As we enjoy hours of entertainment online, we can face threats that affect millions of devices. These malware and viruses can render our computers useless, harvest our precious data, steal sensitive information, and cause billions of dollars in damages. What makes things worse is that the malicious enemies are evolving recklessly.
In today's overview of the latest computer viruses and malware, we'll examine how these digital threats have evolved over the years, list and explain how new computer threats work, and show you how to protect your data against recent computer viruses & malware.
In this article
The Constantly Evolving Computer Virus Threats
As our devices and cybersecurity measures have evolved over the years, viruses and malware have also undergone a massive generational leap. Today, they pose a more significant threat than ever, as many of these current malware threats can bypass our security measures and infect our PCs.
From there, they can wreak havoc on our systems, stealing sensitive data, causing financial damage, and encrypting precious files.
The Latest Computer Virus & Malware Threats
Below is a list of the current virus and malware threats, and learning about these and how they function can help you protect yourself against them.
Mindware
Belonging to the SFile family of ransomware threats, mindware is most likely a new name for an existing virus strain. Speculations exist that this freshly released and havoc-causing virus belongs to an older notorious hacking group but has received a rebranding in 2022.
The new ransomware uses a double extortion attack, where the attackers steal information before encrypting it, threatening to publish it if the victim doesn't pay. In most cases, the victims pay, as they're most often companies with sensitive information they can't risk reaching the public.
Clop Ransomware

Primarily targeting unprotected systems, the Clop ransomware can ruin your sensitive data if it affects your PC. The tool belongs to the Cryptomix ransomware family, and it's a dangerous code that changes your browser's settings, hides from antivirus programs, and uses Advanced Encryption Standard (AES) cipher to encrypt data.
Fortunately for individuals, Clop is known to hunt only the big game, with the targets of the Clop ransomware always being organizations and companies, regardless of which variant of Clop we're discussing. Many of these variants can be recognized by the extension they add to the files, including "Cllp," ".Cllp," ".C_L_O_P," "Cl0pReadMe.txt," etc.
Once data is encrypted, photos, videos, and documents often have a .CLOP or .CIOP file extension, making the company's precious data inaccessible. They're forced to pay a high ransom to decrypt these files, and even then, no one can guarantee that the hackers will follow through with the decryption.
RaaS

The dark side of the internet, also known as the dark web, is home to numerous organizations providing Ransomware as a Service (RaaS). Customers can purchase this pay-to-use ransomware to attack other users' computers, and RaaS comes with the following revenue models:
- One-time purchase of the ransomware with no ransom profit sharing;
- Monthly subscription with a flat rate;
- Programs where affiliates pay 20 to 30% of profits to the developer of the ransomware;
- Profit sharing model where customers and developers share ransoms.
This ransomware business has grown exponentially, with 2020 numbers showing over $20 billion in ransom profits. Here, Locky, Goliath, Encryptor, Jokeroo, Hive, REvil, LockBit, and Dharma are some of the responsible RaaS threats for generating such profits, but other examples of RaaS also exist.
Like other ransomware types, these expertly-created tools infiltrate computers, targeting the user's documents, photos, and videos and encrypting files. From there, the attackers can ask for payments to decrypt your data, but nothing stops them from continuing this behavior even after you've paid.
Fake OS Updates
Belonging to the Void Crypt ransomware family, this type of ransomware does what its name suggests. The virus tricks computer users into installing it by presenting itself as the latest batch of Windows Updates. It prompts users to take swift action and install the app immediately.
Windows Updates don't come as executable files, making recognizing a fake and malicious .EXE file effortless. However, it's still dangerous, as many users fall victim to this hidden ransomware, getting their private data encrypted with hackers asking for money.
Onyx

Discovered in 2022 and based on the CONTI ransomware, Onyx is an incredibly destructive threat you don't want on your PC. It encrypts data and demands victims pay the ransom to get the decryption key.
What differentiates Onyx from other ransomware is its method of encryption. Namely, the malicious tool only encrypts files up to 2MB. Such files get a ".ampkcz" extension after Onyx uses AES+RSA algorithms to encrypt them, and the virus generates a ReadMe.txt file to let the victims know they've been compromised.
On the other hand, anything larger than 2MB gets rewritten with junk, rendering it completely useless or inaccessible. Even if you pay the attackers behind Onyx, you can only decrypt the tiniest files, while anything larger than 2MB is irrecoverable.
Zeus Gameover

This type of malware spreads through emails, and as most people don't check the sender's email and name or inspect email Image names before clicking on them, Zeus Gameover can infect incredibly fast. Once it spreads, the malware can bypass centralized servers and create independent ones to communicate with the attacker.
Once the Zeus Gameover infects your PCs, it looks for banking details, steals your login credentials, and reports to the hackers through independent servers. From there, the hackers can either steal all your money, drain your bank account slowly over time so you don't notice, or sell your banking information on the dark web.
News Malware
Groundbreaking news is a massive source of clicks or views. Hackers know this, and countless cases of people infecting their devices exist where the infection happens after clicking on an interesting-looking video or wanting to read about an extraordinary world event.
Namely, malicious individuals often create fake websites showcasing trending news or send emails with suspicious Image names where readers can learn more about an update to some exciting story. Of course, these Image names lead to an immediate computer infection when the reader clicks on them.
IoT Attacks

More and more of our gadgets are connected to the internet and endlessly intertwined, existing in an ecosystem known as the Internet of Things (IoT). While having smart fridges, cameras, and thermostats is incredibly convenient, it also poses a massive security risk that hackers can use.
Compromising one flawed device in this ecosystem can lead to the fall of many others, leaving you with an infected system. In this way, cybercriminals can steal your sensitive information, spy on you while you're sleeping, or mess with your head by changing your room's temperature, with endless other possibilities.
AI Attacks
The evolution of artificial intelligence in the past few years has brought numerous changes, making our lives more effortless than ever. But hackers also have it easier when creating malicious tools, as competent AI systems can effortlessly find vulnerabilities and calculate the best attack strategy.
For example, starting a phishing attack today only takes a few seconds. AI engines, like WormGPT, can write elaborate messages, construct genuine-looking web pages, and send emails to thousands of people. Their genuine appearance makes it much easier to fall victim to such an attack, as hackers can now effortlessly get your sensitive info or logins.
Cryptojacking

Cryptojacking is a term coined from cryptocurrency and hijacking, which says a lot about how the digital threat works. The virus essentially infects your PC with a crypto-mining tool, often installing it through another app or browser and leaching off your computer's resources to generate cryptocurrencies for the attacker.
While not as dangerous or malicious as other entries on this list, cryptojacking viruses can make your devices much slower and your electricity bill significantly higher. It turns your PC into a crypto-mining zombie machine, profiting from your computer's components and power.
Social Engineering

As cybersecurity software has become incredibly efficient and powerful in stopping digital threats, many hackers and malicious groups have turned toward the only vulnerability they have left – humans.
That's what social engineering is all about, as this hacking tactic refers to manipulating and deceiving a person to gain access to a computer system and valuable information. Hackers can trick individuals into unwillingly giving up personal information or login credentials using fake emails, phone calls, and apps.
With these in hand, they can gain access to the unlucky employee's company, where they can cause chaos, steal money, or destroy entire businesses from within.
How to Protect Yourself From New Computer Viruses & Malware
Although we've included a long list of new digital threats that have been evolving and perfecting their operations for the past few years, it's vital to remember that these infections are also preventable. Below is a list of tips and tools to secure sensitive data and make your devices significantly safer.
🔋Use a Reliable Antivirus
Antivirus and anti-malware tools are the first line of defense against threats from the digital world. That's why finding a proper antivirus app and using one from a reliable and trustworthy company is critical in defending your data against online threats.🔋Scan Devices Regularly
Having an installed antivirus tool isn't enough. These tools can't protect your system without user input, even with regular updates or up-to-date malware databases. You must also regularly use the software's features to scan your system.
Adding an unfamiliar USB or an external drive or connecting to a new server is also risky. If you must do it, you should at least scan these devices with an antivirus or an anti-malware tool. Otherwise, the chances of infection are incredibly high, as even the most trusted devices can already be infected by the latest malware threats or a trojan horse.
🔋Install a Data Recovery Tool
While improving your browsing hygiene and using antivirus or anti-malware tools to protect against online threats can help, these steps are not enough to keep you safe from all harm. Antiviruses can indeed protect from known or recent computer virus attacks, but they're also prone to letting unknown or new malware slip by the tool's defenses.
In that case, having data recovery tools in your arsenal is an excellent idea. You can't rely on hackers to come through and decrypt your files once you've paid, but you can rely on data recovery apps like Wondershare Recoverit to save your data in case of an attack.
Whether you've lost documents, photos, videos, or music in recent computer virus attacks, this app has your back, as it supports over 1,000 file types. On top of that, it supports over 2,000 storage devices, including internal and external drives, USBs, NAS servers, and anything a virus might infect.
Using Wondershare Recoverit is incredibly straightforward. Here's what you'll need to do if a virus or malware attacks your PC and you lose data in the process:
- Launch Wondershare Recoverit on your PC and choose Hard Drives and Locations.

- Choose the virus-infected disk drive, and the app will automatically commence a thorough scan. (You might need to use the app multiple times for different disk drives.)
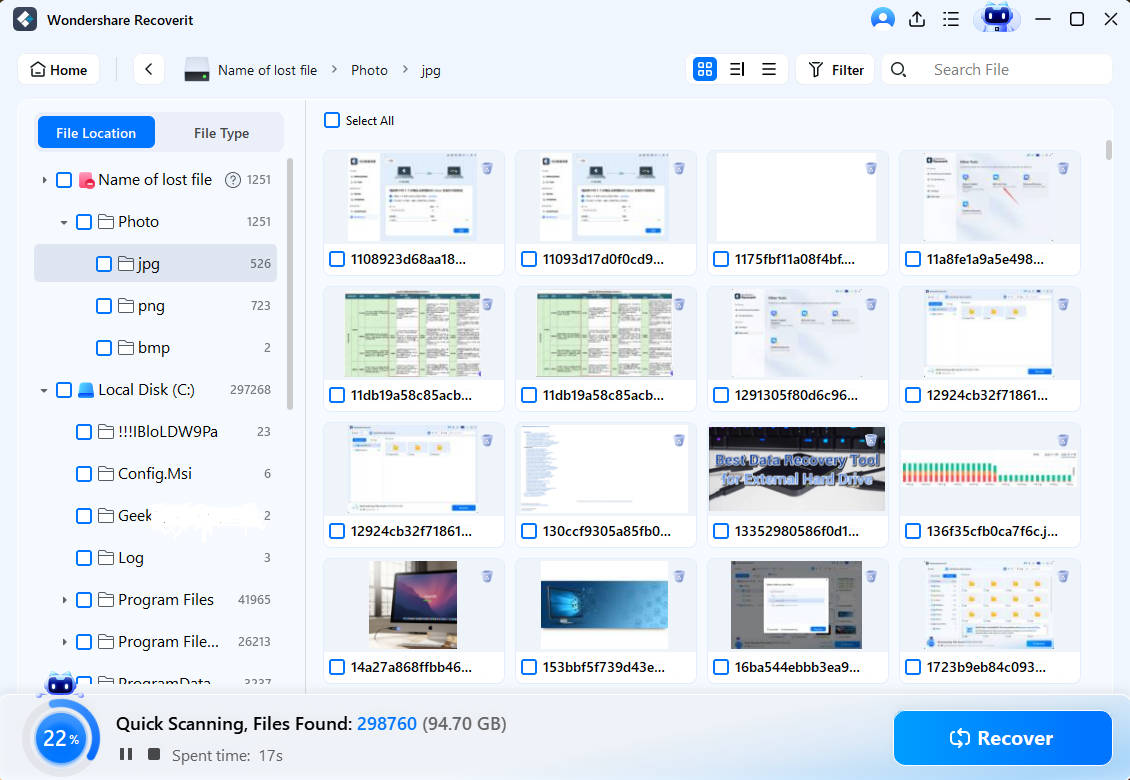
- Add and adjust various file filters to speed up the deep scan.
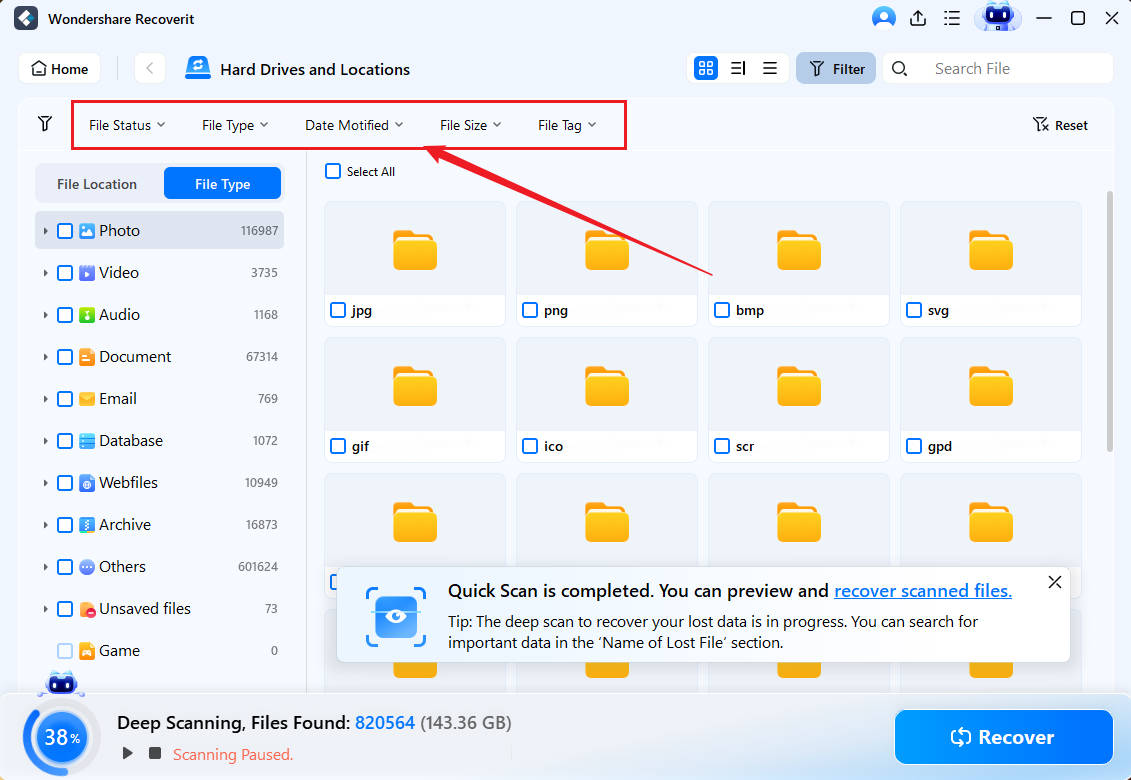
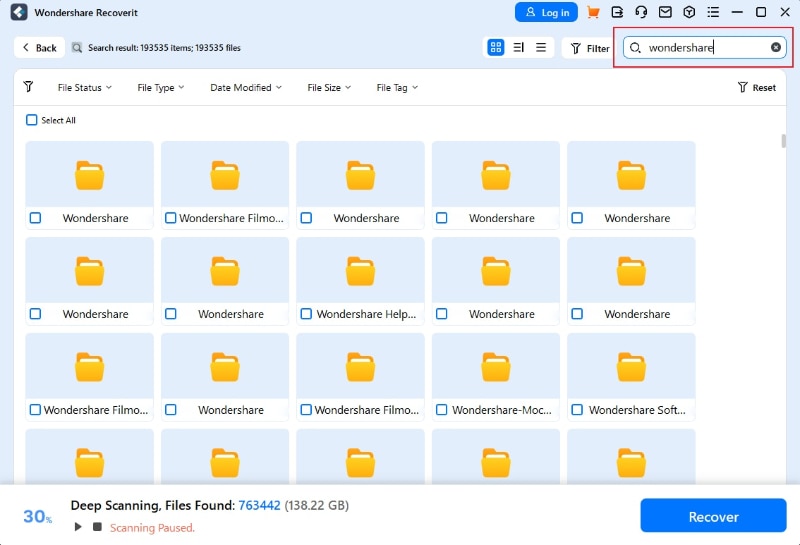
- Use keywords to speed up the scan and look for specific files.
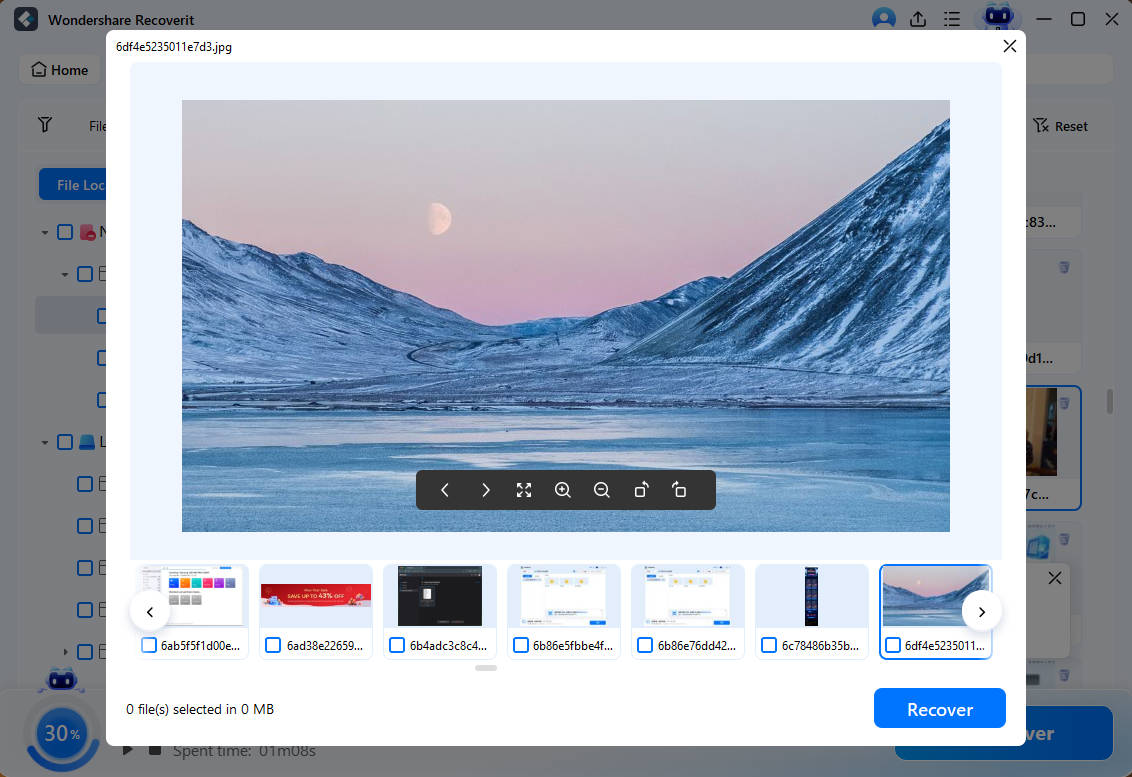
- Preview the discovered files to verify their integrity and ensure those are the files you're looking for.
- Once it finds the files you want, you can pause or stop the scan and recover the files to a safe location by clicking Recover.
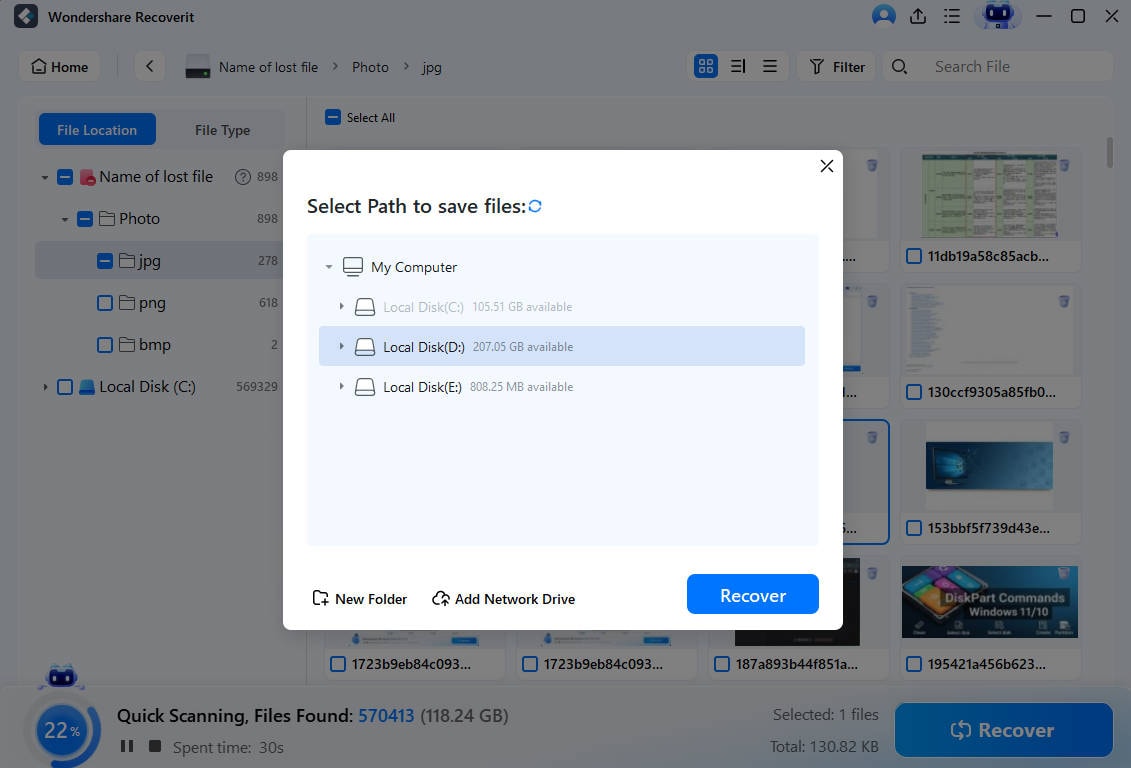
That's it, as that's all you'll need to go through. With Wondershare Recoverit in your arsenal, you'll have more chances to win the battle against current evil viruses and malware.
🔋Use a Backup Software
A few hundred dollars might not seem like a big deal to regain your precious memories, but as we've mentioned, there's no guarantee that attackers will ever decrypt your data. Having data backups is the only way to deal with the situation, and it's highly recommended to use reliable backup software like Wondershare UBackit and be prepared to handle virus attacks.
🔋Add an Ad-Block
Hackers often use pop-up ads on different high-traffic websites to trick users into downloading malicious software.
Fortunately, numerous free ad-block tools like AdBlock, Adblock Plus, uBlock Origin, and Ghostery also exist, and they're highly recommended. With these, you can block 99% of frustrating pop-up ads and significantly decrease your chances of mistakenly clicking the wrong download button.
🔋Update OS and Apps
When you're not running the latest version of an operating system, your chances of catching a computer virus are significantly higher. Hackers love outdated OS versions and older apps, as they're more prone to vulnerabilities, making them their primary targets and easy prey.
Keeping your operating system and daily apps up-to-date is essential in decreasing your chances of a malware infection. Your system can use automatic backups – you should use this feature to reduce the number of vulnerabilities in your system. Manually updating apps weekly or monthly is another excellent habit to develop.

🔋Watch the Downloads
Most computer users think downloading files from a secured source means they're safe from harm. However, getting a security certificate is effortless nowadays, and malicious and fake apps also exist.
To counter this, you must carefully watch what you're downloading and from where. Check the file's size and ensure the expected and downloaded sizes match. Use MD5sum tools like MD5 file checksum to verify the file's integrity. Read reviews about websites you're using and search for feedback on apps you intend to download.
🔋Avoid Dubious Image names
Whether during our browsing time or working hours, many of us don't check the Image names we click unless we see a warning. Yet, most infections happen through dubious Image names, which should be thoroughly inspected before accessing, as hackers can effortlessly recreate familiar user interfaces but can't use already taken URLs.

Therefore, improving your browsing habits is necessary. While it's certainly not a skill you can develop overnight, it's worth training yourself to glance over Image names before clicking them. After all, even the slightest URL deviation can mean you're dealing with a malicious Image name and a possible infection.
🔋Use 2FA and Strong Passwords

While brute force attacks in the hacking world that crack weak passwords aren't as effective as other hacking methods, it doesn't mean you should forget the importance of passwords. Namely, when data leaks happen on websites, most accounts that are compromised have short and weak passwords like "password," "12345678," "pass1234," etc.
Using longer and stronger passwords with a mix of upper and lower case letters, numbers, and special characters significantly boosts your security. At the same time, two-factor authentication (2FA) tools make it necessary to gain access to your phone, making the hacker's job much more challenging.
Conclusion
The digital world is filled with constantly evolving threats. The latest virus types like mindware, clop ransomware, RaaS hacker groups, Onyx, Zeus Gameover, and other mentioned examples have been causing massive chaos, and we've elaborated on how these latest virus attacks evolve, infect, spread, and steal financial information.
Fortunately, cybersecurity measures have also evolved significantly in the last few years. Together, they create a safe environment for data, allowing users to guard their files against advanced cyber threats, but only with changes to their browsing, downloading, updating, and scanning habits.
And even if the latest malware threats go through your cybersecurity defenses, apps like Wondershare Recoverit work wonders in recovering corrupted and virus-affected files. Reliable backup software like Wondershare UBackit also makes it easy to restore your vital data in case of a virus attack.
It's highly advised to use these tools instead of paying a ransom, as it doesn't guarantee that attackers will return your files.



 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















