Based on a global survey by Acserve, 50% of SMBs have been targeted by a ransomware attack. The costs are incredibly high: around 30% of victims had to pay over $100,000 in ransom, and 20% were blackmailed for a sum between $1 million and $10 million. That's terrifying.
Businesses should start developing a ransomware disaster recovery plan. Let's scroll down and get ready against ransomware disasters.
In this article
Stage 1: Create a Ransomware Disaster Recovery Team
Knowing who's in charge of what could be extremely helpful in chaotic situations like these.
Typically, a disaster recovery (DR) team includes:
- Crisis management coordinator – When catastrophe hits, your organization should have a sensible crisis management coordinator to initiate the plan and coordinate the recovery.
- Executive manager – A disaster recovery plan is only a dead letter without executives to sign off on it in a critical moment. You need them at the table for approval and oversight.
- Business continuity specialist – This person is in charge of your failsafe options. They should ensure that your everyday operations return to normal as soon as possible.
- Assessment & recovery reps – The entire infrastructure must be in the hands of your IT and security experts. They should handle recovery on networks, servers, storage, and databases.
Each disaster recovery team member should have clearly defined roles and a blueprint for incident response to avoid panic and confusion. It doesn't hurt to name and train backup team members if the original members are not in when the ransomware hits.

Stage 2: Establish Incident Response Protocols
An incident response protocol is a fancy name for a disaster recovery checklist. You might wonder, "How do I know what needs to be done when I have zero experience with ransomware?" That's why you plan based on prediction, probability, and other victims' experiences.

While recovery plays a central part in this, that's not the only thing you must do:
Understanding the attack scope
First, you need to get to know your enemy. What kind of a ransom attack are you dealing with? What is the attack surface, and has it started to spread yet?
Informing the right authorities
Not reporting a crime is illegal in many countries. During the planning phase, you should ask your representatives about your legal responsibilities as a ransomware victim. In many cases, there will be a protocol for informing the authorities that you must follow.
Assembling and communicating
By the time you conduct an initial investigation and inform the police, your disaster recovery team should already be assembled. At this point, you must contact and inform the internal and external stakeholders, from your PR and legal team to your customers and the wider public.
Establishing business continuity
In this phase of the incident response plan, you should be able to lean on your failsafe systems and resume normal business operations without any hindrance. It's critical in industries like health and finance, where even a small standstill can have severe consequences.
Executing a disaster recovery plan
The optimal disaster recovery plan should help you achieve near-zero point-in-time recovery, which means that you can restore your systems to a point before the attack with minimum data loss and downtime.
Stage 3: Record Entire Network Infrastructure
Disaster recovery is impossible if you don't know how everything was before the attack. That's why you need to keep snapshots of your network infrastructure. Recording and monitoring are essential for a successful response, yet many organizations neglect to invest in them.
Records are invaluable for planning your recovery strategy, and in more ways than one. In addition to helping you build a collapsed network infrastructure faster after the attack, they also tell you a lot about your essential and nonessential systems, allowing you to prioritize them.
That way, your disaster recovery specialists will know which parts of the infrastructure to recover first to keep the business running. In case there are any system dependencies, records will show them too. Knowing all of this makes all the difference when you must act fast.
One more thing: recording and monitoring your network infrastructure can help you identify system vulnerabilities that have somehow slipped through the cracks.

Stage 4: Perform Regular Data Backups
Backup is a HUGE factor to consider when creating a ransomware disaster recovery plan. Now, there are three main types of backup – full, incremental, and differential:
| What is it? | Who is it for? | |
| Full backup | During a full backup, the entire directory of files and folders gets copied to another location at once. | small businesses with undemanding amounts of data. |
| Incremental backup | Incremental backup involves backing up only the files and folders that have changed since the last backup. | large organizations with substantial backup needs. |
| Differential backup | Similarly to the incremental backup, it saves only the files and folders that were changed, but since the last FULL backup. | SMBs with a lot of data but insufficient resources to perform regular full backups. |
Organizations considering different backup options have another decision to make – cloud storage or on-premise backup. Generally, getting your backup and storage on the cloud is a more secure, simpler, and cheaper solution, especially with managed services.
More than a backup type or destination, consistency is key for disaster recovery.
A foolproof backup schedule involves saving your data as often as you can. For some organizations, continuous incremental backups make more sense than weekly full backups. That largely depends on how much data you produce, your storage capacity, and your backup system.

Enterprise-grade backup solutions should also include encryption. That puts an additional layer of security around your systems, ensuring that criminals can't read, sell, or otherwise misuse your data even if they get a hold of it. Encryption and backups should go hand in hand.
Stage 5: Adopt Cybersecurity Technologies

Next-generation cybersecurity technologies keep up the pace with ransomware attacks, helping businesses that adopt them on time develop a more systematic approach to data resilience.
For instance, professional data recovery tools like Wondershare Recoverit empower you to quickly restore your data and avoid paying the ransom when attackers break in.
Solutions like these are a vital piece of the disaster recovery puzzle because they are easy to use in a crisis and have high recovery rates. They can recover any file format from any storage device, regardless of the file system. Plus, they don't need a recovery specialist.
Data recovery with Wondershare Recoverit is a simple step-by-step process:
- First, download the app from the official website and install it on the computer where you need to perform recovery.
- Next, select a location to start the recovery. You can choose any hard drive or external device, run a crashed system recovery, or recover data from NAS or Linux.

- The scan will start automatically. Wait for the app to finish the scan or pause it if the file or folder you've been looking for shows up. You can also stop the scan.
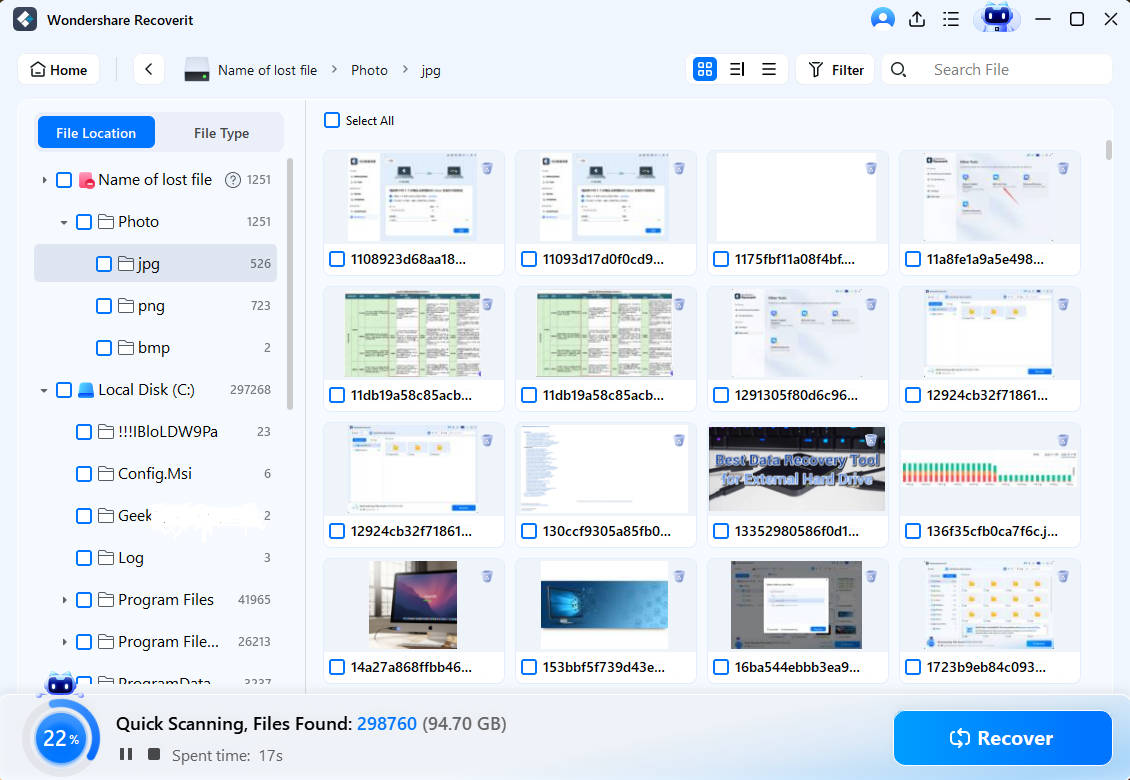
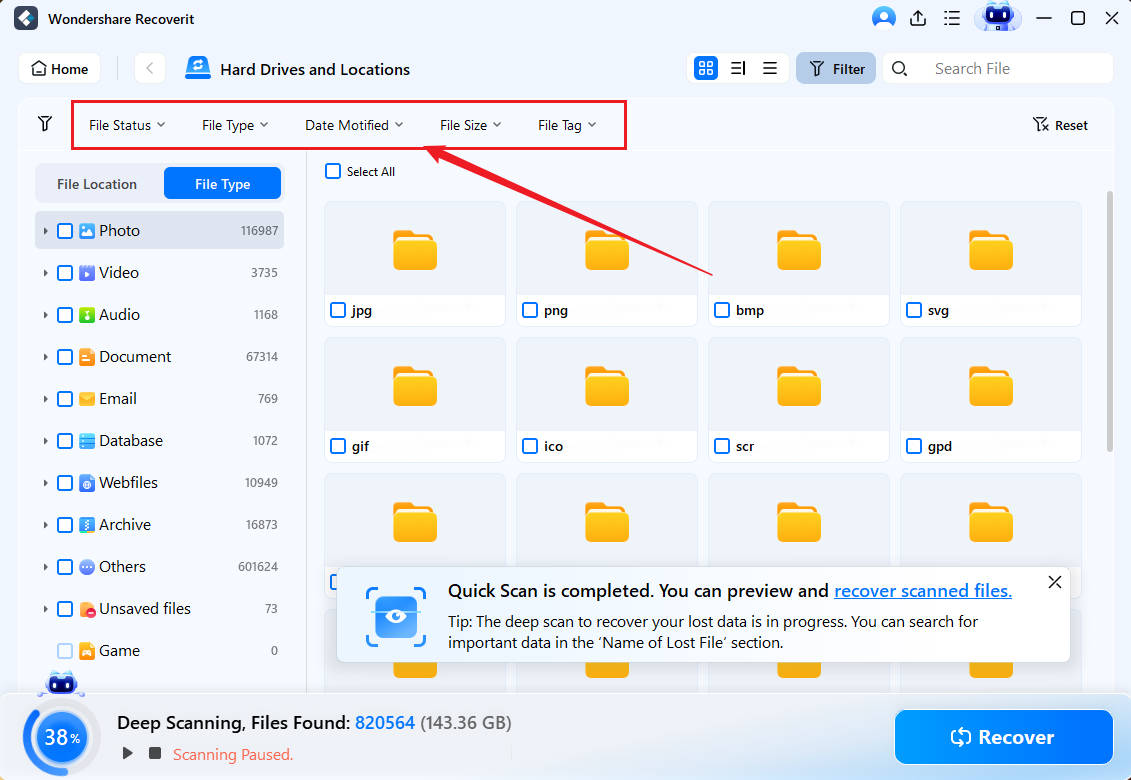
- When the scan is finished, you can filter results by file type, size, and tag or search a specific file or folder by keyword.
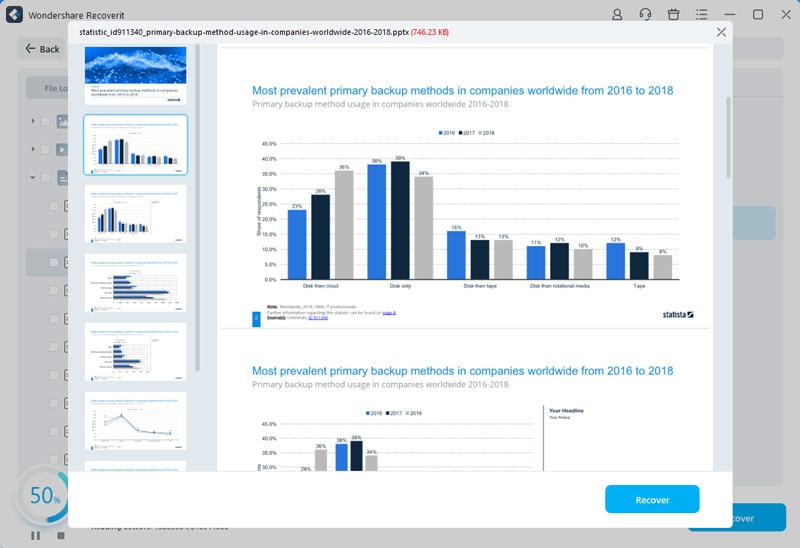
- Double-click on a file to preview it before recovery. If you decide you want to keep it, click the Recover button.
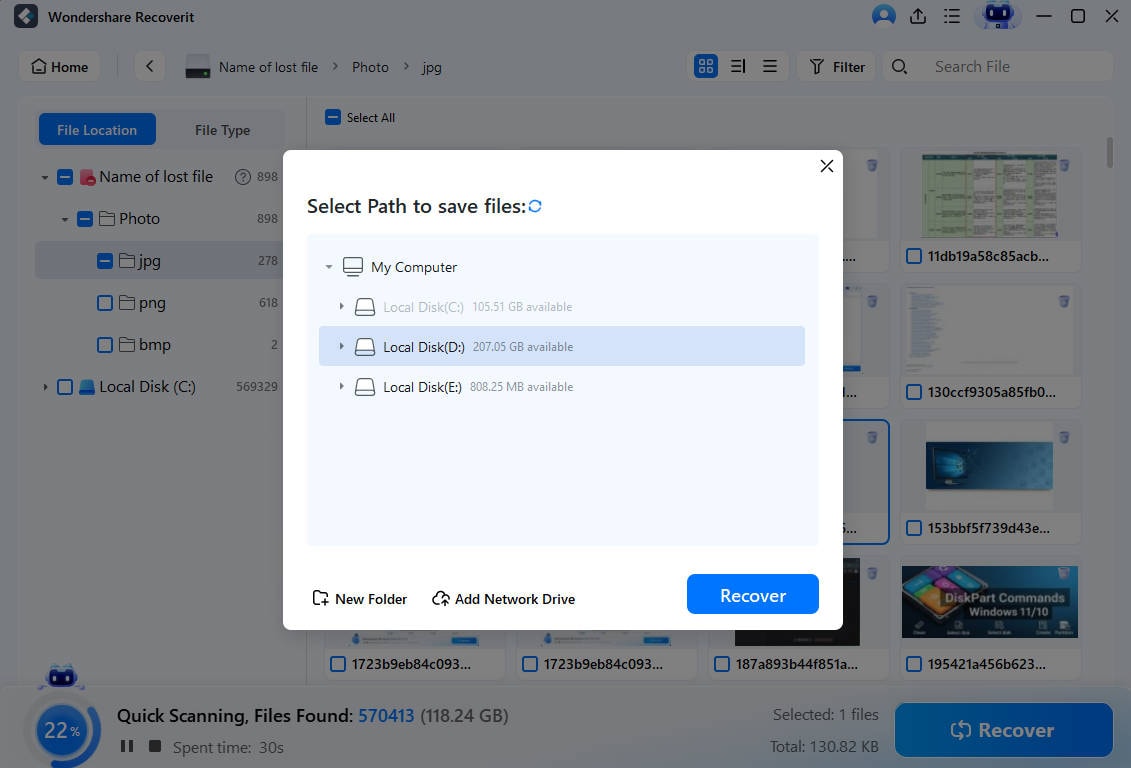
- Choose a safe recovery destination and click Save to retrieve your data.
- If you don't want to do that right now, you can save the scan results for another time.

Other cybersecurity solutions that are now a must-have for businesses are:
- Endpoint Detection and Response (EDR) – EDR systems monitor and analyze endpoint activity to detect and respond to advanced threats, including ransomware attacks.
- Next-Generation Firewall (NGFW) – Firewalls are absolutely essential for cybersecurity. They provide advanced threat protection by inspecting traffic and blocking malicious content.
- Security Information and Event Management (EM) – EM solutions collect and analyze security information across the organization to detect and respond to ransomware attacks.
- Email Security Gateway – Email security gateways detect and deflect email-based threats, including fishing attempts and ransomware payloads sent via attachments and Image names.
Stage 6: Test and Upgrade Ransomware Disaster Recovery Plan
Many organizations across industries learn how to avoid and delete ransomware early on. How come, then, that attacks are on the constant rise?
According to some researchers, this is because many of these organizations fail to test and improve their disaster recovery plans.
Testing is a critical measure against failure, as it shows where your incident response falls short. In addition to that, it teaches preparedness and helps you adopt a vigilant mindset.
Stage 7: Train Employees on Ransomware Threats

Of course, training is critical to a successful ransomware disaster recovery plan. Employees must be continually trained to recognize and avoid ransomware and report their suspicions to the IT security team.
What do you need to teach your employees? There are several habits they need to add to their daily routines to stay protected from common ransomware threats:
- Learning to spot and avoid phishing attempts;
- Recognizing suspicious attachments in emails;
- Using verified and known download sources;
- Creating strong passwords that can't be hacked;
- Using encryption and VPN for sensitive transactions;
- No oversharing of personal information online.
Conclusion
The importance of having a ransomware disaster recovery plan cannot be overstated. If you need help establishing one, find and allocate the right people for the incident response team. They can help you develop and enforce protocols for disaster recovery.
Don't forget that cybersecurity is a continuous process. You must monitor your systems for vulnerabilities and threats and introduce regular backups. Adopt data recovery tools like Recoverit, start training your employees, and test your plan as often as possible.















