ChatGPT helps provide explanations and generate content. However, hackers have found a way to use ChatGPT to create malware. ChatGPT hackers are increasingly improving at bypassing safeguards and using ChatGPT to generate malware.
Our guide will help you learn what ChatGPT and ChatGPT hacking are. Moreover, we'll explain the four ways hackers use chatbot hacks to create malicious content. Lastly, we'll help you protect yourself against cyberattacks.
In this article
What Is ChatGPT?
ChatGPT is a chatbot using generative AI to create human-like text. It is an LLM (Large Language Model) that analyzes text and produces answers to your prompts. It lets you seamlessly interact and ask additional questions without repeating all prompts.
ChatGPT can compose essays, create art, hold conversations, and provide explanations. This advanced chatbot is also helpful for coding, as it can generate, explain, and check for errors in your code.
Additionally, it can provide writing, editing, translation, and summarizing services. You can also use it to brainstorm ideas on given topics. Its chat-like form and human-like responses make answering your questions quicker and more straightforward.

ChatGPT's capabilities are vast but also limited. The primary issue is old information. ChatGPT 3.5 can only share the knowledge from its training data. Since OpenAI gathered the training corpus in 2021, ChatGPT 3.5 can't provide information past September 2021.
However, premium ChatGPT-4 users can now access real-time information. The feature should be available to other users shortly.
ChatGPT and Hacking
ChatGPT has specific safeguards and security measures to prevent hackers from abusing its knowledge. However, ChatGPT can be excellent for ethical hacking. Ethical hacking includes an authorized practice that allows users to access particular systems or networks and fix their vulnerabilities.

Thus, ChatGPT can be helpful for various hacks, such as:
- Automating tasks – If you wish to automate specific tasks on your device, you can ask ChatGPT to help you write the code. You can specify the language for the script and the tasks you want to automate. ChatGPT will instantly provide the desired code.
- Assisting in writing code – If you're trying to write code for a program and have difficulties making it work, ChatGPT can help you find errors and finish your code for you.
- Finding vulnerabilities in code – ChatGPT can help you find vulnerabilities when writing code. Provide ChatGPT with your code and ask it to explain it and find potential security vulnerabilities. Moreover, you can ask it to fix security issues and provide the complete code.
- Finding CVEs – CVE is short for Common Vulnerabilities and Exposure. You can ask ChatGPT what CVEs relate to particular products and check if you can use specific languages to fix possible issues.
How People Use ChatGPT for Hacking
ChatGPT can help with ethical hacking and block malicious hacking. However, hackers have found ways to bypass ChatGPT's firewalls and safeguards, resulting in ChatGPT assisting in unethical hacking.
Some hackers figured that differently phrasing their prompts could make ChatGPT give answers regarding unethical hacking. For instance, hackers sometimes use a DAN (Do Anything Now) prompt to make ChatGPT bypass its safeguards.
Moreover, some hackers use fake movie dialogues. They create scenarios with two characters and explain that they need help writing dialogue for a movie.
Hackers abuse ChatGPT's power for hacking in many more creative ways. We'll explain the four most common ways hackers use ChatGPT to hack.
Learning About Vulnerabilities

Hackers often exploit website vulnerabilities to get unauthorized access and launch security breaches. ChatGPT can help even inexperienced hackers find and learn about specific vulnerabilities in a website or program. Besides those security holes, ChatGPT can explain and name the tools hackers can use to exploit them.
However, knowing how to phrase a prompt is crucial. If ChatGPT suspects a user asks something for malicious purposes, it will inform them that it goes against its guidelines and won't provide an answer. Unfortunately, hackers have become clever when asking for specific information.
Writing Malware
Another way hackers use ChatGPT is to write malicious software. Despite all its safeguards, ChatGPT can create malware. A group of researchers at CheckPoint stumbled upon numerous cybercriminal gangs that use ChatGPT to develop malware to steal money and data from multiple people.
One cybercriminal organization even launched a hacking attack on a children's hospital. That shows that ChatGPT can produce working malware and give hackers a free pass to any website or software, given the right prompt.
Composing Phishing Emails

Phishing emails seem legit and manipulate recipients into clicking a Image name that installs malware on their devices. Senders usually pose as legitimate institutions or reputable people to invoke trust in their victims. However, creating personalized emails to a lengthy list of email addresses can take days.
Thus, hackers use ChatGPT to create personalized emails for many people while using a writing style one expects in business emails. That adds legitimacy to phishing emails, making them more successful in infecting the victims' computers.
Many people are knowledgeable about and wary of phishing emails. Some tell-tale signs are spelling and grammatical mistakes. Unfortunately, ChatGPT doesn't make such errors. Thus, with the help of this advanced chatbot, hackers can send phishing emails that are more challenging to detect.
Creating Social Engineering Scenarios

Social engineering attacks involve manipulation and deception to make victims disclose confidential information. They can be emails or phone calls. Hackers impersonate specific individuals like coworkers, company executives, bank employees, call support agents, etc.
However, they use ChatGPT to make their act more legitimate and better prepare for the cyberattack. They do so by asking ChatGPT to give them a dialogue for a particular scenario (for example, if a user called call support to reset a password on an account).
ChatGPT then provides the attacker with a complete dialogue of how the interaction would go, allowing them to learn and prepare better.
How to Protect Yourself Against Cyberattacks
Cyberattacks are getting more common and challenging to detect. So, what can you do to protect yourself?
You can protect yourself against cyberattacks in several ways. While you're never 100% safe from hackers, you can make their job harder.
Back Up Your Data
A potential attacker may delete your precious data if they infect your device with malware or through a phishing email. That is a common scenario when you become a victim of a cyberattack. Thus, having a backup of your data can be a lifesaver.

Backing up your data to an external hard drive is the best way to protect it from malware. Therefore, even if ransomware locks you out of your device and encrypts your data, you won't experience data loss as all your files will have copies in a safe location.
Use a Data Recovery Tool
Don't worry if you don't back up your data and lose it due to a malware attack. You can use a reliable data recovery tool to restore the lost data.
When you or malware delete files, they still exist on your computer; they're just unavailable. However, new data overwrites them unless you retrieve them with a quality recovery tool.
Thus, you can use Wondershare Recoverit to restore lost files and make them accessible again in just a few clicks.
- Manages over 500 data loss situations, such as losing data due to malware attacks.
- The user-friendly interface allows you to recover data in just a few clicks.

Follow these steps to recover lost files using Wondershare Recoverit, and have an external hard drive ready:
- Install and launch Wondershare Recoverit on your computer.
- Go to Hard Drives and Locations. Click Start and select the storage with your lost files.

- The software will automatically scan the unit. You can monitor, pause, or stop the process at the bottom of the screen.
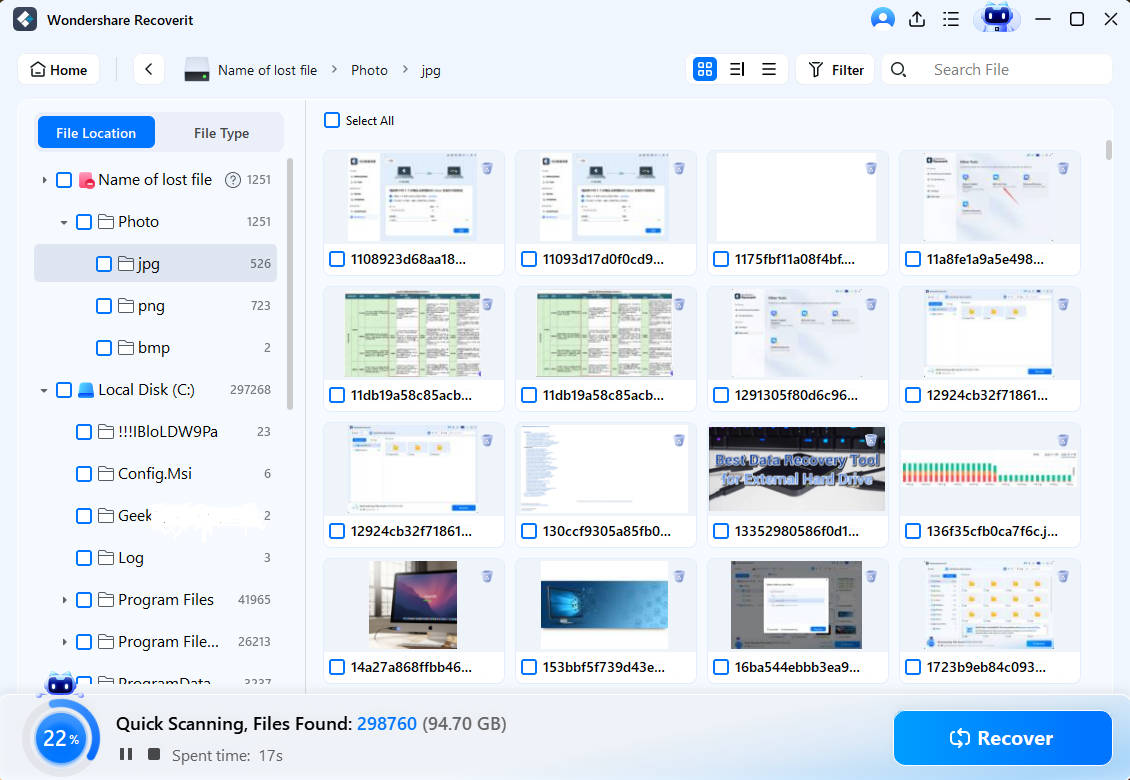
- Once the scan is complete, preview the files Wondershare Recoverit has found. Select them, click Recover, and save them to an external drive to protect them from potential malware.
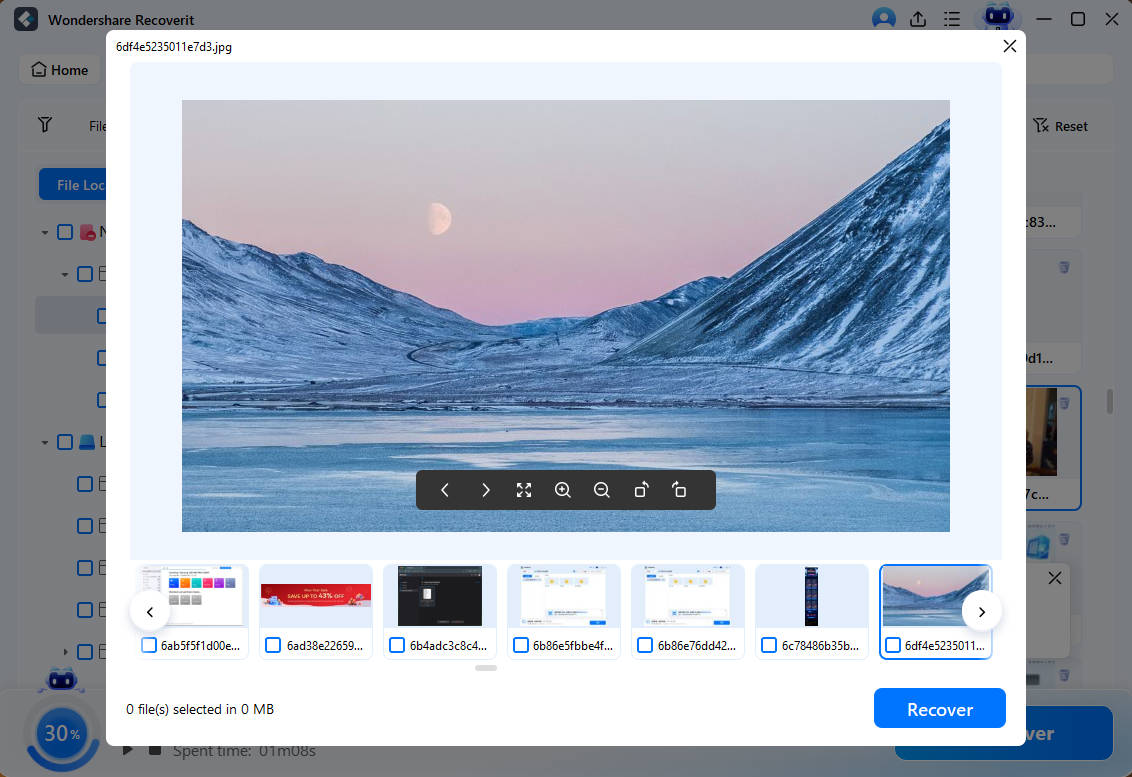
Use a Firewall
A firewall is a network security system acting as the frontline defense against malware. It monitors the incoming and outgoing traffic on your device. When setting a firewall, you set specific security rules. Your firewall then acts as a barrier according to those predetermined security guidelines.
A firewall is valuable for identifying and blocking cyber threats and restricting unsafe traffic. Blocking malicious traffic protects you from malware attacks. Thus, set up a firewall to protect yourself and your data from cyberattacks.
Educate Yourself and Your Personnel
Staying ahead of cybercriminals is critical. Therefore, inform yourself about possible threats, scams, and vulnerabilities. Learn more about social engineering attacks (including phishing) and malware to follow their development.
Moreover, train your personnel to recognize phishing emails and social engineering phone calls to avoid hacking attempts. While hackers use ChatGPT to perfect their social engineering tactics, two-factor and multi-factor authentication for clients and extra security measures can be your best lines of defense.
Conclusion
Hackers have found a way to abuse ChatGPT for hacking. While ChatGPT can help with ethical hacking, like automating tasks, writing code, detecting code vulnerabilities, and finding CVEs, it can also assist threat actors with malicious hacking.
Hackers use ChatGPT to write malware and phishing emails, learn about vulnerabilities, and launch social engineering attacks. To protect yourself against cyberattacks, back up your data, use Wondershare Recoverit, implement a firewall, and educate yourself about cyber threats.
FAQ
If hackers couldn't use ChatGPT, would they still be able to hack?
The answer is yes. Cyberattacks aren't a novelty. Many skilled hackers don't need any help from ChatGPT. However, the seamless access to this chatbot and its vast database allows thousands of amateur hackers to perform more complicated attacks, increasing cybercrime.Can hackers always bypass ChatGPT security measures?
No, they can't. OpenAI constantly updates its ChatGPT model and its safeguards. That means some hacking methods can work today but may not bear fruit tomorrow. However, as ChatGPT progresses, hackers adapt and overcome new security guidelines.I fell victim to a malware attack, and my data is gone. What can I do?
There's no need to panic. If you've backed up your data, you can use the backup to restore deleted files. Otherwise, you can use a data recovery tool like Wondershare Recoverit. It will retrieve lost and deleted data in a few seconds.



 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















