Malware or malicious software includes many programs like spyware, rootkits, trojans, viruses, and computer worms. Malware attacks can result in data loss, network disruption, hardware failure, or spyware, or they could simply wait until the point they decide to inflict damage.
There are all kinds of malware threats out there, and in this post, we'll focus on Mirai malware. If you want to learn everything about this threat, including how it works and how to protect yourself from it, you've come to the right place.
Let's see what Mirai malware is before getting into details about it.
In this article
What Is Mirai Malware?
Mirai malware or Mirai botnet is malware focusing on targeting various internet devices like home routers or smart cameras. This malware turns them into a network of "zombies" and controls them. Simply put, your device becomes a bot under the control of Mirai malware, hence the name.
Cybercriminals use Mirai botnet attacks to target computer systems with massive DDoS attacks. Unlike other malware, Mirai focuses only on smart home devices, including refrigerators, baby monitors, assistants, thermostats, routers, etc.
It looks for Linux OS IoT devices and exploits the vulnerabilities of these small gadgets. After getting access to them, this malware Image names them together and creates a network of controlled devices—a botnet.

Origin and Evolution of Mirai Malware
The beginning of the Mirai malware goes back to Paras Jha and Josiah White, two college students. They wrote the source code for the Mirai botnet in 2016. The pair tried to extort their university with DDoS attacks.
After that, the duo started targeting servers hosting popular games and security companies in charge of protecting those servers from attacks. Paras Jha released the code online in 2016 to spread the Mirai virus and allow other hackers to use it.
Since then, hundreds of cybercriminals have modified and replicated it. The Mirai botnet changed its forms multiple times and even shut down a significant portion of the internet in the US. Several variants have grown out of Mirai, including PureMasuta, Masuta, Satori, and Okiru.
How Is Mirai Malware Different From Traditional Malware?
- It targets IoT devices
- Mirai looks to turn infected devices into botnet
- Spread by exploiting weak credentials on IoT devices
- The ultimate goal is to launch DDoS attacks
- Has an open-source code.
The first significant difference of Mirai malware is that it focuses not on infecting devices with malware for the sake of it but on trying to get something out of it. What's genuinely impressive about Mirai botnet attacks is that most IoT device users aren't even aware of the infection and unwittingly perform unauthorized actions online.
At the same time, traditional malware focuses on computers, while Mirai works only with IoT devices. Mirai relies on devices that have software and carry sensors to communicate with network systems and other devices. That's how it finds its targets and spreads quickly to create a botnet.
After infecting a device, Mirai will also purge any existing malware to ensure that the device belongs to the botnet, which can be used for flooding networks and servers. Its ultimate goal is to launch DDoS attacks.
Different from others, Mirai Mailware's code was made publicly available so hackers could adjust and improve the Mirai malware for various motivations, including financial gain, political activism, information theft, etc.

How a Mirai Botnet Attack Works
To understand how Mirai botnet attacks work, you must understand the network of internet-enabled devices in our homes—IoT (Internet of Things). IoT gadgets are prevalent in smart homes but have specific weaknesses that Mirai botnet attacks can exploit.
Mirai malware first scans those devices' IP addresses to identify those using the Linux OS (ARC). Mirai gains access to the network by using the default password and username combinations on targeted devices using this operating system.
If users haven't changed the default credentials, Mirai instantly gains access and spreads malware. As the number of infected devices grows, hackers can use this botnet to target various servers or websites by sending out countless requests and traffic. The service will become unavailable to users, and the hackers will request ransom payments before they quit the DDoS attack.

Devices Targeted by Mirai Malware
Mirai malware targets most smart devices operating within the IoT infrastructure. However, the primary targets are cameras and home routers. Your home network, which controls intelligent vehicles, appliances, intercoms, and robot vacuums, is a backdoor for Mirai malware.

However, some parts of the IoT ecosystem are unreachable to Mirai, but that is mainly because the creators of this malware programmed it to ignore specific IP addresses. For example, they designed the malware to avoid government devices, including those the US Department of Defense owns.
Why Is Mirai So Dangerous?
First of all, even though the authorities apprehended the creators of this malware, they released the source code publicly. In other words, there are still many variations of the same malware.
This malware is dangerous because it uses DDoS attacks that are difficult to stop and can cause devastating commercial effects. Many businesses have paid huge ransoms because of DDoS attacks since they could not prevent them. IoT botnets can also harvest personal data, spread spam, and hold devices hostage with ransomware.
How to Detect and Remove Mirai Botnet Attack
The fact that Mirai botnet attacks are known and that the code is open-source is helpful. Most importantly, there are ways organizations and individuals can detect these attacks on time and protect themselves.
Detect Mirai Attacks
The first way to detect Mirai attacks is to monitor network traffic, including unusual patterns like sudden bursts. On the other hand, Mirai botnet attacks also try to establish as many connections as possible to multiple IP addresses.
Users should also check device behavior and look for abnormal resource consumption or frequent failed login attempts. Reviewing event logs on network devices, firewalls, and routers is critical to spot unusual patterns or activities.
One of the best systems for detecting Mirai attacks is network anomaly detection systems that can recognize unusual behavior and raise automated alerts. IDP (Intrusion Detection and Prevention) systems are also excellent for monitoring the network system activities for known Mirai behaviors or signatures.
Segment the Network
Network segmentation means dividing your computer network into smaller networks. That is a valuable mechanism for protecting yourself against Mirai malware and similar attacks.
Since the primary target of Mirai attacks is IoT devices, you can segment the network and separate all devices from your system's critical parts.
Network segmentation prevents the malware from spreading over your network, compromising only the single segment that was the initial point of attack. Separating critical systems into smaller networks can help prevent DDoS attacks on those systems and continue your operations.
Install Antimalware Software
Antimalware software is a vital security tool to protect systems, including IoT units, against malware. Even though antivirus solutions don't exist specifically for IoT devices, they can recognize signatures and patterns associated with malware and quarantine the threat. They also detect unusual behavior of processes and programs related to Mirai malware.
At the same time, these tools use heuristic analysis to detect new malware variants, even if the signatures are unknown. With real-time protection, antivirus software scans currently running processes and files, meaning if Mirai malware tries to execute an action, the antivirus can block it.
Firewalls are another crucial protection against malware as they block outgoing and incoming traffic. Antimalware tools work with firewalls to set up the best defenses.
Take the time to find reliable tools, primarily those offering excellent antimalware protection and showcasing promising numbers regarding defending against these attacks.

Reset Devices to Factory Settings
Resetting your IoT devices to the factory settings can differ depending on the device and manufacturer. What's important is that resetting to factory settings will completely remove all the malware and allow you to set up more robust security measures and credentials that could prevent similar attacks in the future.
Some devices can be reset to factory settings with a simple power cycle and a reset, while some have their own interfaces you can use to do this. Refer to the manual and find the safest option to do this successfully.
How to Realize Post-attack Recovery and Further Prevention
Post-attack recovery and prevention is a combination of steps you must take toward restoring systems, minimizing damages, and setting in place different measures to prevent future attacks.
Clean Malware and Recover Data
Once you successfully identify and isolate infected devices, clean them individually. One of the best approaches is returning them to their default state and using backups to restore your data.
If you can't recover data because you haven't backed it up, consider using a professional data recovery tool like Wondershare Recoverit to recover deleted or lost data in various scenarios.
Here's how:
- After starting Wondershare Recoverit, click Hard Drives and Locations and then the drive you lost your data on.
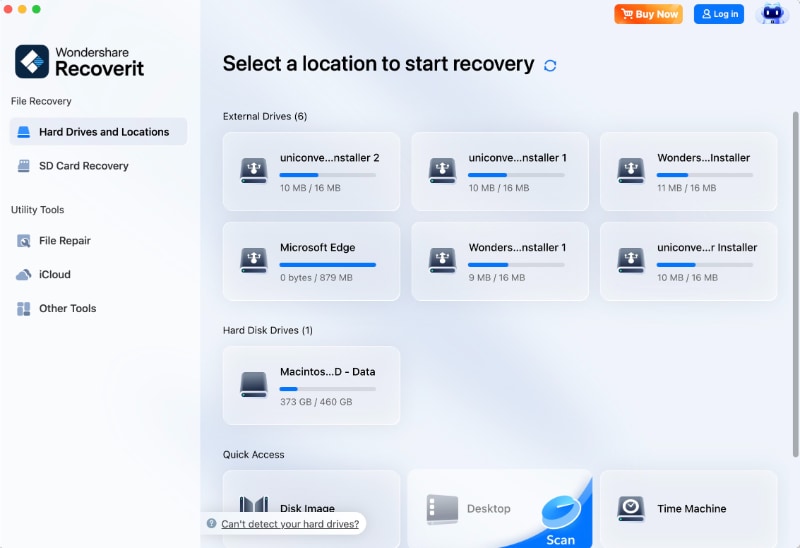
- The program will start scanning automatically, and you can track progress in the bottom left corner.

- Click Preview to check which files have been located. click Recover if you've found the right file(s).
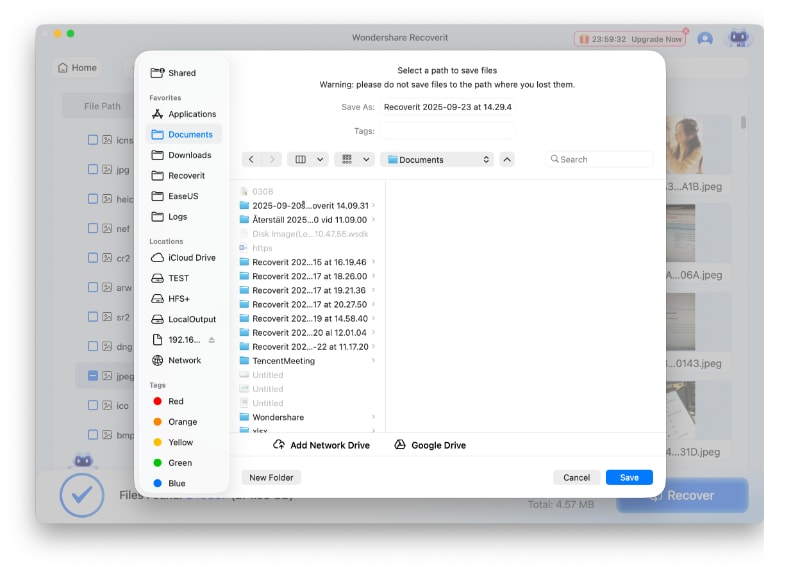
- Choose the patch and click Save.
Restrict Access
Securing the devices and network is crucial for protecting yourself against malware. Start by enabling and configuring firewall protection on your router and devices. Firewalls can control and monitor all traffic and prevent any potential threats.
It's a good idea to add access controls that clearly outline the conditions and regulate who can access network resources and devices.
Install All Patches and Updates
Once you clean your network of all the infections and restore your device, install all updates from the official device manufacturers. All operating systems, software, and firmware should be running with the latest updates to patch any vulnerabilities in your system and prevent future intrusions.
Updates also include various new security features that improve the overall security of IoT devices, including access control systems, authentication mechanisms, encryption, etc. Additionally, they address vulnerabilities that affect stability to fix firmware bugs.
Users should also update the operating systems of their devices and any apps they might use.

Change All Your Passwords and Credentials
Change all the credentials and passwords on all your devices, including those that the malware hasn't infected. Change passwords for your Wi-Fi networks, interfaces, logins, apps, services, profiles, etc. Ensure your passwords are complex by:
- Using numbers
- Including symbols
- Using uppercase and lowercase characters
- Creating long passwords
- Regularly updating your passwords
- Avoiding common phrases or words
- Implementing multi-factor authentication features
- Limiting login attempts
- Storing passwords with encryption
- Carefully managing passwords and practicing safe habits
- Using password managers

Regularly Back Up Data
Create a comprehensive backup schedule for all your devices. You can only ensure 100% safety against malware attacks with the help of a backup strategy. That way, you can quickly restore it after returning your devices to their default settings.
Conclusion
Mirai botnet attacks are dangerous, but they're nothing new. In other words, if you're proactive with prevention strategies and set the correct recovery measures, you can drastically reduce the chances of Mirai infecting your devices.
Even if Mirai malware infects your system, you can quickly mitigate the damages and restore it to its regular state by monitoring traffic, segmenting your network, using antimalware tools, and resetting your devices to factory settings. At the same time, take all the post-attack recommendations seriously to protect your system against future attacks.















