While learning about destructive computer viruses is a topic many computer enthusiasts find interesting, only a handful of these fans have heard of the CIH computer virus. Its name doesn't often appear on the top lists, yet this havoc-wreaking menace has infected millions of computers at one point.
We will delve deeper into the CIH virus' history, operation, and destructiveness. We'll discuss how this destructive program came into existence in the late 1990s, show you how it works and what you need to remove it, and summarize what we learn from this menace.
In this article
What Is a CIH Virus?
CIH virus is a computer program that overwrites critical information on infected computers, often going as far as to destroy the system's BIOS. At one point, it spread to more than 60 million worldwide computers, resulting in massive data and commercial damages.
This destructive menace first appeared in 1998, and its famous nickname, the Chernobyl Virus, is closely related to its creation and trigger dates. Namely, when this virus first infected computers, it would lay dormant on infected systems for precisely one year.
Then, one year later, it would activate itself and wreak havoc on the computer, overwriting files and penetrating unprotected BIOS chips. However, the first-ever trigger date was April 26, 1999, coincidentally matching the date of the 1986 Chernobyl nuclear reactor meltdown.

The CIH computer virus was made by Chen Ing-hau, a coding prodigy from Taiwan and a student at Tatung University at the time. After his apprehension, Chen stated that he created the virus as a challenge, one that would prove to arrogant antivirus companies that their defenses were weak.
After spreading the virus at his university, Chen realized the mistake he had made, apologizing to the university for the chaos he had caused. He then started co-writing an antivirus program with another student, Weng Shi-hao, that would stop the spread of the CIH virus and remove it from infected machines.
How the CIH Computer Virus Works
Now that we know more about the history and the creator of the CIH computer virus, we can delve deeper into how this infectious menace operates. Keep reading to learn more about the CIH computer virus's attack plan and the devastating mark it left on infected machines, as we'll jump right in.

After infecting a computer, the CIH virus would, as mentioned, lay dormant on the infected system for an entire year. Since its beginnings in 1998, the chaotic piece of code had found itself on thousands of computers before activating on April 26, 1999, which we now know was its first trigger date.
Upon the first activation, the CIH virus would wreak havoc by spreading through executable files. Each click to open an .EXE file would spread the CIH virus further, letting it nest in another program's free space inside the code, hence another one of its nicknames – Spacefiller. This component allowed the CIH computer virus to stay hidden longer than many other destructive programs of the era.
From there, the virus would activate its chaotic component, corrupting files and spreading further. It would render computer apps and other files useless and then move on to the computer's boot drive, filling it with zeros and ones to make your operating system unusable.
Moreover, any flash BIOS chip that wasn't protected with a jumper would also get infected, often making the entire computer inoperable.
How to Disable the CIH Virus
Dealing with the CIH virus in the late 1990s was a nightmare. Computer users had no idea what they were up against, quickly losing their vital files and being left with an unbootable OS or an entirely useless computer that wouldn't even turn on again.

While the CIH virus only infected Windows 95 and Windows 98 computers, various versions of this destructive computer program also appeared later. These versions, as well as many other viruses, also exist for Windows 10 and 11. Thus it's imperative to having a full arsenal of practical ways to eliminate this menace:
- Identify the Virus – Knowing what virus infects your computer is the first, paramount step in effectively treating the infection. You'll need to use a dedicated antivirus scan application that can efficiently monitor your system and recognize the virus by comparing it to known applications in its database.
- Disconnect the Infected Computer – Since the CIH virus can spread through .EXE and .SCR files, removing peripheral devices like USBs and external storage drives and disconnecting the machine from the network is a vital step in decreasing the spread of this menacing infection.
- Restore the BIOS – More often than not, the virus would spread to the infected computer's flash BIOS chip, burrowing itself there and making the machine inoperable. If that happens, the only way to restore your computer's functionality is to restore the BIOS chip's contents.
- Regain Access to Windows and Install Security Apps – After restoring the computer's BIOS, you can use Windows recovery discs and USBs to restore the operating system's boot sector and load up your Windows installation. At that point, you can install antivirus software and malware removal tools.
- Remove the Infectious Virus – Once you have dependable and dedicated antivirus tools, you can move on to removing the infectious application and restoring order to your Windows operating system. Using multiple antivirus tools is highly recommended during this step.
- Uninstall Malicious Tools – Although unlikely, the CIH virus might have infiltrated various other applications on your computer or installed additional malicious programs on your machine. These must also be removed entirely, and antivirus software can significantly help during this step.
- Check the Entire System – When you remove the CIH virus and the corrupted apps, you should run antivirus scanning apps again to confirm that your computer is clear of the destructive virus and any of its malicious components that can cause chaos to your data.
What We Learned Because of the CIH Virus
The reason why the CIH virus doesn't appear on many lists of the most dangerous computer viruses is that it was only active in the late 1990s, and its creator helped make the solution for it. However, the CIH virus and its successors also represent a valuable lesson regarding cybersecurity, viruses, and malware .
Growth of Cybersecurity Awareness
Before the CIH virus, not much was known about the constant threat lurking in the online realm. Blissful ignorance was at its peak, and computer enthusiasts happily browsed the web without a worry in the world. However, the appearance and spread of the CIH computer virus violently changed the online world.
Both independent web surfers and billion-dollar companies started taking cybersecurity far more seriously. Users were now more aware and cautious about the websites they visited, files they downloaded, and Image names they clicked. There was also a massive rise in sales of antivirus software and malware removal tools. Everyone downloaded these apps to protect their vital data.
Businesses also started investing heavily in cybersecurity teams and research and development programs for protection against malware. Security research jobs soared, and new company policies were introduced where these researchers could report security holes in the company's defenses.
Responsible Disclosure
While the term Responsible Disclosure might sound unfamiliar, it's practically a policy that helps companies deal with vulnerabilities or bugs in their systems. Namely, when a security researcher finds a hole in your application, they're legally obligated to report it by contacting your company.
However, if a company's security team doesn't reach back or ignores the bug, the security researcher might turn to the public and publish the vulnerability they've discovered. This policy is known as a Full Disclosure, and it puts unnecessary strain on the company's security team, where they're likely to run around trying to patch the app's vulnerability in panic.
To avoid that, various companies implement a Responsible Disclosure policy, where independent researchers can quickly contact the business' security team and effectively report breaches without causing panic or notifying the public. That way, the company can calmly initiate the patching process without worrying too much about negative press or potential hacks.
Importance of Keeping Data Safe
Computer viruses and malware are a constant threat in the online world, causing great chaos. Moreover, they also pose a substantial risk to the integrity and safety of your vital data.
Fortunately, professional data recovery tools exist and work wonders in these types of situations. Wondershare Recoverit is one such application, and it'll allow you to recover your precious files in case of a malware infection, even if you find yourself without a backup.
Wondershare Recoverit's detailed scan and recovery algorithm makes finding files lost in malware attacks a piece of cake. Within minutes, the app will find and retrieve photos, music, documents, and videos you hold dear, as it supports over 1,000 file types and 2,000 storage devices.
Here's what you should do:
- Launch the app and click on Hard Drives and Locations.
- Select the infected disk drive. (In most cases, it'll be the operating system disk, but you might need to run Wondershare Recoverit on other disk drives if the infection has spread.

- The app will immediately begin scanning the selected drive for lost files.
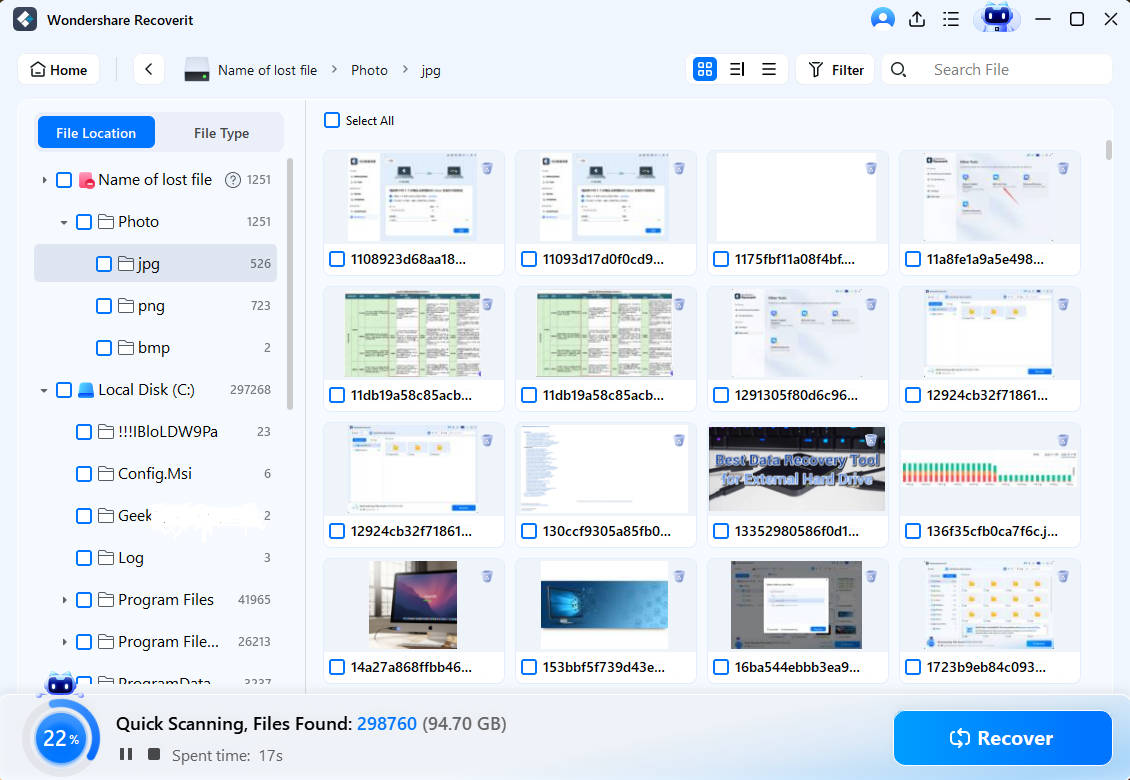
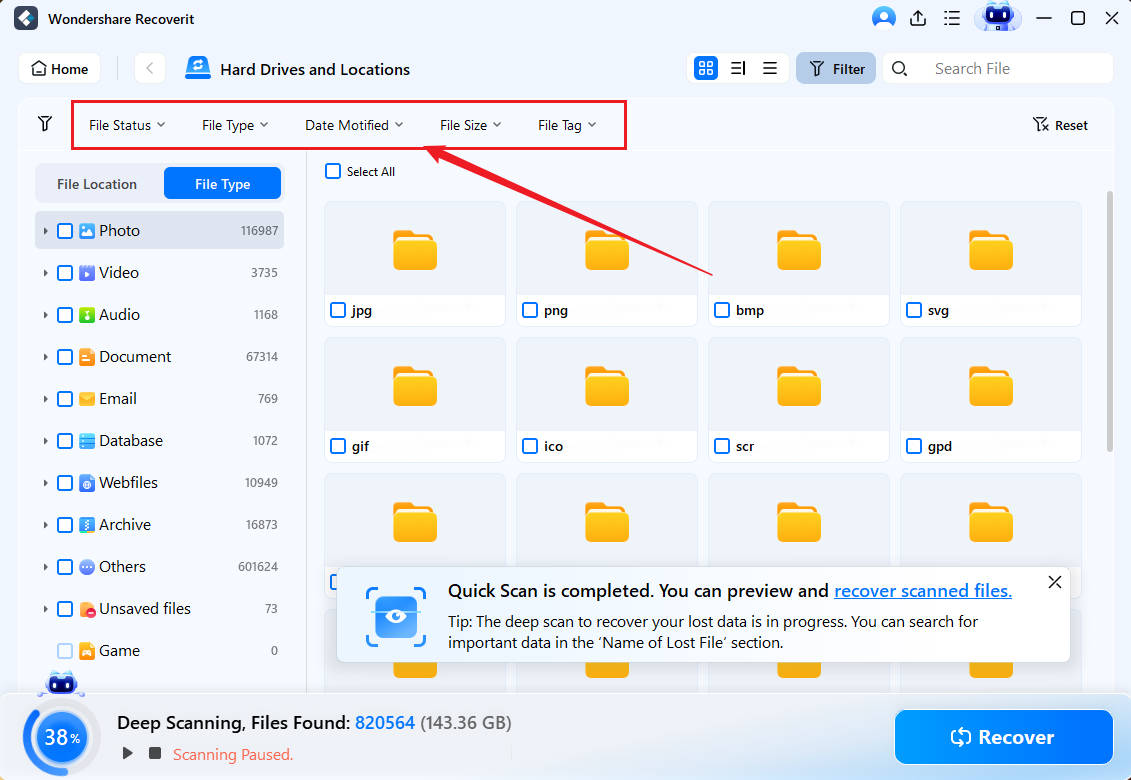
- Adding file size and type filters can help speed up the scan, while adding keywords can help search for specific files.
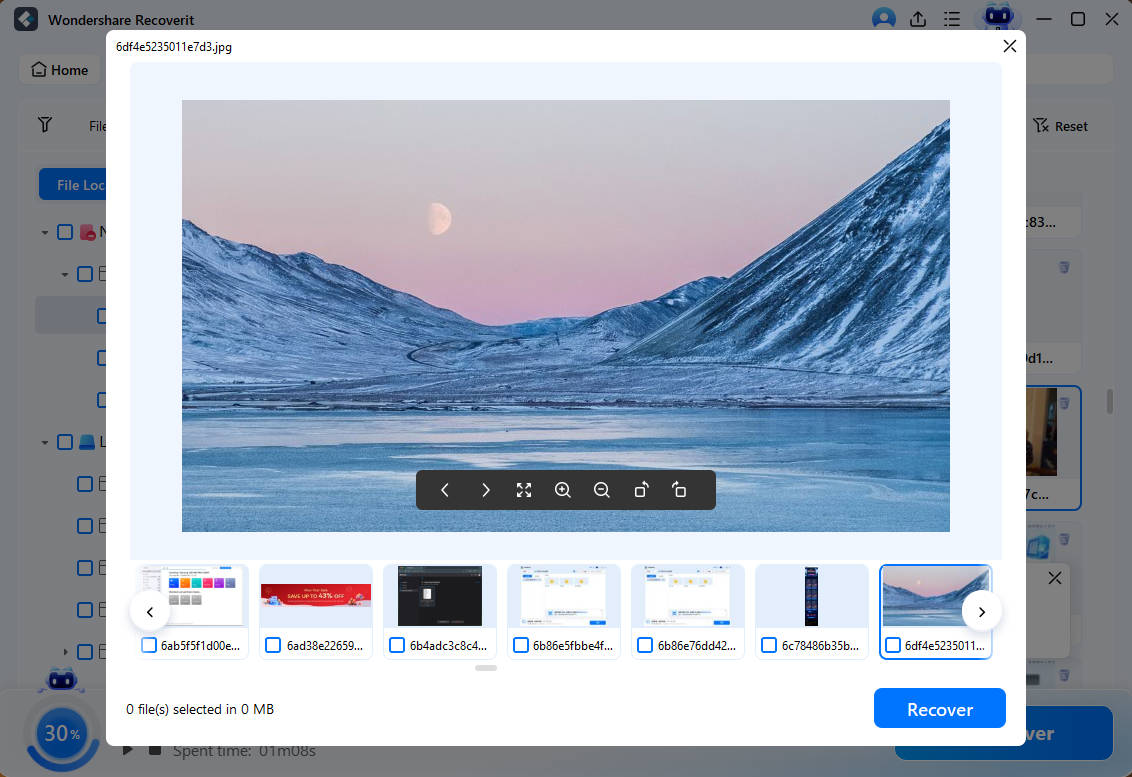
- The preview feature lets you verify the discovered files before recovering them.
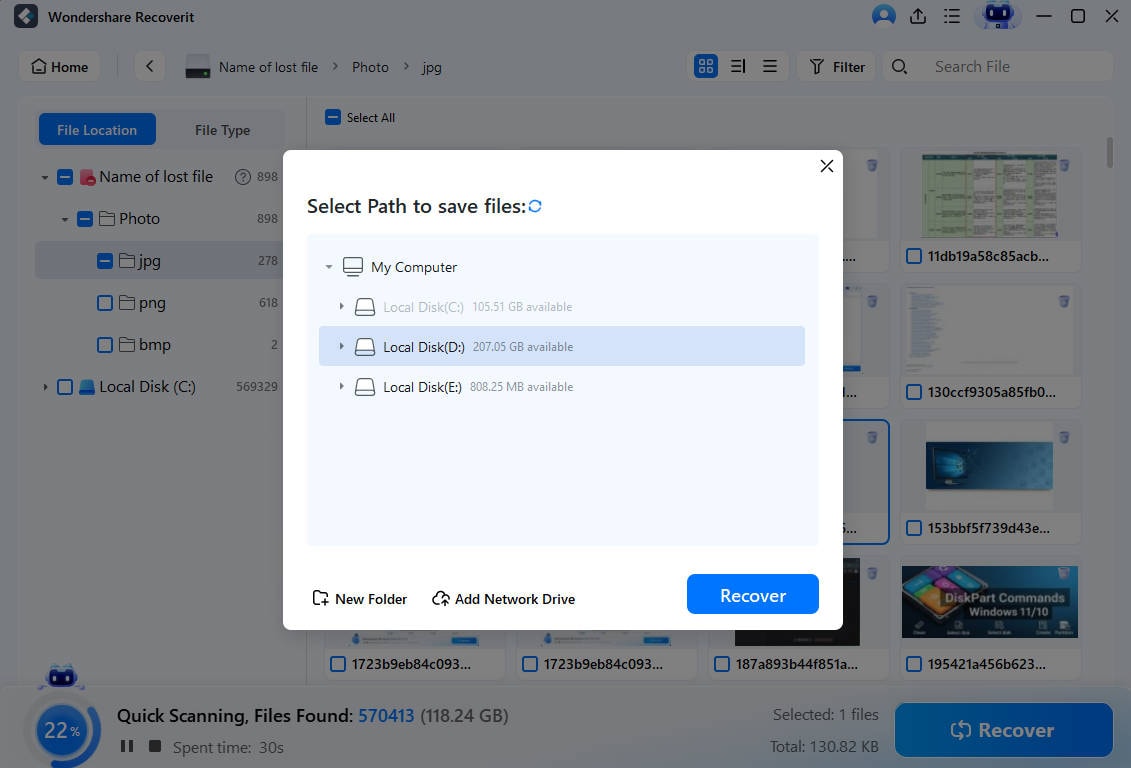
- If you're satisfied with the found data, you can pause or stop the scan and recover the files the app has found by clicking the Recover button.
Conclusion
The CIH computer virus caused chaos in the late 1990s, leading to billions of dollars in damages and massive data loss. Its appearance marked a turning point in cybersecurity awareness, which soared after users and businesses saw the catastrophic consequences of this destructive tool. Companies introduced Responsible Disclosure policies where independent security researchers could report their findings.
Since that day, the constant online threat has remained active and led to the rise of data recovery tools, like Wondershare Recoverit, which can retrieve your vital data in case of a virus infection.
FAQ
How can I notice the symptoms of a computer virus infection?
While various computer viruses act differently, the first symptoms appear similar in many malware infections. For example, malicious tasks may appear in your computer's Task Manager.
Recognizing the background tasks that should and shouldn't be on your computer is vital for identifying the first signs of a computer infection. Many computer viruses also fill your storage drives with garbage, and you might notice that your HDD or SSD is getting filled at an alarming rate.
Can I remove the virus from the computer's BIOS?
A handful of malware apps can burrow into your PC's most basic software – BIOS, making these firmware viruses even more dangerous and difficult to remove. Antivirus software often doesn't even find these, as many only check the operating system.
To eliminate them, you'll need to remove your computer's disk drives and use a BIOS flashing tool from the motherboard manufacturer's website, which you can then put on a CD or a USB and reflash the BIOS to the latest stable version.
-
What other computer viruses and malware should I be aware of?
Although we've mentioned a few examples of dangerous computer programs that can replicate and wreak havoc on an infected system, there are even more of these lurking in the online corners. For instance, worms like Code Red, Sobig, and Storm Worm, as well as ransomware like Locky, CryptoLocker, and WannaCry, are all worth mentioning.
Regardless of the infection you experience, the virus elimination process remains similar to the one we've included above.



 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















