Computer viruses pose a significant risk to your system's health and data safety. Some even attack your sensitive information, devastatingly affecting your finances, with the Clampi virus being among the most feared ones.
This malicious tool has been around since the 2000s and, along with its later variants, has caused billions of dollars in damages worldwide.
Today, we'll investigate the infamous Clampi computer virus, see how it works, and show you how to detect and remove the malicious code. Moreover, we'll also provide tips on minimizing the effects of the virus and reducing the risk of computer infection in the first place.
In this article
What Is the Clampi Computer Virus?
In essence, the Clampi virus is a sophisticated form of malware hackers use to exploit computer users financially. This Trojan horse type of virus acts as a man-in-the-browser, hiding behind firewalls and noting your login credentials. It specializes in stealing financial information and is known in the digital world as a banking trojan.
The original Clampi virus appeared in the mid-2000s but has experienced various modifications and evolved alongside the digital landscape. Several variants of the Clampi computer virus exist today, targeting Microsoft Windows users and infiltrating operating systems from Windows XP to Windows 11.

As the cybersecurity industry evolved, so did the Clampi virus, changing its behavior, disguising itself as different genuine Windows services, and shifting its tactics. Today, most iterations of the Clampi virus affect the web browser app, taking control of its settings and redirecting users to inconspicuous yet malicious websites or changing security settings.
In most cases, hackers controlling the Clampi virus target financial institutions like banks. However, individuals are also at risk, as the trojan virus can often hide even on trusted websites. Once it infects, it spreads on unsecured networks, finding outdated software vulnerabilities on unsuspecting users' computers.
How the Clampi Computer Virus Works
Understanding how this trojan horse functions is paramount in detecting, removing, and protecting yourself from the virus and its evolving versions. We'll immediately dive deeper into how the Clampi computer virus works, investigating first how it infects Microsoft Windows computers and then examining the malicious code's effect on user data.

How the Clampi Virus Infects Devices
When it first appeared in the 2000s, the Clampi virus wreaked havoc through phishing scams, often finding itself as an attachment in malicious emails. Today, more evolved Clampi variants spread on social media websites and through downloadable media files, infecting unsuspicious users and camouflaging as various Microsoft processes inside the Task Manager.
Some versions of the Clampi computer virus act as virus-removal tools. These scam apps steal money by warning computer users of a fake malware infection, scaring them into downloading additional malware or purchasing an expensive cleaning tool. Many of these scareware then stay on the computer, generating further warnings and exploiting the user multiple times.
Malicious Effects of the Clampi Virus
Once it infects your Windows computer, the Clampi virus waits for your input, mainly looking for financial information. It hides deep in the computer system, waiting for you to sign onto an e-banking website or make an online purchase where you must add your credit or debit card info along with the expiration date and CVV.
The virus is intelligent enough to recognize financial information from countless other words you type in or messages you send. It then logs your sensitive data as soon as you enter your username and password, immediately sending it to the hackers that infected your computer in the first place through the trojan's control and command servers and numerous open backchannels.
From there, these hackers can use your financial credentials to make purchases, having direct access to your entire e-banking system. With these credentials, they can do whatever they want, with many Clampi infections going as far as full-on identity theft.
However, most cybercriminals use the Clampi virus to slowly drain bank accounts over time, hoping the computer owner overlooks the smaller trades.
How to Detect and Remove the Clampi Virus
While incredibly sophisticated and capable of hiding itself in the darkest corners of your computer system, the Clampi virus is detectable with the right tools. If you suspect this malicious piece of code has infiltrated your operating system, there are ways of detecting and eliminating it, and the help comes in the form of these tools.
Use Firewall and Intrusion Detection Tools
A Firewall is one of the first defenses you have against malicious pieces of code that can wreak havoc on your computer. Using one and correctly setting it up are pivotal steps for defending your data against the threat of digital viruses.

However, it's worth noting that the Clampi computer virus isn't as easy to detect as you might think. It's intelligent enough to hide behind a firewall, so using dedicated intrusion detection tools alongside is highly advised.
These network security apps monitor your internet traffic for suspicious activity, reporting anything they find to the network admin. They're instrumental in companies and offices, and the admin can set up specific rules based on what an Intrusion Detection System (IDS) finds. From there on, an IDS can take appropriate action against the threat.
Use Antivirus Software
Dedicated antivirus software from a reputable security company is one of the pillars of the defense against internet threats. They're often fitted with heuristic scanners, behavioral analysis tools, and databases of known malicious programs. As such, antivirus tools are instrumental in keeping your data safe.
Regularly using an antivirus and scanning your computer's files will keep your sensitive data private by finding and eliminating suspicious tools and malicious apps. It's a highly recommended practice, especially if you notice anything unusual or see files you can't remember making or downloading.

With these tools in your arsenal, detecting viruses in your computer system will be a piece of cake. Removing them will also only require a few seconds of your time. However, prevention is better than cure, and there are things you can do to avoid virus infections in the first place.
How to Minimize the Effects of Clampi Computer Virus Attacks
Deterring the infiltration of the Clampi computer virus, its many variants, and other known computer viruses is possible. Below is a list of some of the best tips to avoid infections and minimize the effects of the Clampi virus.
Clean and Isolate Systems
Most Windows users don't regularly clean their computer systems. Once they install the OS, such users keep piling up applications, making it incredibly challenging to keep track of what app does what.
Environments like these are a perfect target for the Clampi virus and other similar malicious tools to thrive, as it's nearly impossible to detect the destructive app in a sea of services once you open up Task Manager.
Instead of letting that happen, regularly cleaning your system from unnecessary programs and occasionally refreshing your Windows installation is highly advisable, as you can keep track of what's what, making it easier to detect suspicious tools.
Update Software Regularly
Bad players prowl for vulnerabilities, unpatched security issues, and ancient systems. Hence, an outdated computer is a prime target for these hackers and malicious coders, as such systems are full of security holes they can use to infiltrate your system, steal your data, and cause chaos.
If you don't regularly update your antivirus tool, an outdated antivirus program likely won't recognize the behavior of new malware and can't detect it. Without the latest updates, more recent internet threats will fly past your defenses as if you didn't have any.

Therefore, regularly updating your operating system and checking for new versions of your daily apps are pivotal to protecting against clampi and other viruses. Set reminders and write notes or add the practice to your weekly or monthly routine, as it's instrumental.
Authentication Strategies
As mentioned, the Clampi computer virus waits for logins. The malicious program sits hidden, waiting for users to input their username and password, access e-banking websites, or purchase goods online. Such actions give hackers your financial credentials, and they can easily use them on other websites, making small purchases and slowly draining your bank account.
In this case, enabling two-step or even multi-step authentication can make things much more difficult for these bad players. Even if they get your financial information or access your credit card details, they can't make purchases without SMS codes or confirmation from an authentication app on your phone.
That's why, various top-of-the-line authentication strategies, such as SMS verification or a dedicated mobile authentication app, are highly advisable. The only way these can be penetrated is if the hacker also gets access to your phone, which won't happen with the Clampi virus as it only runs on Windows.

Improve Network Security
While the Clampi virus doesn't work outside Windows, other digital threats might, and in that case, authentication apps won't help much as hackers can access your other devices like phones. Nonetheless, that can also be prevented by improving your network security and decreasing the chances of a virus infection spreading to other devices.
Using the WPA2-AES encryption standard and a robust alphanumeric password with special characters is highly recommended. At the same time, a network firewall plays a pivotal role in protecting against internet threats. Manually configuring it to block unauthorized access is vital, especially in larger companies with hundreds or thousands of connected PCs.
Businesses can also benefit from training their employees about the importance of passwords and should require that employees periodically change these. Seminars about attachments, emails, suspicious Image names, and good internet hygiene are vital to increasing the business's cybersecurity.
Use a Professional Recovery Tool
While the infamous Clampi computer virus functions as a man-in-the-browser Trojan horse that steals sensitive data, other digital threats are among the primary culprits behind data corruption. These malicious pieces of code cause chaos and corruption wherever they appear, and the user's data can quickly become the target in case of a computer infection.
Fortunately, data corruption is not as much of an issue as it used to be, as data recovery tools have evolved on the other side of digital advancements. These valuable apps have gotten incredibly good at their jobs, and Wondershare Recoverit is a prime example of such a helpful tool.
Although Wondershare Recoverit has an intuitive, beginner-friendly user interface that anyone can navigate, we've also included a detailed guide on using the app in data loss situations caused by malware attacks and computer virus infections. Below are the step-by-step instructions for using the app in such cases:
- Download and launch the Wondershare Recoverit app and select Hard Drives and Locations.
- Click on the infected disk drive. Usually, that's the operating system disk, but you'll likely need to use Wondershare Recoverit on other disk drives, too.

- The app initiates a thorough scan of the selected disk drive.
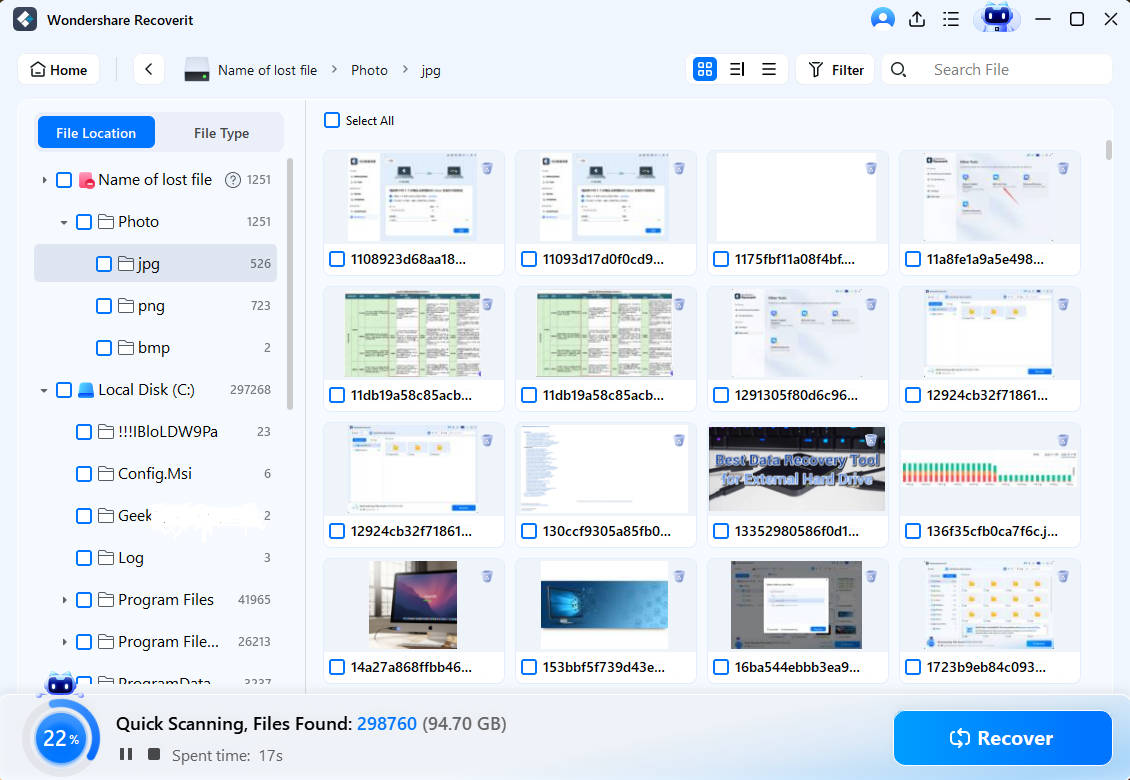
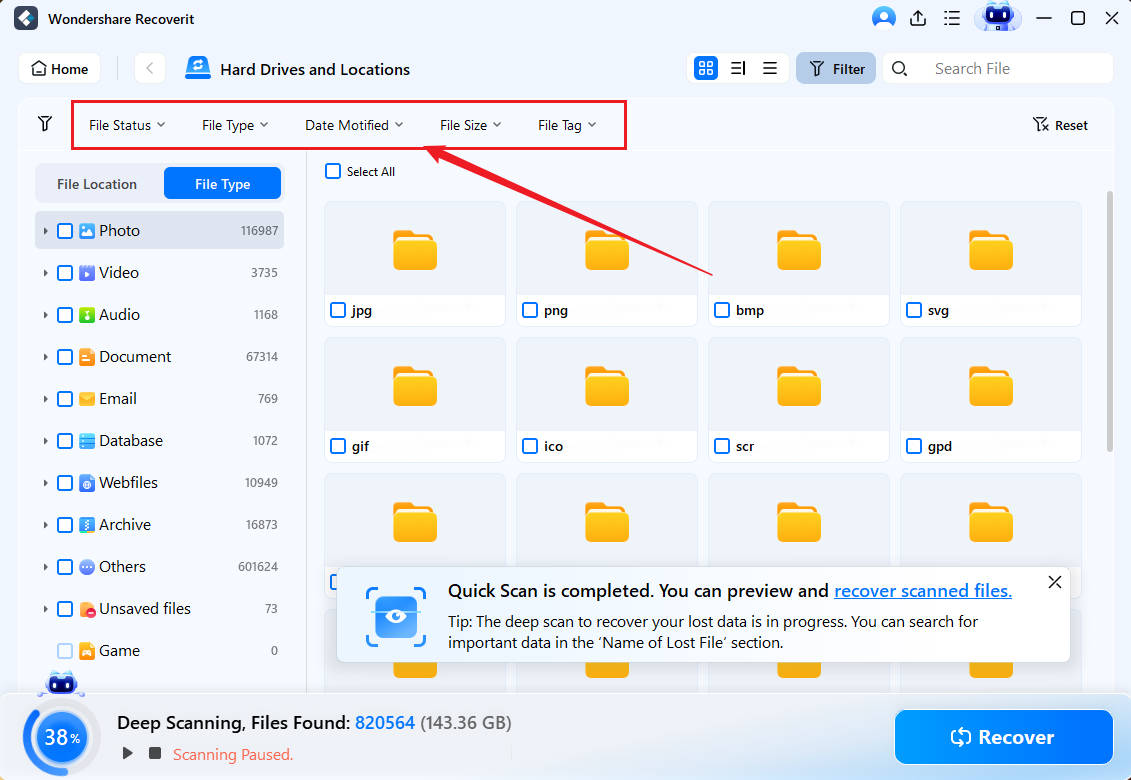
- You can help speed up the file scan by adding and adjusting file status, type, time, size, and tag filters.
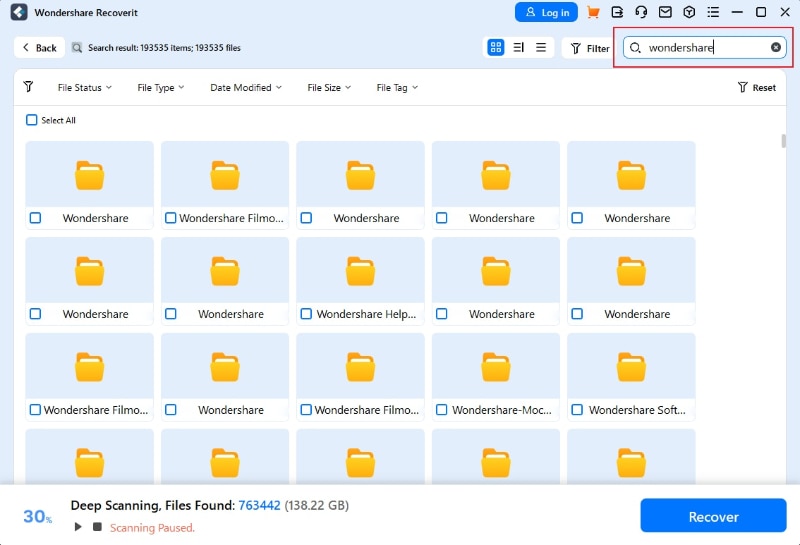
- You can also add keywords to help Wondershare Recoverit find specific files you're interested in.
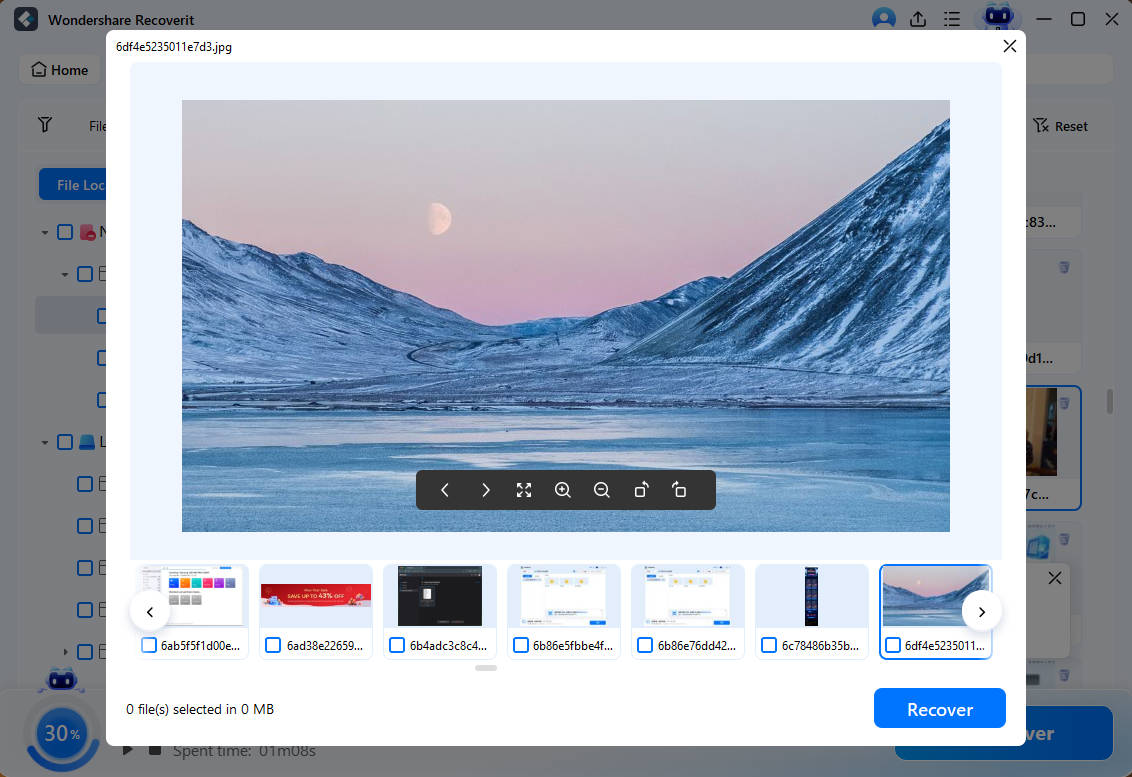
- Users can also preview the discovered files before recovering them.
- Once the scan finds what you're looking for, you can pause or stop it. Alternatively, you can let it finish and then click the Recover button to save the discovered files onto your PC.
You can have your precious files back in just a few short steps after virus or malware attacks.
Use a Reliable Backup Tool
The Clampi computer virus might not be as destructive as many of its colleagues, but it can still destroy your system by slowing it down, modifying files, and embedding itself in your data. At the same time, other computer viruses can cause even more chaos and destroy the contents of your hard drive, and you could quickly lose your precious files.
Creating and maintaining regular system backups is crucial in preventing such disasters. Fortunately, numerous backup apps can help with this, with Wondershare UBackit being a prime example of a reliable backup tool.
Using dedicated backup applications from trustworthy companies is an excellent idea, especially if dealing with multiple computers and mountains of valuable and sensitive data.
That way, you can set up scheduled backups for folders containing your most critical data, and the backup app will run in the background, creating incremental backups and keeping your files safe in case of a virus infiltration.
Conclusion
Known as a man-in-the-browser Trojan that steals login credentials, including financial information, the Clampi virus has been a severe threat since the 2000s. The virus hides, waiting for usernames and passwords, masquerading as various Windows apps and processes, and stealing financial logins, letting hackers slowly drain your bank account.
Detecting and removing the virus requires firewalls, intrusion detection systems, and reliable antivirus programs. Still, since preventing is undoubtedly better than treating, we've also included tips for avoiding infections.
These include regular updates, clean systems, adequate network security, multi-factor authentication, backups, and data recovery tools like Wondershare Recoverit to deal with corrupted files and the aftermath of the infection.
FAQ
What should I do after removing the Clampi computer virus?
After eliminating the threat and restoring a safe backup, you should contact your bank and review the purchase history to see if your e-banking logins have been used elsewhere. At the same time, once you're sure the Clampi virus has been removed, you should start changing your usernames and passwords for any accounts accessed on the infected computer.Is it possible to remove the Clampi trojan without installing additional software?
Yes. Tech-savvy users can eliminate the Clampi virus by finding infectious programs inside the Programs and Features tool or the browser's addons and uninstalling said software. From there, removing the Clampi virus would require identifying and eliminating any suspicious processes inside the Task Manager.Finally, the computer's Hosts file will likely require changing, and you'd probably need to remove rogue registries inside the Registry Editor.Can the Clampi virus affect macOS, iOS, Linux, or Android devices?
Fortunately, no. The Clampi computer virus is known to affect only Windows devices. Other Clampi variants also exclusively attack Windows machines, making it safer to do financial transactions on your Mac or mobile phone. However, that doesn't mean your Mac or phone is safe from all harm, as other digital menaces exist for these operating systems.



 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















