As antivirus software and anti-malware tools are constantly getting better at stopping computer infections, viruses are countering this by improving their disguise on your system. Some malware can even masquerade as legitimate system processes, such as csrss.exe.
Today, we'll delve deeper into csrss files and see how viruses and malware can wreak havoc disguised as vital Windows processes.
We'll explain what csrss.exe is, show you its characteristics and functions, teach you how to recognize legitimate background processes from csrss.exe trojans, and reveal how to defend yourself from such digital menaces.
In this article
What Is CSRSS.exe
The Client Server Runtime SubSystem Process, better known by its csrss.exe abbreviation, is an essential background process in Windows. It performs vital operating system functions. It's considered a critical process on Windows system machines, and you can find two Client Server Runtime Processes when you open the Task Manager and scroll down to Windows processes.
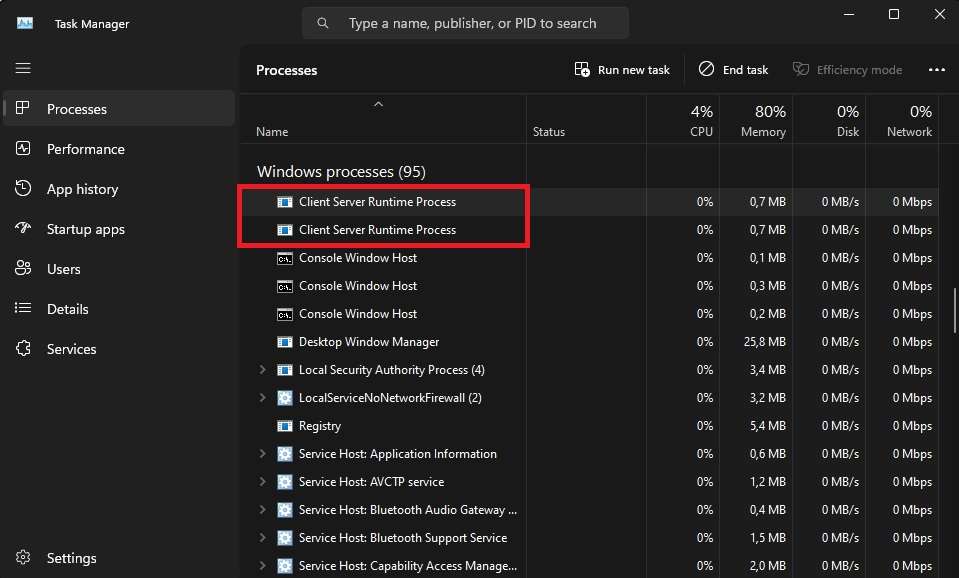
Characteristics of the Legit CSRSS.exe
Legitimate csrss.exe processes and those that handle vital Windows system functions will only use minimal resources, which can also be checked inside the Task Manager. These files will always function as the SYSTEM user, and opening their location will lead you to the System32 or SysWOW64 folders.
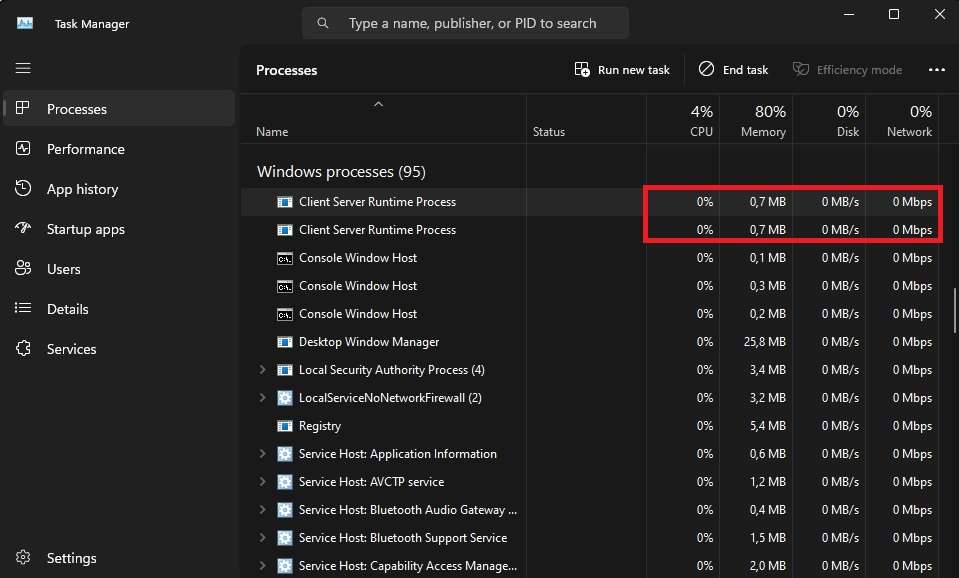
The csrss.exe handles different parts of the operating system that are vital for Windows' continuous operation. For example, it's used to launch other processes and threads, manage the command line, and shut down the system. These processes call upon various .dll files, which later handle the mentioned functions.
Characteristics of the Malicious CSRSS.exe
Noticing the use of excessive system resources or unusual behavior connected to these two processes means you're likely dealing with a trojan virus disguised as these system tasks. Viruses and malware on Windows systems are known to sneak in as legitimate Windows processes or have similar names.
Therefore, csrrs.exe or csrsr.exe are not genuine Windows processes and should be inspected in detail and terminated. At the same time, a csrss.exe that uses massive amounts of the CPU and GPU's power will likely be an infectious program that can wreak havoc inside your system.
Signs of Trojan Infection
Unfortunately, the name of these viruses implies that there's not much you can do to notice them. Trojan horse viruses, or trojans, are designed to infiltrate the computer as stealthily as possible. These viruses remain silent and don't show obvious computer virus infection signs.
Negative Effects
Since csrss.exe processes are connected to the Windows graphical user interface, infections within these files and trojans masquerading as them can lead to various visual issues. On top of the high load of the fake process, a csrss.exe trojan can also affect your graphics card's performance, or you may encounter problems with basic Windows functionality.
Even worse, while it's affecting your PC's performance, the csrss.exe also steals sensitive information. Your logins and private data can quickly fall into the wrong hands, leading to identity theft or financial loss.
How to Recognize a Legitimate CSRSS.exe
Due to their nature, trojans are challenging to identify and can silently cause chaos on your computer. However, the ones that use csrss.exe still have a few drawbacks, and if you suspect this is happening on your computer, there are steps you can take to verify the legitimacy of these background processes.
💻Verify Digital Signatures
All legitimate Windows system processes have digital signatures that Microsoft signs, and csrss.exe is no exception. Users can quickly check these digital signatures by following these steps:
- Open Task Manager by hitting CTRL + SHIFT + ESC on your keyboard.
- Find the two Client Server Runtime Process instances.
- Right-click on one of them and select Properties.

- Go onto the Digital Signatures tab and check whether "Microsoft Windows Publisher" appears under "Name of signer." You can also hit Details and View Certificate for additional information.

Once you confirm that Microsoft digitally signed the process, you can repeat the same steps for the other csrss.exe instance.
📃Verify File Integrity
As mentioned, legitimate csrss.exe background tasks can be found in only two folders inside your system's disk drive. These are System32 and SysWOW64, which you can verify by checking the file location of the two csrss.exe processes. Here's how:
- Hit CTRL + SHIFT + ESC to open Task Manager.
- Locate both Client Server Runtime Process tasks.
- Right-click one and choose Open file location.

- Repeat the first three steps for the other csrss.exe task.
If both background processes lead you to the abovementioned folders, you've verified these are legitimate Windows system processes. However, if that's not the case, you must deal with the disguised trojan virus.
🔋Look For Suspicious Resource Consumption
System resource consumption significantly rises when dealing with fake csrss.exe processes. You can identify trojans masquerading as legitimate Windows background tasks by looking into their CPU, RAM, Disk, and Network usage and watching for graphical anomalies on your PC.
In most cases, GPU usage is the first to spike, as csrss.exe is related to the Windows graphical user interface, but all five types of resources should be checked.
👀Identify Unusual Sessions
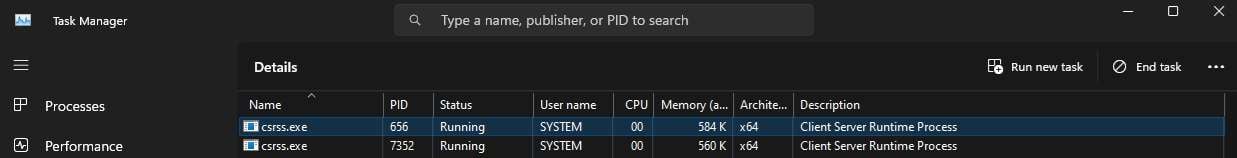
While there are two instances of the csrss file, only one is active per session, but when Windows loads, it always has two sessions – hence the two background tasks. However, both csrss tasks will run under the SYSTEM user name, and anything other than that indicates a fake process.
You can check this by right-clicking each csrss.exe and selecting Go to details or manually navigating to Task Manager's Details tab, locating the two csrss.exe processes, and verifying that "SYSTEM" appears under "User name" for both tasks.
How to Remove a CSRSS.exe Trojan
Because of its harmful effects, which include stealing data and reducing the computer's performance, removing the csrss.exe trojan is necessary as soon as you discover it. The process involves a few steps, which we'll cover below.
Uninstall Suspicious Programs
The first step involves the removal of any suspicious applications you might have on your PC, and you can use the Windows system's Programs and Features tool to remove such unwanted apps quickly.
- Open the Control Panel and navigate to Programs > Programs and Features.
- Select a suspicious app and hit Uninstall.

- Follow the uninstallation instructions and remove the app from your PC.
- Restart your computer afterward and recheck Programs and Features to ensure the apps aren't back.
Suppose you're unsure about the application's name or legitimacy. In that case, you can also look into the program's publisher, installation date, and size, which might indicate whether you're dealing with a legitimate app or a suspicious tool that the csrss.exe trojan might have installed.
Reset the Browser's Settings
Once you've removed suspicious programs, you can move on to your browser's settings, as the csrss.exe trojan is known to add malicious extensions, change default browser settings, or alter your homepage and bookmarks.
- Launch Google Chrome, hit the Three Dots button in the top right corner, and select Settings.

- Navigate to Reset settings on the left side and tap Reset settings to their original defaults.
- Confirm your choices by clicking Reset settings once more, which will remove cookies and extensions and change your homepage.

The steps for other browsers like Firefox, Opera, Safari, or Edge are similar, but you can also look for additional information online. Moreover, the aforementioned steps are vital in dealing with the csrss.exe trojan, as you might otherwise mistakenly visit a proper-looking page that steals your information.
Use Trustworthy Malware Removal Tools
Trojans are primarily quiet, running in the background without causing data damage. Still, they also leave the doors open for other malware, which can be incredibly destructive. Checking your system for malware and removing it after trojan removal are highly advised.
How to Protect Yourself From a CSRSS.exe Trojan
Although a trojan virus, like the csrss.exe trojan, often has no noticeable symptoms, it doesn't mean it's harmless.
Below are some of the best methods for increasing your computer's security, preventing csrss.exe trojans or similar viruses, and keeping your valuable data safe.
Update OS and Tools
Keeping your system up-to-date is crucial for remaining safe and preventing viruses and malware from exploiting the computer's zero-day exploits. That includes Windows operating system updates and the latest versions of tools you use daily.
Turning on automatic OS updates and letting Windows Update check for additional updates for the installed applications on your system is an excellent idea. You can also manually update your Windows system and use websites to download the latest versions of various apps simultaneously.
Use a Capable Antivirus
The rise of cybersecurity measures has led to the development of hundreds of antivirus tools. However, not all antivirus software is equal, and many free versions don't offer the same level of protection that a dedicated and capable antivirus tool can have.
Finding proper antivirus and anti-malware applications will require research and might be costly. Nevertheless, these tools are worth the money in the long run, as they can protect your private data from the harm caused by trojans, ransomware, and other viruses.
Scan for Viruses
While an installed tool and reliable antivirus software will prevent you from downloading viruses and malware or opening suspicious executable files on your system, these aren't enough to keep you safe. Malicious programs can still slip your computer's defenses, even with real-time protection active on your PC.
You'll have to develop the habit of regularly using the antivirus program and frequently scanning your system for potential infections. Such a task, although tedious, can help prevent computer infections and reduce the risk of possible data loss due to malware.
Examine and Isolate Suspicious Processes
Preventing the further spread of a computer virus and limiting its destructive effect is challenging. However, it's undoubtedly possible when you have the right tools and know what to do for different infection types.
If you've checked the two csrss.exe processes in Task Manager and realized something doesn't add up, it's time to examine these in detail and assess the situation quickly.
You'll also have to be quick and isolate the suspicious processes by disconnecting your computer from the network to prevent further spread of the infection.
Use the Disk Check Tool
The csrss.exe trojan and other types of malware can wreak havoc on your system, affecting critical files and causing various Windows functions. Fortunately, regaining these functions after trojan removal is possible, and you can use a built-in Windows feature called CHKDSK. Here's how:
- Hit the Windows key, type CMD, and launch the Command Prompt as admin.
- Enter the following command to scan your computer's disk drive:
sfc /scannow - Then, enter this command to initiate the CHKDSK function:
chkdsk /f /r
The CHKDSK command might take a while to check the entire disk drive. After it's done, you should restart your computer to apply any fixes or changes the command has made.
Recover Missing Files Using a Recovery Tool
Trojans are silent but destructive. These malicious apps can cause massive damage, with many of them affecting and corrupting your vital files. However, you're not helpless if you try to recover data in these situations.
One such tool is Wondershare Recoverit, and it works wonders in situations where viruses, malware, and trojans have led to data loss. The app's scan and recovery algorithm makes dealing with the aftermath of a trojan horse a piece of cake while using the app is incredibly simple.
We've included detailed instructions:
- Launch Wondershare Recover It on your PC and click on Hard Drives and Locations.
- Select the infected disk drives to start the data scan.

- Once you select the disk drive, the app will scan for lost data.
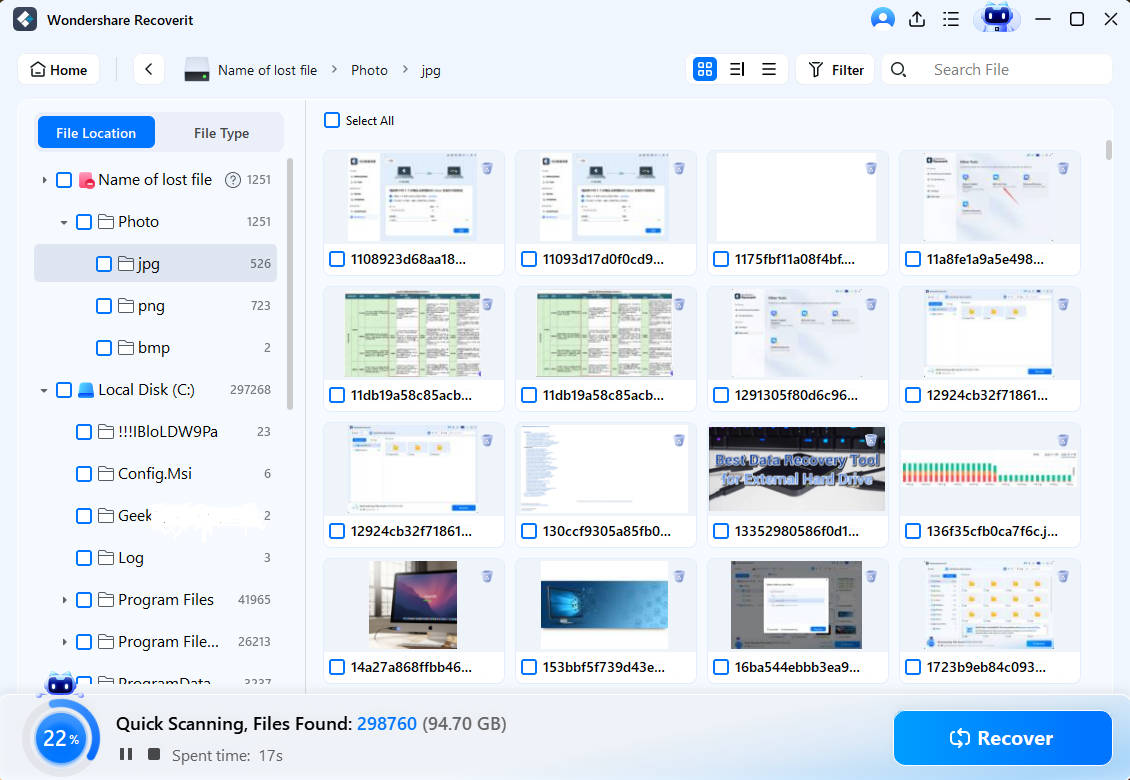
- You can speed up Wondershare Recoverit's scan process by adjusting the file size and type filters and adding keywords to look for specific files.
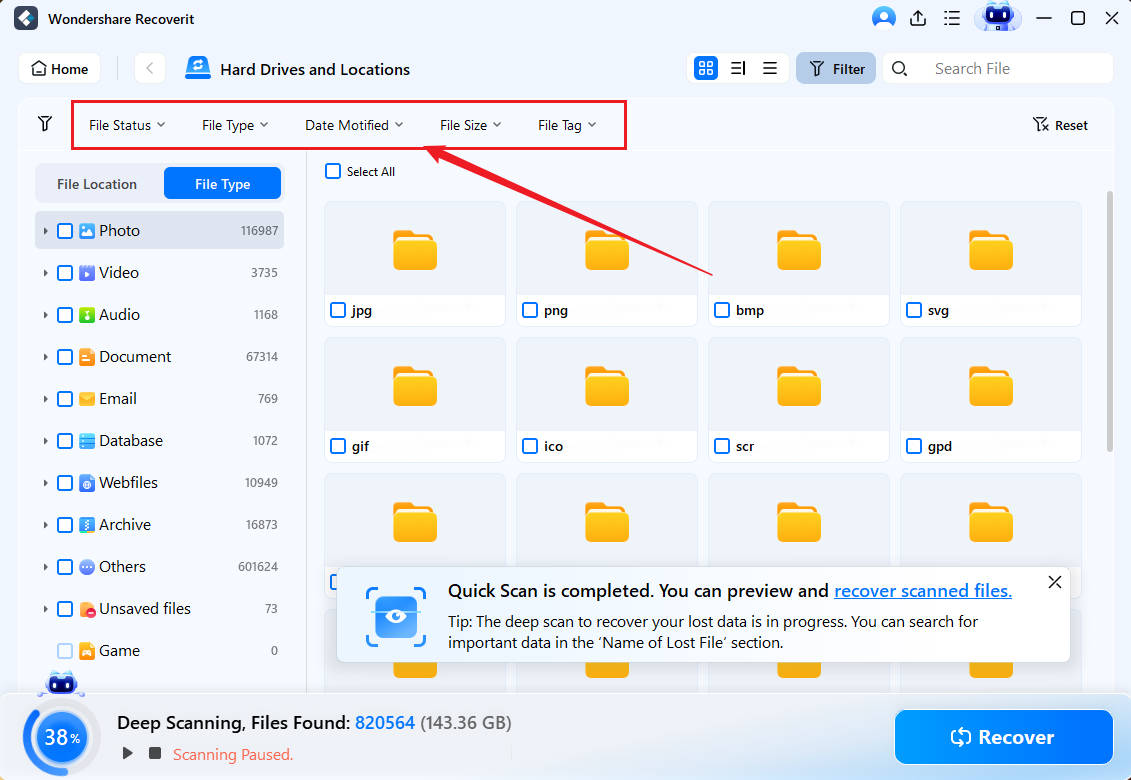
- Once it discovers lost files, Wondershare Recoverit will let you preview them.
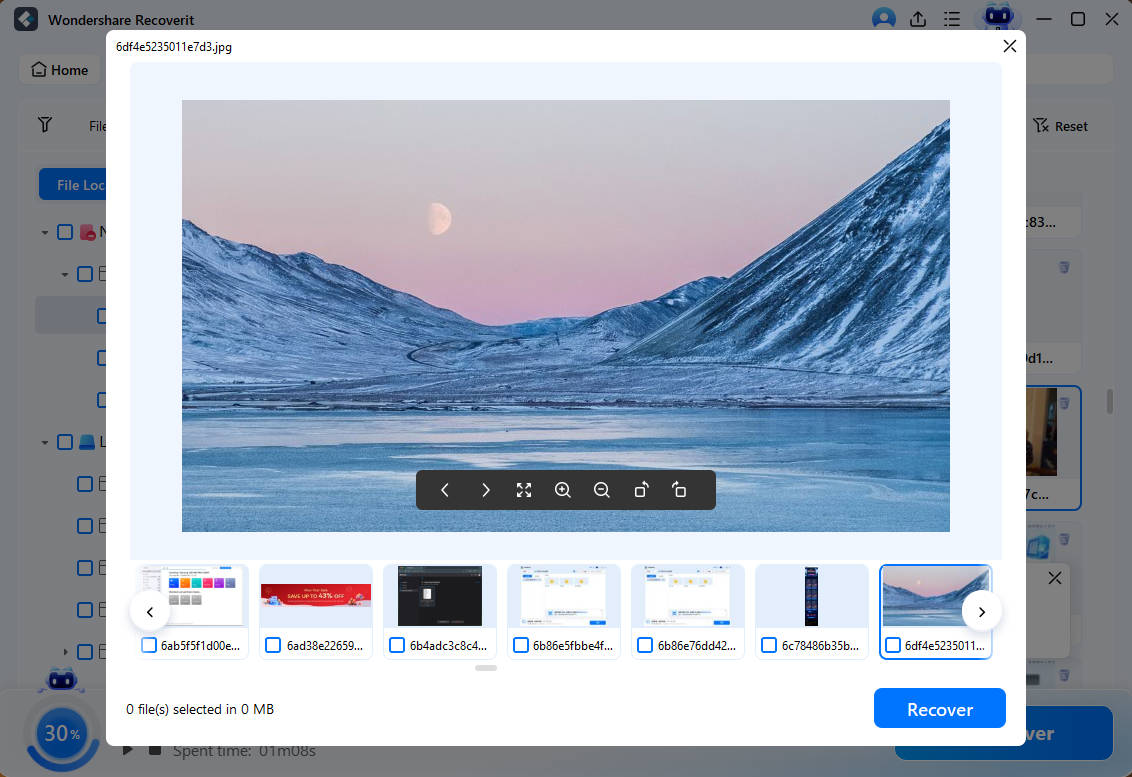
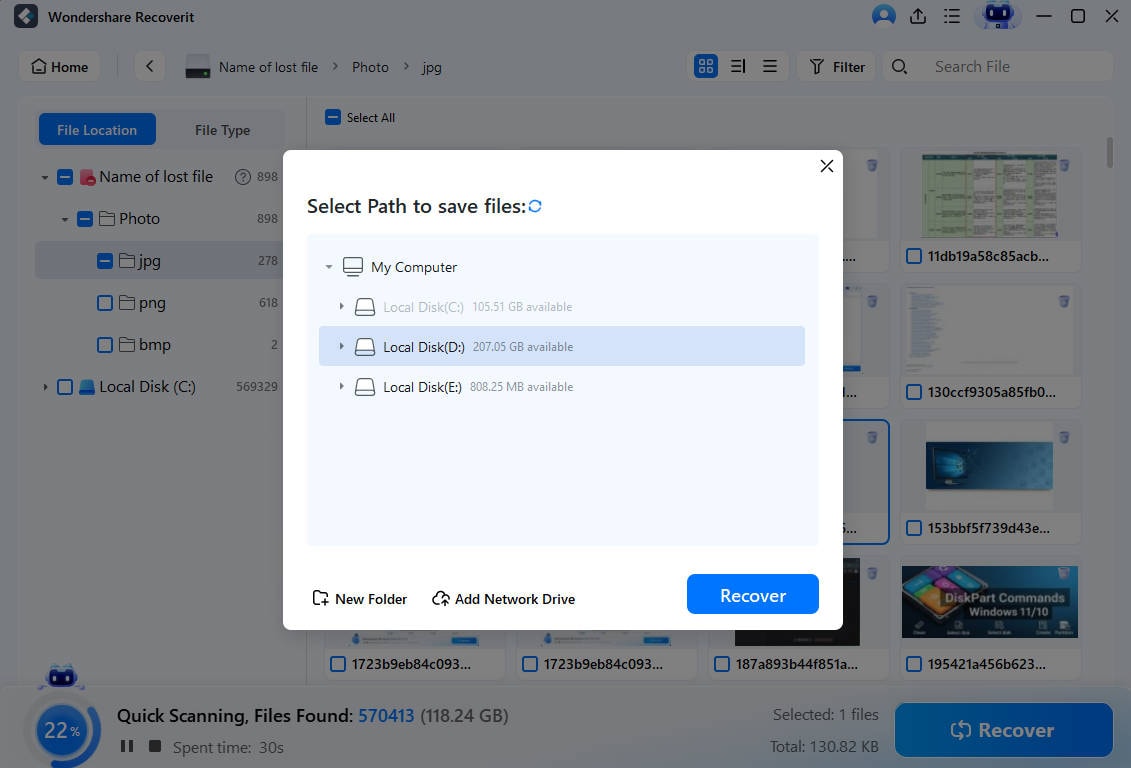
- When ready, you can pause or stop the scan and save the found data to a safe location.
It's worth mentioning that Wondershare Recoverit is far more capable than just dealing with computer infections. The app can be helpful in various data loss situations like accidental deletion, system crashes, failing disk drivers, interrupted transfers, etc.
Report Suspicious Activities
After you've dealt with the trojan virus, as a fellow internet surfer, you should warn other users to stay clear of the website or app that infected your PC. Reporting these platforms and suspicious activities you've encountered after visiting the website or downloading an app can help prevent further damage to other users.
Companies also have various policies regarding virus incidents, so if you've encountered a trojan on a company machine, you'll need to follow the business' incident response plan and notify the security team about the breach.
Finally, your country might have a dedicated cybersecurity department that deals with such digital threats. Researching such a team and reporting the virus to their email address is highly recommended, as they can take down malicious websites and apps.
Conclusion
The csrss.exe is a legitimate Windows process that often appears as two instances on Windows 7, 8, 10, and 11 computers. However, there's also a chance you're looking at a trojan horse virus disguised as a genuine system process, which you can also check by carefully inspecting the background task.
If inspecting the csrss.exe leads you to believe it's a malicious tool, you can use reliable antivirus software and malware removal tools to eliminate the trojan horse from your PC. After trojan removal, Windows' built-in CHKDSK tool can help regain basic Windows features and fix your disk drive, while Wondershare Recoverit can retrieve your vital files if they've been affected by the virus.
FAQ
Should I end the Client Server Runtime Process?
No. The csrss.exe is responsible for various vital Windows functions. Manually ending the process can cause these functions to glitch and stop working. It can also crash your Windows computer and generate a Blue Screen of Death with different error messages.Can I manually delete a trojan horse disguised as a csrss.exe?
Manually handling suspicious csrss.exe processes isn't recommended, as you could accidentally cause even more damage by terminating a genuine Windows system task. Even if you're positive that the third csrss.exe instance is a trojan horse, you should use an antivirus or a malware removal tool to handle the infection.What does the csrss.exe trojan do?
By masquerading as a genuine Windows system process and disguising itself as a csrss.exe, the trojan horse virus infecting your PC isn't particularly destructive regarding your PC's data. However, that doesn't mean it's not dangerous, as the trojan is known to steal personal information. With these, the attackers behind the trojan can cause financial loss and lead to identity theft.



 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















