Have you noticed breached security on your computer? A Trojan Horse virus might have infected it. The attacker could steal your confidential data, so we've prepared a comprehensive guide to help you remove the virus.
We'll first explain what a Trojan virus is, how it works, and how to prevent an attack. Then, we'll walk you through several methods for Trojan horse virus removal. With our guidance, you'll learn how to remove the infection quickly and efficiently.
In this article
What Is a Trojan Virus?
A Trojan horse virus is malware disguised as a legitimate file or software. Its name derives from the wooden horse that allowed the Greeks to infiltrate Troy and win the war. Like the Trojans who welcomed this gift, unaware that Greeks were hidden inside it, ready to attack them, a Trojan virus appears as a legitimate-looking file and is a massive security threat.

Since a Trojan virus infiltrates your computer unnoticed, it can take over the system and steal your precious data, including usernames, passwords, and social security numbers. Besides stealing your data, Trojans can delete entire hard drives and shut down your computer randomly without you detecting them.
How Trojan Viruses Work
Now that we've covered what Trojan Horse viruses are, it's time to see how they work.
Main Characteristics of Trojan Horse Viruses
One of the main characteristics of Trojan Horse viruses is that they camouflage themselves as legitimate, safe files. They can appear as email attachments, software patches, attractive applications, etc. The victims themselves usually download Trojan viruses, as cybercriminals manipulate them into doing so.
Another characteristic of a Trojan virus is that it infects the system slowly. It takes its sweet time to infect the victim's computer to avoid detection and steal information. It's malware designed to damage files, steal data, and spy on the user's activity.
Primary Types of Trojan Viruses
A Trojan horse virus can work in numerous ways. Thus, we can divide them into several types of Trojans. These are the most common Trojan viruses:
- Backdoor Trojan – This type of Trojan gives access and control over the computer's hardware to the attacker, allowing them to use microphones and cameras and steal data.
- Distributed Denial of Services (DDoS) Trojan – DDoS Trojans perform actions to dismantle your network. They execute attacks and flood your system with requests from many different sources.
- Fake AV Trojan – This type of Trojan masks itself as antivirus software. It usually requires payment to eliminate viruses and threats from your computer, regardless of whether it is infected.
- Ransom Trojan – These Trojan viruses encrypt your data and lock you out of your system, holding it at ransom. Then, they ask for financial compensation to undo the damage.
- Rootkit Trojan – These Trojans hide existing malware and prevent its discovery before performing maximum system damage.
- SMS Trojan – These Trojan horse viruses infect mobile phones, posing as a free app to steal, monitor, and divert text messages.
Critical Trojan Virus Prevention Strategies
If a Trojan horse virus can go undetectable, what can you do to prevent it from infecting your computer? We've prepared several tips and strategies to help you avoid Trojan attacks. Since being extra careful can only take you so far, implement these methods to protect yourself from Trojan virus attacks.

🧰Use Anti-Malware and Antivirus Tools
Anyone can fall victim to a cyber attack that installs a Trojan or other viruses, malware, spyware, ransomware, worms, rootkits, etc.
You can't stop cybercriminals from attacking you, but you can protect your system by installing Trojan Remover Options. They'll safeguard you from possible threats and eliminate them immediately.
🧰Regularly Update All Programs
Trojans can sometimes hide inside the installation folder of specific programs and apps. They can perform actions on your computer from there.
By regularly updating all your programs and OS, you can keep yourself safe from possible threats and unfamiliar files.
🧰Use Firewall Protection
A firewall is your first line of defense. It monitors the traffic to and from your network to allow or deny access. It can be an excellent shield preventing Trojans from infiltrating your computer.
Thus, configure a firewall correctly. It will filter your traffic according to your set security rules.
🧰Practice Safe Habits on Social Media and Email
You may be tired of hearing this advice, but it's crucial. Users get too comfortable online nowadays and don't think about possible threats. When using social media and email, never click illegitimate Image names, open suspicious messages, or download unnecessary and random files. Always stay safe online.
🧰Browse the Web Safely to Avoid Trojan Virus Attacks
Besides email and social media, Trojan horse viruses can infect your computer from your browser. Thus, practice safe web browsing habits.
Avoid suspicious websites, especially if they don't have secure HTTPS connections. Moreover, be careful with pop-up ads and random downloads.
🧰Use Authentication Tools
Another way to protect your data and accounts is to use multi-factor authentication (MFA) tools. Some two-factor authentication (2FA) tools include ID cards and PINs, and some send a verification code to your email or as a text message.
Moreover, some authentication tools will ask you to set personal questions and answers that only you know to ensure no one can access your accounts and data.
What to Do After a Trojan Horse Virus Attack
What can you do if you've already suffered a Trojan horse attack? First, don't panic; you can fix the damage.
We've prepared the six best strategies about how to get rid of trojan viruses. Follow our instructions, and you'll remove the trojan virus and fix the damage it has inflicted on your computer.
🎯Isolate Infected Devices
If a Trojan horse virus infects your computer, stop the further spread of the malware immediately. If you isolate your Trojan horse virus-infected device, you can prevent it from spreading through the network and causing additional damage.
Follow these steps to isolate your infected devices:
- Disconnect and physically separate your device from the network.
- Turn off Wi-Fi.
- Remove external devices.
🎯Scan Your Devices
Once you isolate your infected computer, you must scan it for Trojan horse viruses. Install reliable anti-malware software and scan your device for Trojans. However, it's more critical to check your other devices for Trojan infections.
Since a Trojan horse virus can spread via the network, scan all your other connected devices. Download anti-malware on each and thoroughly check them. If they detect Trojans, you must isolate those devices, too.
However, if you act quickly enough, your other devices will probably be safe and Trojan-free. Thus, you might only need to treat your infected computer or smartphone.
🎯Identify and Remove the Threat
Besides scanning your other devices for Trojans, you must fix the one you've isolated. You can remove the Trojan horse virus with anti-malware software. It lets you eliminate malware and sometimes uses real-time protection to identify threats promptly.
🎯Update Everything
As we mentioned, Trojan viruses often hide in installation folders of other programs. They can stay there unnoticed and spread infection throughout the system. However, if you update your apps, programs, and system regularly, you can efficiently eliminate Trojans.
Start by updating all programs and apps on your device. That can take time, but it's better to be thorough.
Then, update your operating system. While that usually extends to all installed programs, it's better to update all apps separately.
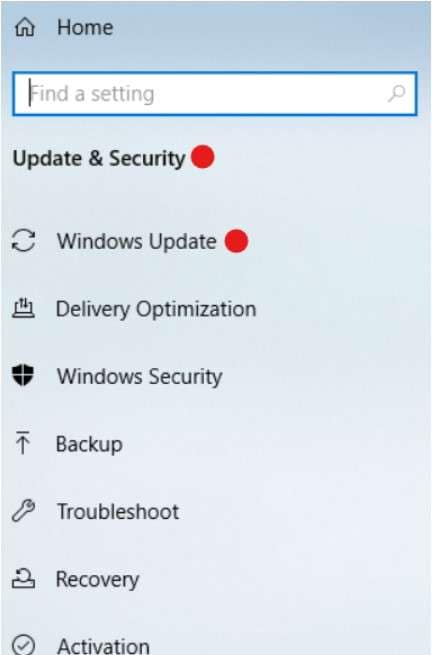
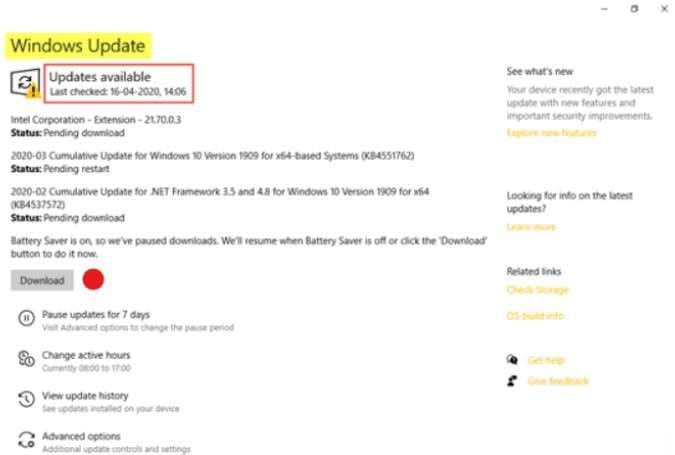
To update your Windows operating system, follow these steps:
- Click Start or press the Windows key and open Settings.
- Go to Update & Security and select Windows Update.
- Click Check for updates.
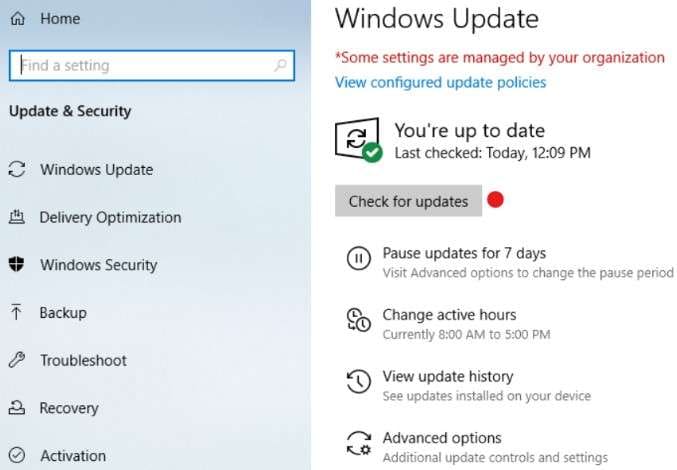
- If any updates are available, click Download and wait for the new Windows OS update to download and install.
🎯Recover Data
Don't worry if you notice a Trojan Horse virus attack that has the intention of deleting your files. Your deleted files aren't lost forever. You can use a reliable data recovery tool like Wondershare Recoverit to restore lost files in a few clicks.
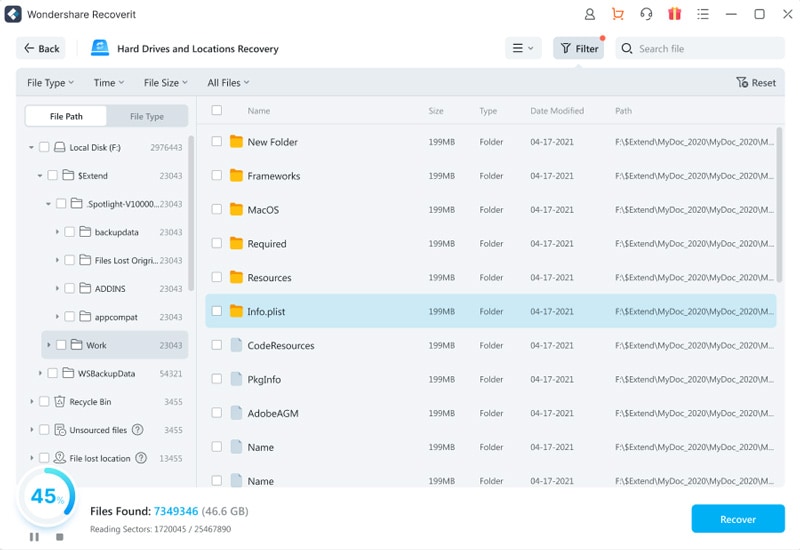
Wondershare Recoverit can recover lost files from virus-infected hard drives within a few seconds. Follow these steps to retrieve data from a Trojan virus-infected computer using Wondershare Recoverit:
- Install and launch Wondershare Recoverit on your computer.
- Go to Hard Drives and Locations. Click Start and select the one storing your deleted files.

- The software will start an automatic scan of your chosen storage. You can monitor the process at the bottom of the screen, where you can pause or stop it.
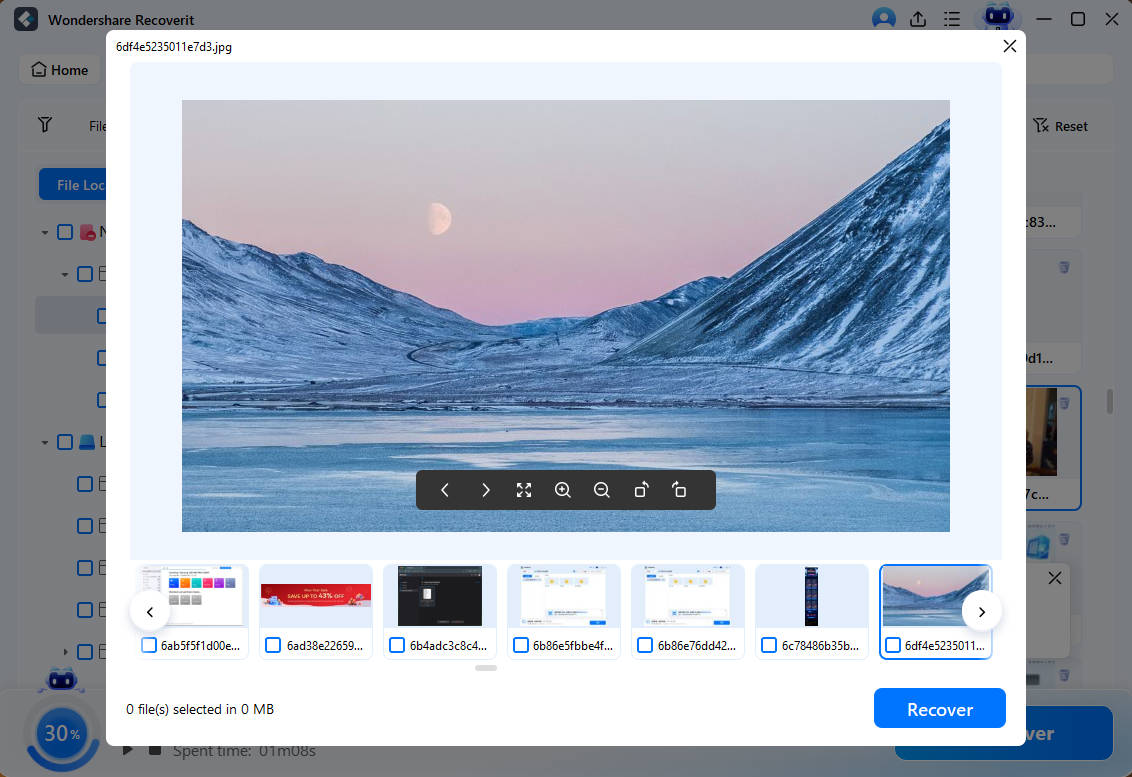
- Once the scan is complete, preview the recoverable files and click Recover. Save them to a safe location to avoid losing them again.
🎯Change Passwords
Changing your passwords can help you put the privacy walls back up and protect your data from a Trojan virus. If a Trojan has already infiltrated your accounts, a password change will withdraw its access and evict it from your computer.
When you change your passwords for social media, email, cloud, and other accounts, use different passwords for each. Ensure they have over ten characters, including numbers, symbols, and lowercase and uppercase letters, and mean something only you would know. Lastly, never save them in your browser or a document on your computer.
Conclusion
A Trojan horse virus masks itself as a legitimate app or file and steals information from your computer undetected. If a Trojan horse virus infects your computer, you may experience data loss, information theft, spying, and remote meddling with your system performance.
Therefore, knowing how to remove a Trojan virus is critical for safeguarding data. If your computer gets a Trojan infection, isolate it, scan all your devices, identify and remove the Trojan virus, and change your password for further safety. Then, use Wondershare Recoverit to recover deleted files due to the Trojan infection.
FAQ
Can I delete a Trojan horse virus?
You can delete a Trojan horse virus. However, you can only do it if you can detect it. Thus, if your anti-malware software can catch a Trojan on your computer, it will isolate and eliminate it from your system.Is a Trojan virus a virus?
While a Trojan horse virus is called a virus, it's malware. A virus can self-replicate and spread through the system by attaching itself to another program. A Trojan horse is malware that sneaks into your system as part of a program or legitimate file.Can Trojan viruses infect mobile phones?
Trojan horse viruses can infect mobile phones. You might download one to your phone via an SMS, email, or files from suspicious websites.