Have you inserted any USB drive in your system that was infected and led to loss of data? Know that you're not the only one. Many smart attackers will leave these malware-infected USB drives near you. That curiosity sparks in, and you start using the USB.
While this sounds tempting, you must never insert any unknown USB device in your system. That is exactly how the USB drop attacks happen. Several people have been victims of USB drop attacks, which are incredibly harmful. As soon as the attackers gain remote access to your system, they will wipe off all the data.

This can be a very risky thing to opt for. However, when a USB drop attack happens, you will lose some critical data from your system. This blog will guide you through all the potential ways through which you can understand what is USB drop attack, how to prevent the risk of USB drop attacks and what to do when something happens.
Try Recoverit to Recover Lost Files when USB Drop Attack Occurs
Security Verified. Over 7,302,189 people have downloaded it.
In this article
Part 1: What is a USB Drop Attack?
The USB drop attack refers to the attack through a USB code. For example, the host attacker will keep the USB drive containing malicious code in front of the victim as if it were a mistake. The victim individual may then place or connect the infected USB to their computer. Now, the USB acts as a medium for the hacker to conduct their attacks by infecting the systems. Most of these attackers follow the USB Drop attack tutorial and affect the systems.

Part 2: How Does It Take Place?
The USB drop attacks usually happen because of innate curiosity. If you accidentally plug in the device on your computer, it will lead to severe risks. Some of the common ways through which the USB drop attack happens are as follows:
- Social engineering
USB baiting is one of the common types of social engineering baits that will directly impact the system. It usually tricks the gullible users who will click into files that have very curious-like names. However, these folders contain malicious codes and links that may damage your system. Once you click the links, you'll be guided to the phishing sites that directly affect your credentials and steal all your information.
- Malicious code
Malicious codes in USB devices must be one of the most common ways a system may be attacked. Users will be redirected to another website when they click on the file or link to get important information. The malicious code will get implanted into the system, leading to severe risks that can damage the computer's data.
- Zero-day attack
The main purpose of the zero-day attack would be to damage the system. The malicious code will be there in the infected USB. It will use all the unpatched vulnerabilities, infecting the software and eventually leading to system damage. Furthermore, it will be very much like a malicious code attack that can also exploit hidden vulnerabilities. However, if the patch isn't fixed, the virus will continue to be deployed, affecting the entire system.

- Human Interface Device (HID) spoofing.
This is a sophisticated type of USB drop attack. The HID spoofing will misdirect the computer, making it believe it is connected to the keyboard. As soon as it is plugged in, the preconfigured keystrokes will give hackers remote access. As a result, it will end up damaging the entire system.
Part 3: Types Of USB Attacks
There is a wide range of USB attacks which can hamper the functioning of the entire system. These will either lead to data loss or corrupt the entire system. Some of the common types of USB attacks are as follows:
1. Rubber Ducky: This is a commercial keystroke injection attack which was released back in 2010. Rubber Ducky will start acting like a keyboard when it is connected to the computer. As a result, it will inject any preloaded keystroke into your system, thereby hampering the entire performance and causing data loss.
2. USBdriveby: It acts as a cover installation process for the backdoor, thereby overriding the DNS settings for the unlocked OS X host. It will be connected via the USB drive, and within a few seconds, it will act like a USB mouse and keyboard, affecting the system and leading to data loss.
3. PHUKD/URFUKED and Evilduino: Although Evilduino is similar to the PHUKD/URFUKED attack, it relies on using Arduino microcontrollers. It works specifically by acting like a keyboard or a mouse. Once it starts acting like that, it will also send mouse cursor movements or keystrokes to the host attack based on the preloaded script.

4. Unintended USB channel: Any proof of concept (POC) USB hardware attack will exfiltrate the data. However, This data attack will be based on unintended USB channels like USB speakers, which might lead to complete data exfiltration.
5. Attacks On Wireless USB Dongles: Attacks on wireless USB dongles have become extremely common. This type of attack was first launched by Samy Kamkar as the KeySweeper attack. This tool covers the logs and decrypts the keystrokes across various Microsoft RF wireless keyboards.
6. RIT attack via USB mass storage: This type of attack was mentioned in a research paper. The RIT attack will eventually lead to changing the content file. This attack will only be done as long as the USB device is connected to the computer.
7. Default Gateway Override: Default Gateway override is quite a common issue, especially because it uses the microcontroller for spoofing a USB ethernet adapter. The adapter will eventually override the DHCP settings and hijack local traffic.
Part 4: Popular USB Drive Threats for 2024
In 2024, several systems were prone to various USB drive threats, leading to severe data loss and other issues. Some of the standard USB drive threats that proved to be a problem in 2024 include the following:
1. SOGU Malware Infection
The SOGU malware infection happened to remain quiet but stole the data. The stealth nature of SOGU malware infection was aimed at avoiding any detection by the traditional antivirus software. When connecting to the system, a USB device infected by SOGU malware will install codes, and sensitive data will be stolen. Furthermore, it will also grant access to various unauthorized access channels.
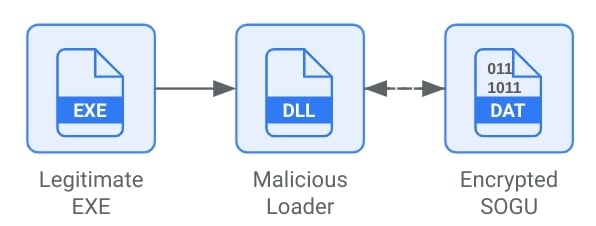
2. SNOWYDRIVE Malware Infection
The SNOWYDRIVE malware variant was designed to spread via USB drives and exploit vulnerabilities in the target system. It may use different techniques like polymorphic codes and fileless execution to prevent detection and compromise systems. When SNOWYDRIVE is activated, it will exfiltrate the data and install backdoors for unauthorized access. Furthermore, it will also grant remote access, which can lead to infiltration via affected networks and pose severe security risks.
3. WispRider Infection
The WispRider infection will damage the system as it bypasses the traditional security system and leverages the USB device. Therefore, it will lead to severe infiltration issues as it follows the zero-day vulnerabilities exploitation. Moreover, it can cause vulnerabilities that compromise the data security systems. The WispRider infection can severely threaten the integrity, confidentiality and availability of data across the target systems and data.
Part 5: How to Prevent USB Drop Attacks?
The USB attacks follow a multi-layered approach. Therefore, it is essential to adopt proper measures to avoid it. Some of the key ways to understand how to protect data from USB drop attacks are as follows:
- You must integrate endpoint security solutions across all the sections. This will help detect and block any kind of malicious software that may try to attack the system, which may originate from the USB drive.
- Try to regularly update the system. Regularly updating the device's operating system can help ensure that the operating systems are performing well. Furthermore, the security software will also prevent security gaps and prevent the risk of USB devices being exploited.

- You must use proper USB security tools that can block unauthorized access to the system. The software must monitor the activity of USB and enforce policies to maintain device security.
- If your system has an autorun feature for USB drives, you should disable it as soon as possible. The autorun feature will start using the USB drive and won’t require permission which can further lead to major risk of data loss. Then you must figure out how to fix USB drop attack.
- You must use encrypted USB devices in your system. These can play an important role in keeping the USB devices working, preventing the risk of attacks and ensuring the system data stays protected.
- Use a reliable tool that can control the safety of your USB device at all points. You must check the security features that can prevent the risk of unauthorized access to any kind of sensitive information or data. Moreover, it is also important that you keep a check on the system's remote management capabilities.
- You must use a USB device management system to monitor the use of USB devices in your system. It can play an important role in configuring the devices, thereby preventing the risk of device usage and activity.
Part 6: Lost Files to Malware or Viruses? Recover Them with Wondershare Recoverit
Have you accidentally lost files because of malware or virus? You should try a USB data recovery software such as Wondershare Recoverit. Wondershare Recoverit is one of the most trusted Windows tools, and it can play an important role in recovering any kind of lost data across different devices. Therefore the tool can also be useful to recover data if USB drop attack happens.
Wondershare Recoverit has a very user-friendly interface that even beginners can use smoothly. This will ensure that you can navigate and use the software to recover data from loss due to USB drop attack. You can visit the various memory areas and save the search results. Moreover, it will support data recovery across sudden deletion, which can be helpful for system crash data recovery.
Wondershare Recoverit is available for free download for Windows users. Therefore, you must download and install it on your device to get started with the data recovery process. You may follow the steps given below to use Wondershare Recoverit to recover files deleted by malwares or viruses from various devices:
Step 1: Launch the Software
Once the software is installed in your system, launch it. Since you are to recover the files from the USB, choose the USB option under the Hard Drives and Locations section.

Step 2: Initiate The Scan
As you select the USB drive, the files will be scanned. This is a Quick Scan, which can take a few minutes for data recovery. If any file is lost or recovered, you can conduct the All-Around Recovery scan. This is the deep mode scan, which can help scan and search for files. You may have to wait a few extra minutes, but it is worth it.
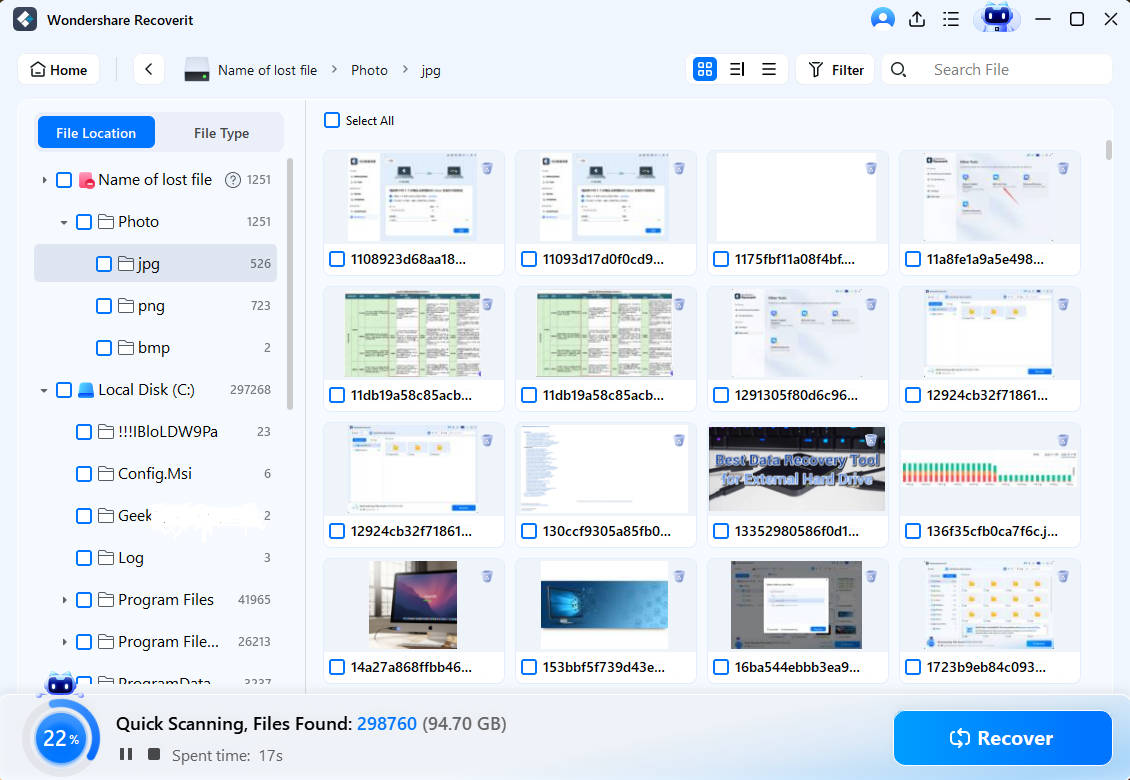
Step 3: Preview and Recover the Files
After scanning, the data will be available on the main screen. You can apply filters and refine your search. Now that the files are available on screen, you can click on the preview feature to get a complete overview. If the files are what you have been looking for, click on Recover. Now, you can select the location to save the files and finally hit the Recover button.
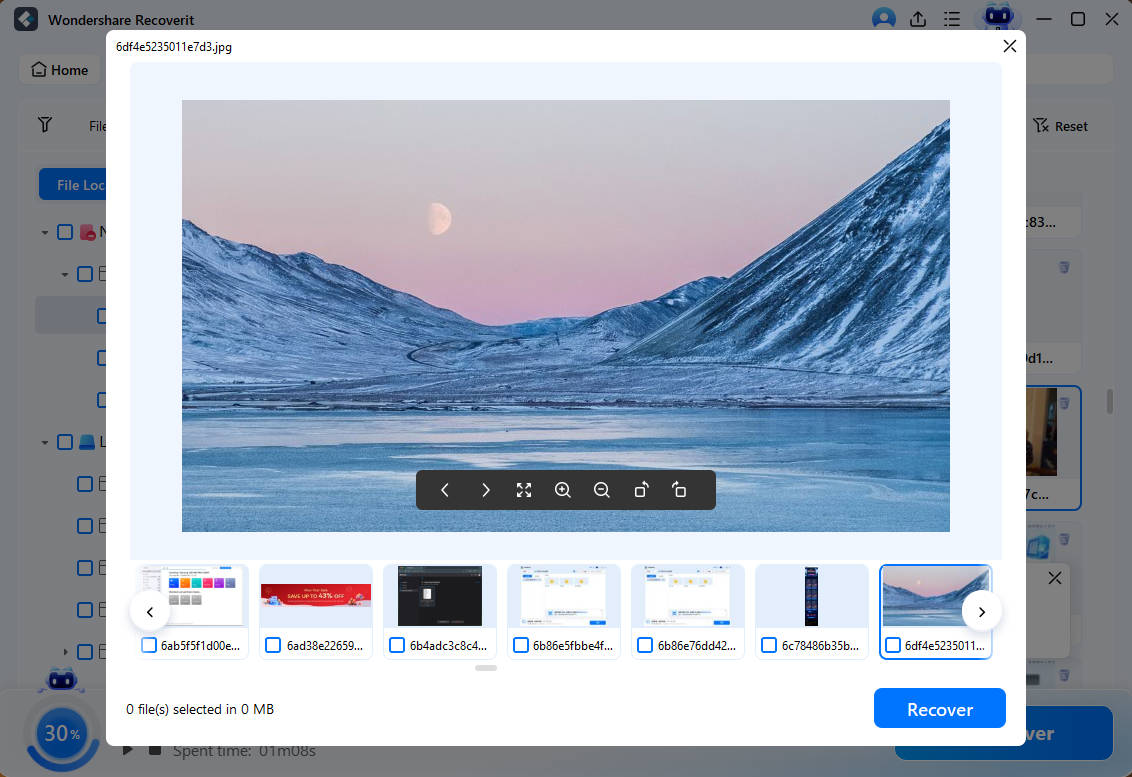
Related Video >>: How to Recover Lost Files After Virus Attacks?
Conclusion
Getting your files lost due to any malware or virus attack is a very common issue. You must understand this process of USB drop attacks and try to initiate the data recovery. USB drop attacks are very common and can affect the entire system. As a result, you may end up losing a lot of data and have viruses all over your system due to the USB drop attack. Therefore, you have to use data recovery software like Wondershare Recoverit. You can get back your data through the data recovery software regardless of how bad the loss scenario is. Going forward you must that you are following the prevention techniques.
Try Recoverit to Retrieve Lost Data After Virus Attacks
Security Verified. Over 7,302,189 people have downloaded it.
FAQ
-
1. What is a USB drop attack?
A USB drop attack is a cyber-attack in which the USB drive contains malware and is left at an unknown location. Any unknown individual may pick it up and connect it to their computer. This can, therefore, attack the system, leading to numerous issues. -
2. What should I do if I find an unknown USB device?
If you find an unknown USB device, you must refrain from connecting it to your computer. There is a high chance that this USB device is corrupted or contains some malicious software which can be used for accessing personal information from your computer. -
3. How can Wondershare Recoverit help in case of a USB drop attack?
A USB drop attack can often lead to the system being hacked and the data being erased. The lost data can, therefore, be recovered using Wondershare Recoverit.


 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















