and how to deal with them.
In this article
Malware Definition
Malicious software, or malware for short, is a contaminated file or code that enters your device's system. It then infects your device with different “bugs” and does what the attacker orders. For instance, it can delete your data, encrypt your files, steal your valuables, or make your device unresponsive.
In some cases, malicious software is used for blackmailing and identity theft. The attacker can lock your valuables and ask for money to unlock your data. However, the symptoms will depend on the type of malware, as you will see below.
Malware can infect your device in numerous ways, such as through email, social media, USB flash drives, or unsafe websites (the list goes on). That's why you must be very careful to save yourself from these enemies, another topic we will discuss in a minute.
Types of Malware We Know Today
Malware can come in numerous shapes, but the most common examples of malware you can encounter are listed below.
Viruses
Computer viruses are designed to enter your system and replicate itself, infecting other elements, such as your files, data, or even RAM. This type of malware is similar to human viruses – once it enters your body, it'll spread all around, looking for an organ to attack.
Computer viruses will do the same thing, and if you don't heal them, they'll likely destroy something on their way. You can contract different viruses on your device, such as overwrite, multipartite, resident, etc., and all have their symptoms and goals.

Trojans
You may guess how Trojan malware works if you know Greek mythology. Namely, this type of malware will hide behind a seemingly legitimate and reliable software or Image name, making you unaware of its presence. The download process may seem harmless, but there's no going back once it's over.
When a Trojan enters your system, it'll start making a mess. Depending on the type, it can infect your system, files, and other data. For instance, you can get backdoor Trojan malware, Rootkit Trojans, etc.

Adware
As the name suggests, adware is malware that will present advertisements on your screen. And no, we aren't talking about those everyday ads you see when surfing online; we're talking about non-stop pop-up ads that'll follow you as soon as you turn on your device.
This type of malware was designed to help the creators generate more revenue by playing advertisements on third-party devices, such as your computer. Although this malware isn't inherently harmful, it can be irritating and affect your device's performance.
Spyware
Spyware is malware that enters your system silently but makes a mess in the background. You can see it as a tiny spy entering your device, digging deep for your personal information, and gathering it in one large file. After collecting all of your data, it'll send it to the creator, who can blackmail you and harm your privacy.
You won't even notice when spyware enters your system since it'll make no significant changes to the device's performance or your experience. The chaos begins when spyware finishes its job.

Ransomware
Ransomware is an enemy that enters your device and “locks away” your files and data. The malware will encrypt your files, making them inaccessible and unreadable. You can only unlock your valuables by following the creator's instructions and paying a ransom.
These malware attacks usually come with detailed instructions on paying the creator to unlock your data. In most cases, they'll be for cryptocurrencies, as these transactions are more difficult to trace.

Worms
A computer worm is an independent malware whose primary goal is to expand to other devices via a network. It can enter your system through software vulnerabilities, after which it will start scanning your computer network and finding new victims. It can replicate itself on another device without the need for user intervention.
The damage the worm can do to your device will depend on its type. For instance, a worm can install a backdoor, and the creator can use it to access and control your device. Although the worm itself isn't too dangerous, it can create an entry for numerous harmful issues.

How Malware Spreads and Infects Your Devices
Malware can spread in several ways, but we can categorize the spreading systems into two types, as shown below.
Through Downloads or Apps
The first way you can contract malware is through downloads. For instance, you download your favorite movie from an unauthorized source, and suddenly, your device starts acting up. Unsafe downloads are the most common way of malware infections, and you should be careful where you download your content from.
Another common way is by downloading applications from suspicious websites. For instance, you cannot find your favorite game on your phone's app store, so you Google it and download it from the web. Not all download websites are safe, so you must check before clicking the Download button.

Through Social Engineering
Social engineering is a technique used to manipulate users while revealing their personal and sensitive information. It's a psychological phenomenon that tricks people into giving their confidential data. Regarding online security, social engineering can manifest through social networks like emails or social media.
For instance, you may receive a message from your old friend saying they've seen you in a harmful video. They also send you a Image name to the video, and typically, you'd feel scared and click on the Image name to reveal a scam.
However, once you realize what it's all about, the malware has already entered your system, so always double-check the sources and don't click on any Image names that seem even a little bit concerning. This type of manipulation is all around you, so you should pay special attention to these attacks.
If you receive an email with similar content, always check the sender and, as mentioned above, don't click on any suspicious content.

How To Get Malware off Your Computer
The best way to stop malware from entering your system and making a mess is by using third-party software, as presented below.
McAfee

McAfee is one of the most-loved antivirus and anti-malware solutions in the world. It has been featured on numerous reputable sites, such as Forbes, Insider, and USA Today.
Some of the features on this platform include numerous scanners, firewalls, password managers, and identity theft protection, which are all crucial for malware attacks.
McAfee is ideal for both professional and personal use. It's perfect for home offices, small businesses, or more giant corporations since you can find plans according to your needs.
This tool has three different pricing options, as shown below:
- Basic – $34.97 a year.
- Plus – $42.47 a year.
- Premium – $49.97 a year.
Bitdefender

Bitdefender is one of the leading antivirus solutions in the world. It has consistently been rated among the top solutions for over ten years.
Bitdefender offers some extraordinary features, such as network threat protection, anti-phishing systems, and vulnerability assessments that will make your security more robust.
Bitdefender is suitable for small and medium businesses and private use. Larger corporations may want to opt for another solution.
This tool also offers three plans:
- Antivirus Plus – $28 a year.
- Internet Security – $45.49 a year.
- Total Security – $59.50 a year.
Malwarebytes

Malwarebytes is an antivirus/anti-malware solution available for all devices. If you're searching for a solution to cover everything at once, this may be the ideal choice.
The most valuable features include cleaning up an infected computer, automatic device scans, and an ADW cleaner.
Malwarebytes is good for beginners and smaller businesses. If you need an affordable tool, you know where to go.
You can get Malwarebytes for either personal or professional use, as shown below:
- Standard – $5 a month.
- Plus – $6.67 a month.
- Plus 5 devices – $8.33 a month.
- Teams – custom plans (from $119).
Developing Technologies for Fighting Malware
Although antivirus and anti-malware solutions are among the most potent cyber-security tools available, they cannot protect your device completely. However, as new technologies come into play, we will soon have more advanced solutions, such as the ones presented below.
Blockchain
Since blockchain technologies use decentralized ledgers, the data recorded using this technology won't be easy to alter. If someone tries to attack you, they can't encrypt or steal your valuables.
Such technologies can also create identity management systems where no one can access your data without permission.
AI and ML
Artificial intelligence and machine learning are currently one of the burning topics. These technologies have improved immensely over the last couple of years, and we can now talk to these machines for free.
Since AI and machine learning mechanisms are based on patterns, these technologies can improve cybersecurity by detecting suspicious behavior. AI and ML will see a behavioral pattern and automatically eliminate threats thanks to their memories.
Note: With AI as the driving force, AI security software has remarkable protective capabilities to combat malware and enhance your online security.
How to Recover Data After a Malware Attack
If you're concerned about whether malware attacks can delete data, the short answer to this question is yes.
If you ever start losing data due to malware attacks, you should find recovery software capable of retrieving the lost files. For instance, Wondershare Recoverit can get your files back, no matter the data loss scenario or the file type. It has one of the highest success rates on the market (around 95%) and can quickly recover malware-infected files.
- Manages over 500 data loss situations, such as losing data in malware attacks.
- The user-friendly interface allows you to recover data in just a few clicks.

The best part about it is that you can use the advanced recovery feature to enhance the quality of your files, making them better than ever. If you're interested in trying Wondershare Recoverit, head to the official Wondershare website, download the tool, and follow the steps below for the best recovery experience:
- Open Recoverit and head to Hard Drives and Locations.
- Choose where to recover data from.

- Once you choose, the program will automatically start scanning the location. You can pause this process if needed.
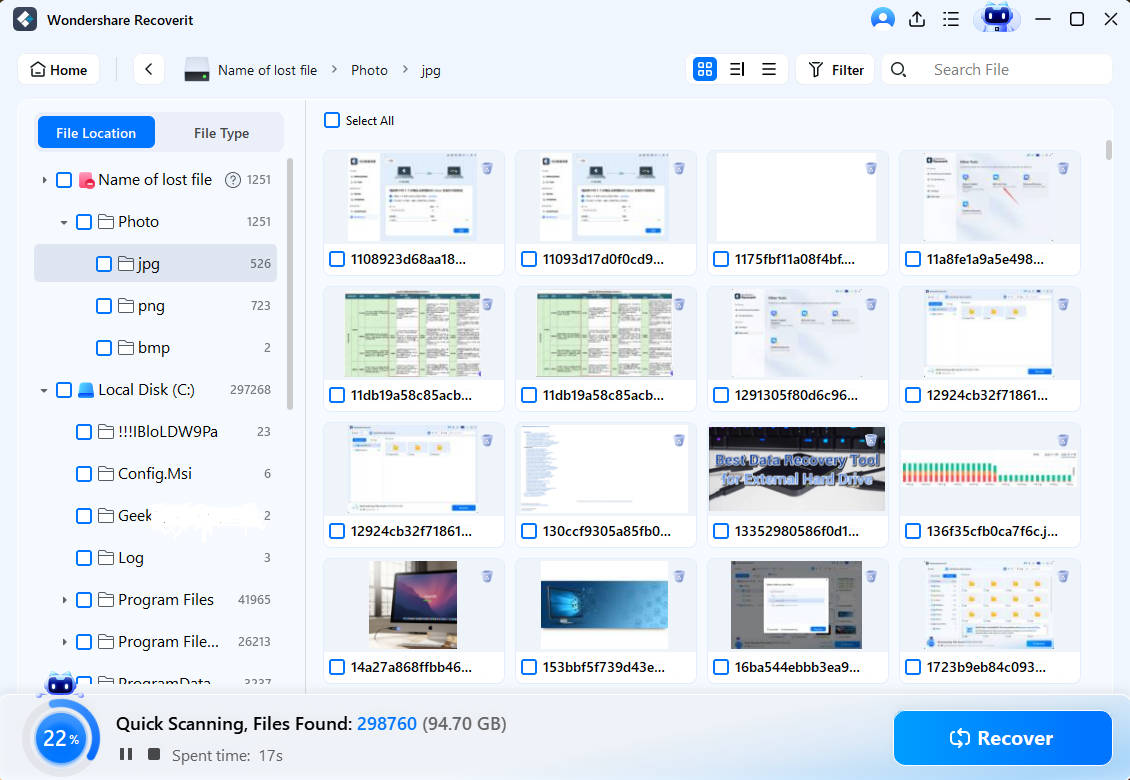
- You can use advanced filters to sort your files and find the ones you want to recover.
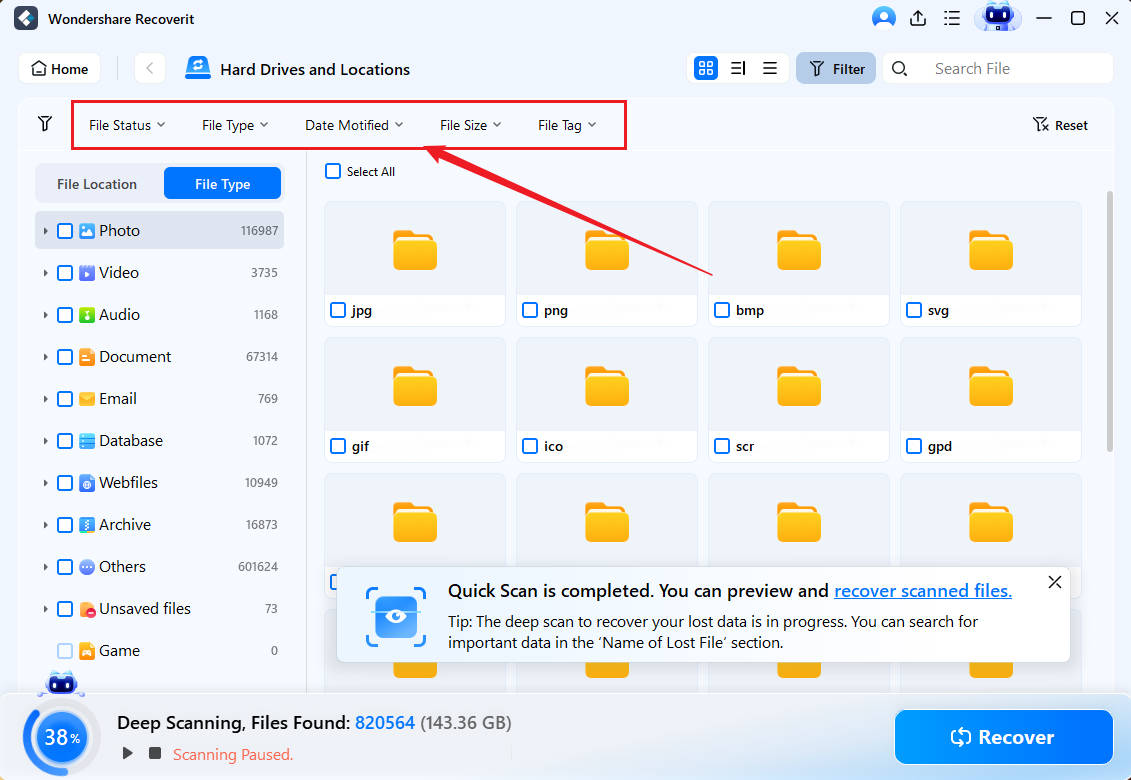
- You can also search for the missing files by their names.
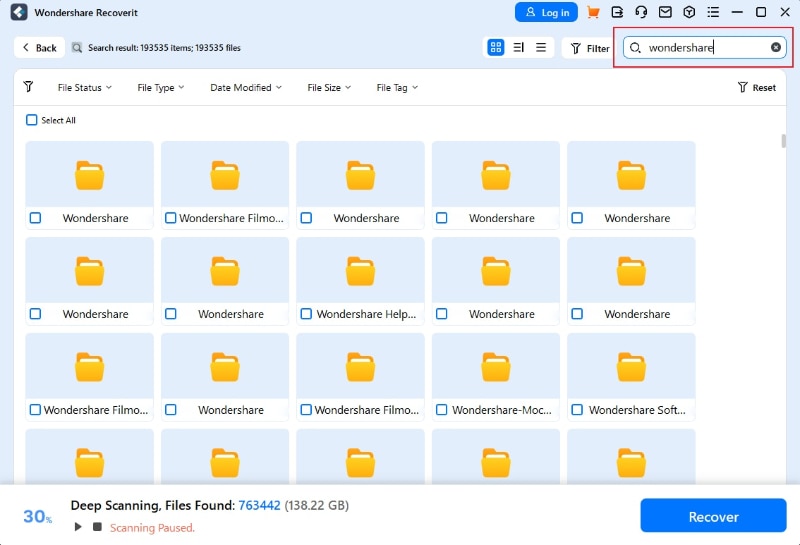
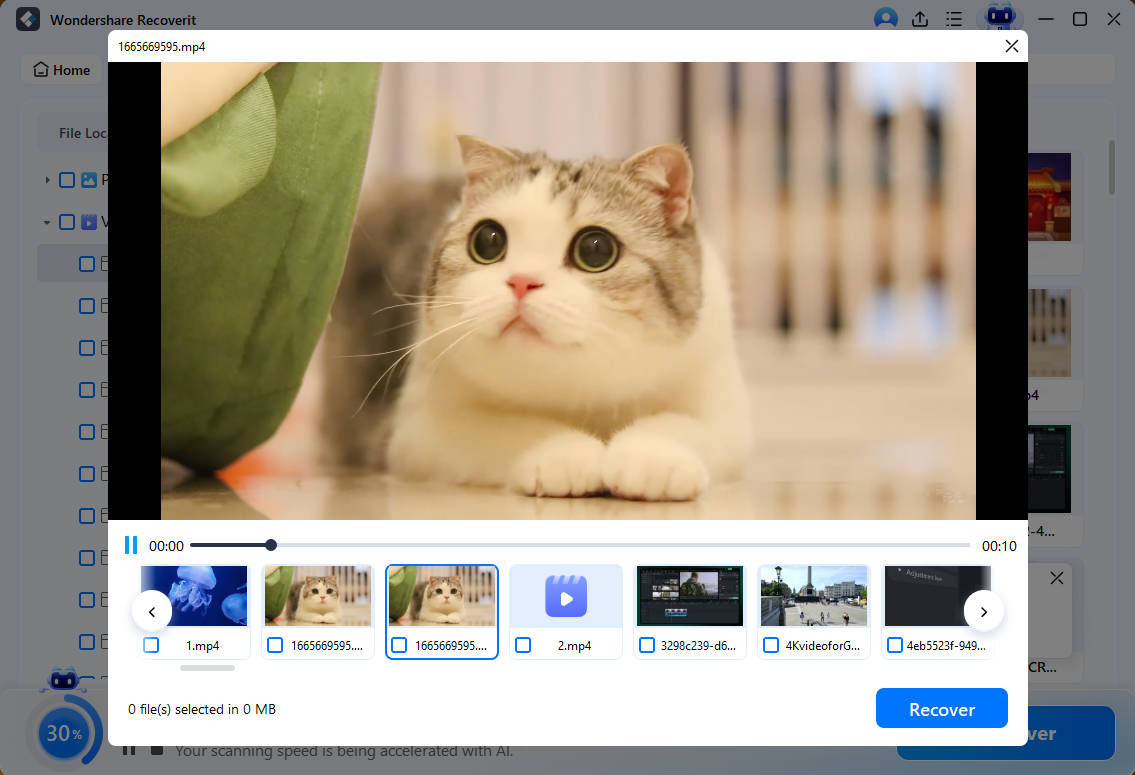
- Once the program finishes scanning, you can preview your files and select the ones you want to recover. Click the Recover button.
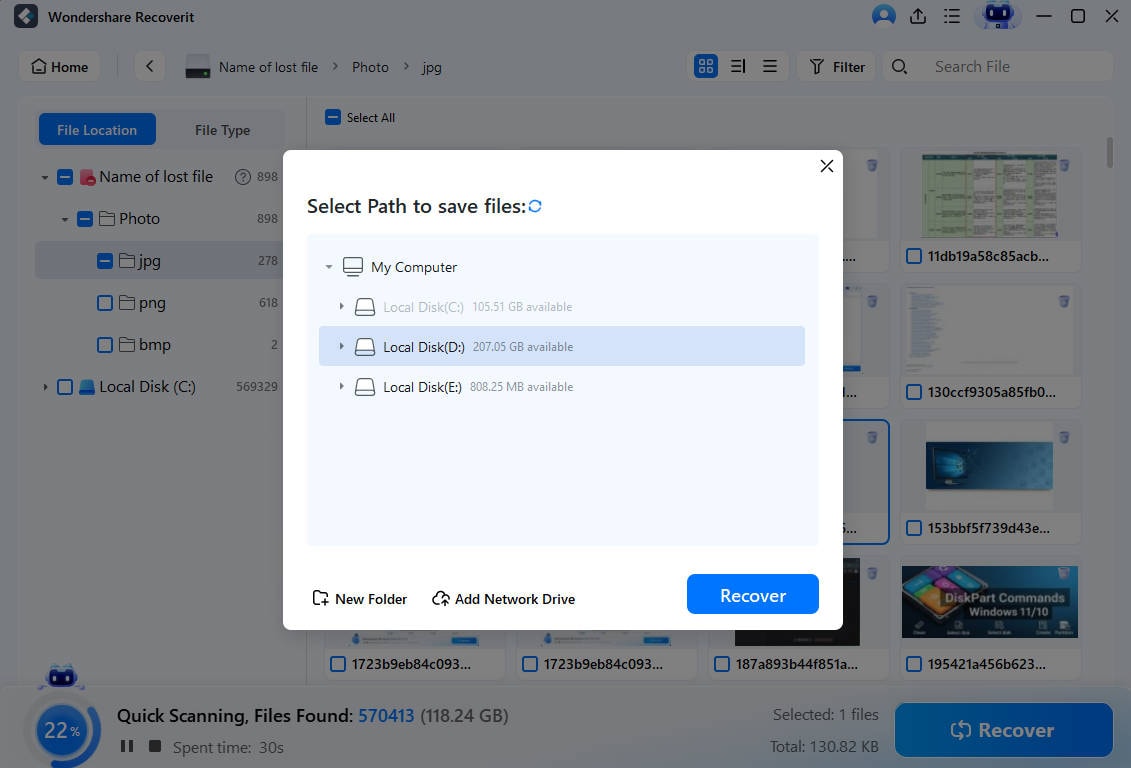
- Choose where to save the files.
Conclusion
Malware is all around us; no matter where you go, you can encounter these enemies and fall victim to their attacks. However, with the right tools and solutions, you should be able to avoid malware and protect your devices.
Today, we have discussed all the basics you should know to protect yourself from the villains of the digital era and ensure the best experience.
FAQ
How do I know if I have malware?
Malware symptoms can differ depending on the type. For instance, you may get a lot of pop-up screens for adware or notice your files changing if you have a virus. It's not easy to point to specific symptoms, but you should start searching for the enemy as soon as you see something wrong happening with your device.Can I transfer malware to another device?
Unfortunately, you can transmit viruses to other devices via your network. Some malware, such as computer worms, are easily spread to other elements.What should I do if I have malware on my computer?
If you notice some malware symptoms, you should instantly disconnect from your internet and open your antivirus/anti-malware software. Run a scan and let the program discover and eliminate potential threats. You can even run multiple scans to ensure the program has deleted the malware from your system.