Is malware and virus the same thing? Contrary to popular opinion, no. While we rarely discuss them separately, these two types of cyberattacks are different. Either can infect your device anytime, so understanding what they are is super-important.
Here's a guide on malware vs viruses and how to protect yourself.
In this article
Malware vs. Virus: Definitions
Malware is trouble. Everyone knows that. But what is this trouble, exactly?
By definition, malware is "specifically designed to disrupt, damage, or gain unauthorized access to a computer system." It can be a file, application, software, or code. Regardless of its many forms, malware always has the same purpose—to carry out a cyberattack.
Virus is malware that spreads through a computer, network, or server by self-replication. It is usually distributed through files and programs. A virus will contaminate your computer after downloading an infected application or opening an infected attachment.
Computer viruses date back to 1982, when the first one was developed for Apple II. Since they've been in the public's eye since the beginning of the commercial internet, viruses have become synonymous with illegal online activity. As you'll soon learn, that is a gross oversimplification.

In reality, there are many different examples of both malware and viruses:
| Malware | Viruses |
| Most people are familiar with the Trojan horse. This malware disguises itself as a legitimate file or program to trick a computer user into installing it. | Polymorphic codes are sophisticated viruses that can rewrite their own code and dodge antivirus detection programs. New variants of this virus involve AI. |
| Spyware is a malware type for tracking or recording information about user behavior. Spyware often collects credit card info and other sensitive data. | An overwrite virus is a common type of computer virus. As its name suggests, it infects files and programs by overwriting their contents. |
According to recent reports, 560,000 new pieces of malware pop up daily, and over 1 billion malware programs currently exist. You might also be familiar with ransomware, adware, worms, rootkits, keyloggers, macro viruses, browser hijackers, etc.
Critical Differences Between Malware and Viruses
Let's explore some of the critical differences between malware and viruses.
Mode of Operation
Cybercriminals need malware to access a computer, system, network, or server. While a virus also works by inserting itself where it's not welcome, it doesn't continue communicating with its sender like malware does. Malware slips through a crack in the system and sets a backdoor.
Unlike malware, a virus is a lone operative. It gets into a computer attached to a file or program and stays dormant until you activate it. In most situations, a virus triggers when you click the infected file or program's icon to install or open it or click an infected Image name.

Intent of the Program
Why does malware need to communicate with the perpetrator after it gains unauthorized access? It's simple—because its job is to scoop data and send it back home. Depending on the type of malware and the attack's intent, it can collect anything from actual files to payment data.
On the other hand, a virus is usually programmed to do some kind of damage. For example, once it activates, it can spread to delete or overwrite files, turn off security programs, take control of critical system operations, or encrypt your data until you pay a handsome ransom.
Infection and Spreading Methods
We've mentioned that malware looks for cracks in the system to enter a computer, network, or server. Only specific malware types sneak in through downloads and malicious attachments as viruses do. Malware's primary method of infection is social engineering, such as phishing.

The most recognizable characteristic of any computer virus is its ability to replicate and spread. You can catch one while downloading a file or software or opening a malicious email. Corrupted storage devices and infected websites can also spread computer viruses.
Replication Capabilities
The ability to spread through self-replication is a distinctive trait that separates viruses from other types of malware. Besides viruses, worms are the only malicious software that can copy itself to spread to other computers or networks.
When a virus infects a computer, and the user unknowingly activates it, it starts copying itself or spreading attached replicas of itself to other files and software throughout the device. Sometimes, those copies overwrite the host app, making it more challenging to uproot.
Removal and Detection Mechanisms
Would you be able to recognize a malware or virus infection? Some types, like ransomware or direct action viruses, want you to know they've seized control of your computer. Others stay silent until you detect them. These are some tell-tale signs of a malware or virus infection:
- Slow performance
- Sudden crashes
- Annoying pop-ups
- Unknown software
- Denied access
- Scary warnings
- Disabled system tools
In terms of removal mechanisms, malware and viruses don't differ much. In most cases, you can eliminate them with a broad-spectrum or specialized antivirus or anti-malware tool. Other situations, including malware spreading to your computer's memory, require an expert.
How to Protect Yourself Against Viruses and Other Malware
Is malware really that dangerous? Let's answer that with a question—would you be comfortable if criminals gained access to your data? Of course not. Data theft, usually the goal of malware attacks, typically results in financial loss. For example, criminals can steal your credit card credentials and, consequently, all your money. They can lock you out of your computer or threaten to expose private data unless you pay them.
A virus can also hurt your email contacts by using your account to spread the infection.
The dangers of malware and virus attacks are even more significant for organizations. Studies reveal that nearly 43% of attack victims are small businesses, many of which declare bankruptcy in the aftermath. Malicious software can cost them between $823 and $653K.
Fortunately, you can avoid all that by employing simple preventative measures like these.
📌Software Updates
Software updates refine your OS and programs to help them function better and faster. However, there's more. Software developers are constantly looking out for new security threats, developing effective defenses that they include in software patches.
From the cybersecurity point of view, don't postpone a new update. Otherwise, you'll leave a window open for criminals to exploit the unpatched vulnerabilities in your system.
📌Safe Internet Practices

Using the internet and your computer with cybersecurity in mind will give you a better chance of dodging a cyberattack. Learning about malware and viruses is an excellent first step. The more you know about various cyber threats, the lesser the risk of falling into a trap.
With that in mind, we've prepared a checklist of habits that should become part of your routine.
- Create complex passwords with random characters.
- Use multi-factor authentication whenever you can.
- Close and erase online accounts that you don't use.
- Don't visit unprofessional and shady-looking sites.
- Don't click unsolicited Image names from "free" offers.
- Use antivirus software to scan a file before downloading it.
- Don't open suspicious emails from unknown senders.
- Learn more about different phishing tactics.
- Read all privacy policies and terms and conditions.
- Always choose online providers that offer encryption.
- Never share private information over public Wi-Fi.
- Never overshare on social media or other sites.
📌Antivirus and Anti-Malware Tools
If you have a reason to suspect that your device has been infected, the first step to take is to download an antivirus program, whether or not you already have one. Malicious software has found a way around your current defense system, so you'll need a more effective tool.

Choose antivirus software according to your desired type of protection. An average user who keeps a computer for streaming doesn't need the same protection as a company with 1,000 employees. Still, insist on threat prevention features such as:
- Web browsing protection – The best antivirus can help you avoid shady websites and Image names by marking suspicious URLs according to their safety risk potential.
- Reactive file scanning – Checking any file before downloading or opening prevents viruses from activating and spreading.
- Complete system scans – Comprehensive malware scans are non-negotiable. Use a tool that checks every corner of your computer against known threats.
- Automatic threat removal – If new malware slips through, the antivirus should isolate, analyze, and eventually remove the threat.
📌Recovery and Backup Methods
Viruses, worms, and other malware are often programmed to delete files. One of the best examples is the so-called wiper malware. Its purpose is to cover up the criminals' tracks after they execute an attack, destroying your data.
That's why you should always back up your files. Windows and macOS have native backup systems that you should enable unless you use a third-party tool.
What if you've already suffered data loss from a virus or malware attack?
In this case, you can rely on robust data recovery tools like Wondershare Recoverit to rescue your deleted files. Wondershare Recoverit is an excellent choice for virus-related data recovery, supporting all file types and virtually any device. It also makes a complicated process very simple.
- Excellent at managing data loss due to malware and virus attacks.
- The user-friendly interface allows you to recover data in just a few clicks.

Hopefully, you won't need it, but here's a guide for data recovery, just in case:
- Download, install, and launch Wondershare Recoverit for your OS.
- Select a location where your lost files used to be before deletion.

- The program will start scanning it, which may last a while. During that time, you can watch the progress and pause the process if necessary.
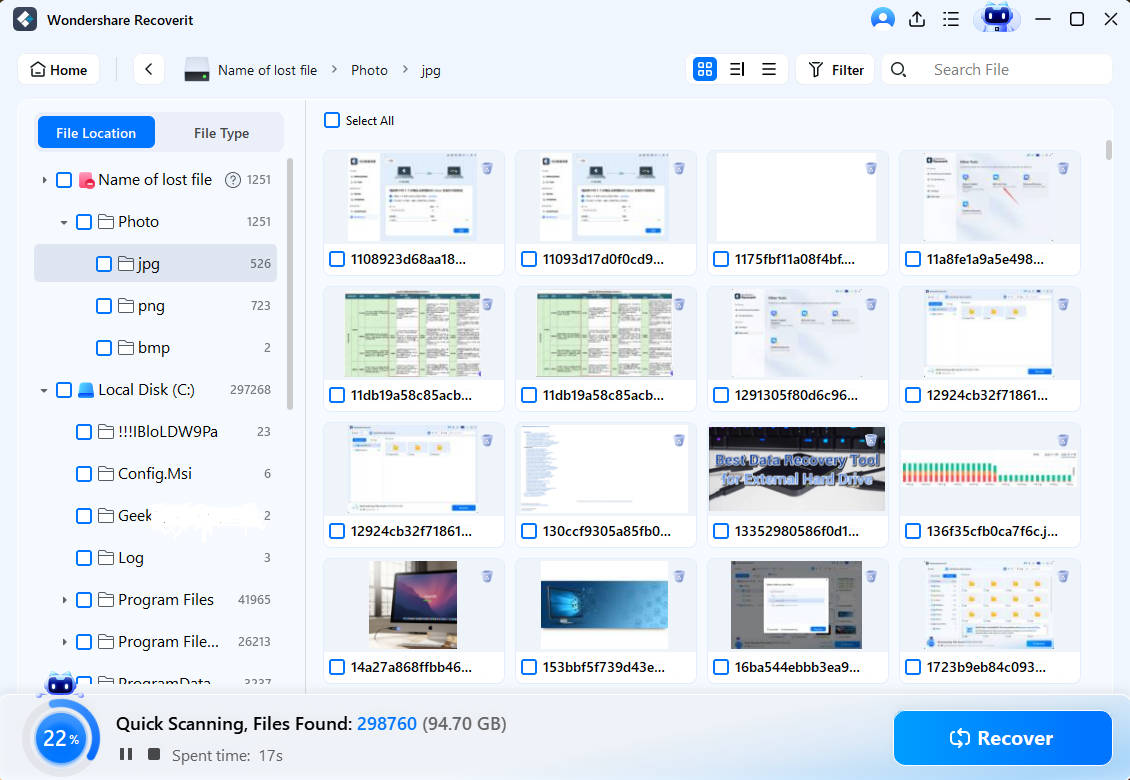
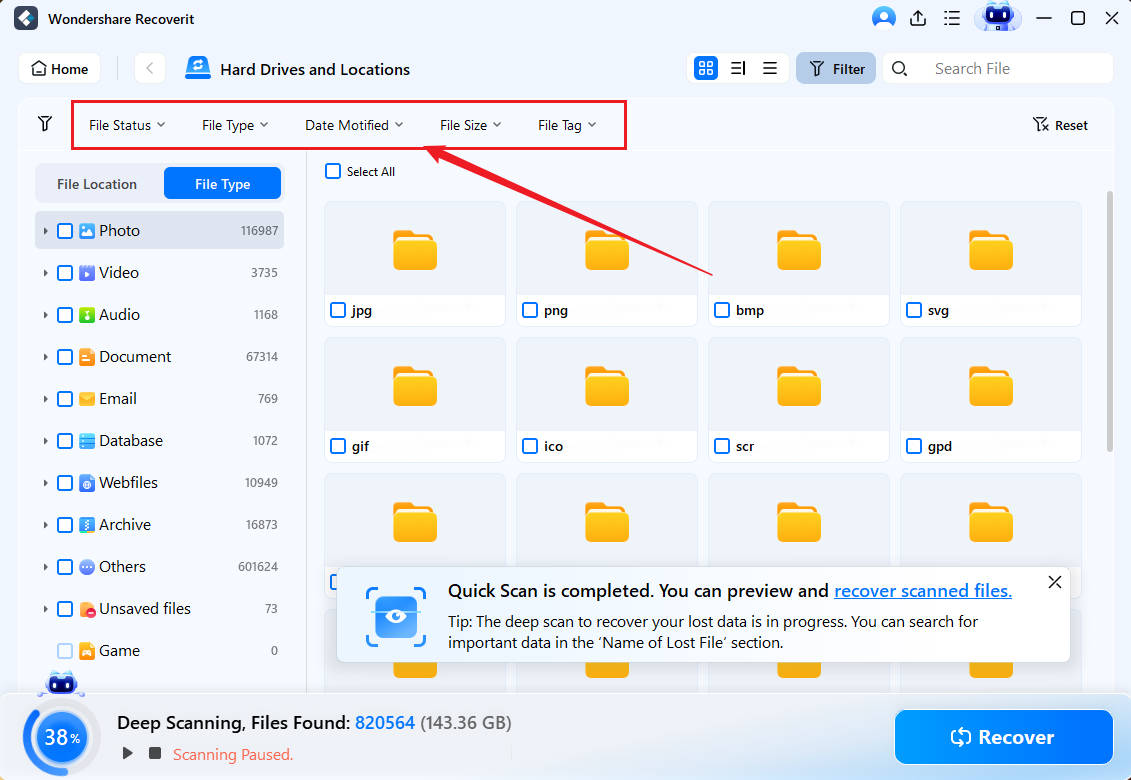
- Once the scan is complete, you'll see a list of your recoverable files. Use filters to search the results if there are too many items.
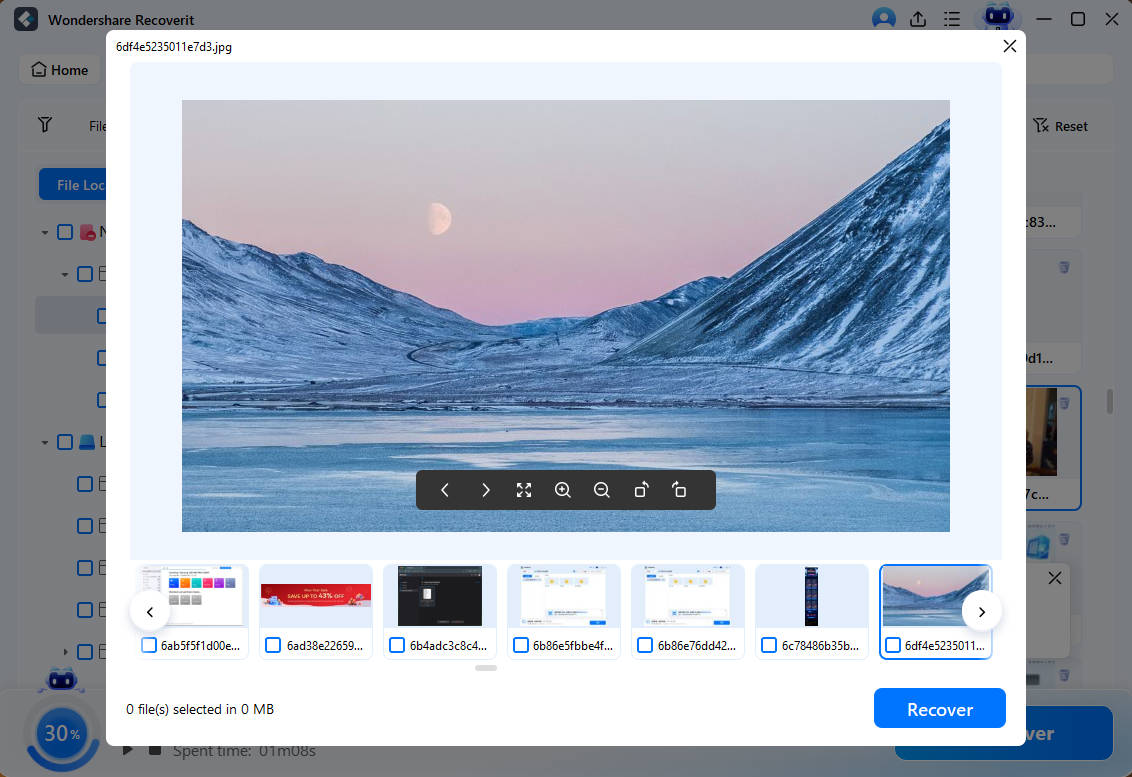
- You can preview every file before recovering it on your computer.
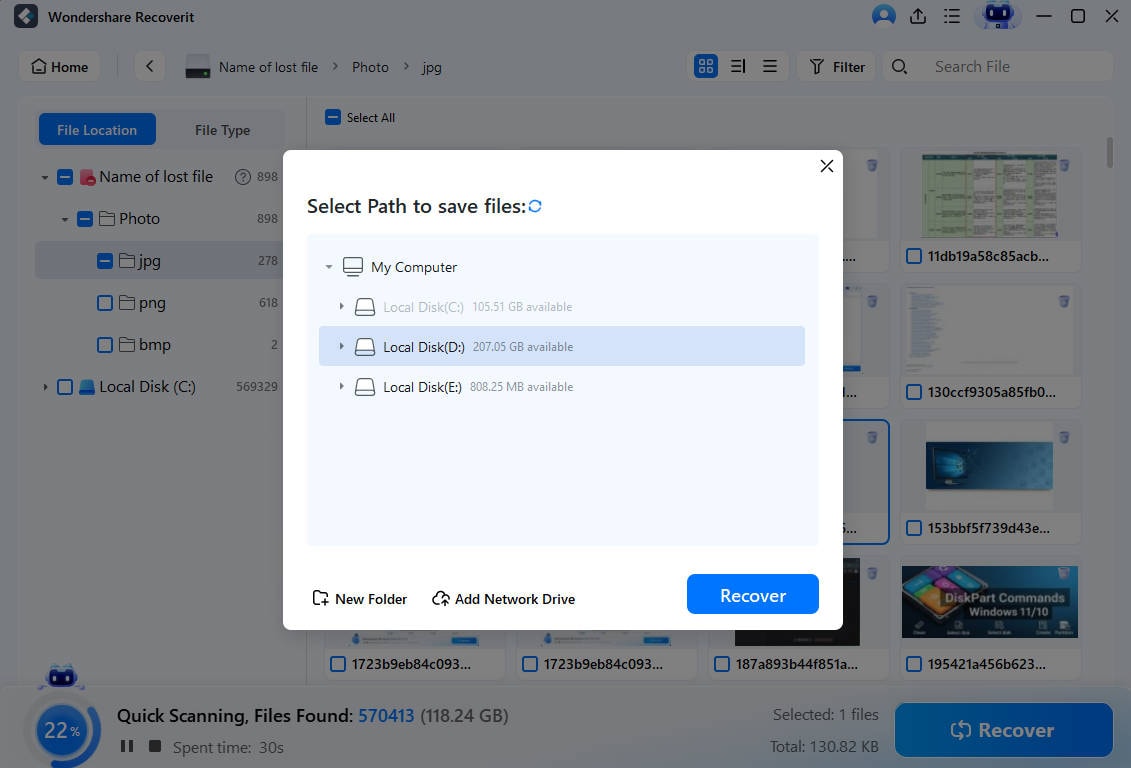
- Select what to retrieve and click Recover.
- Choose a safe destination and click Save.
Conclusion
As you can see, malware and viruses are not synonyms as we often use them. Don't take either for granted. They can cause severe damage if you keep your computer vulnerable to threats. Therefore, run regular updates and data backups and get a high-quality antivirus tool.
Most importantly, use common sense online and always think before you click. If you still encounter an attack, you can always rely on Wondershare Recoverit to save your data.















