AI hacking has a real potential to shake the foundations of cybersecurity and render it powerless against malware attacks, data theft, and fraud. Given this, Every business and individual should take measures to protect their digital assets from AI hacking.
What is it, exactly, and how does it operate? Is there any way you can protect yourself against AI-driven cyber threats? Let's see.
In this article
What Is AI Hacking?

AI hacking is the deployment of malicious AI-powered tools for cybercriminal purposes. That includes the usual arsenal – fraud, identity theft, and data theft – but it doesn't stop there. However, as is true with everything touched by artificial intelligence, AI hacking also implies new possibilities.
For example, being open to bugs and vulnerable to human error, prompt engineering, and hacking, AI is especially dangerous in the business environment, where cybercriminals can use it to crawl into companies' critical infrastructures and stay there for extended periods, causing damage.
Exploring Siri Gemini and understand its role in Apple future artificial intelligence plans.

Types of AI Hacking

There are already countless applications of AI in hacking. Some of the most popular (and dangerous) AI hacking practices include:
📝Code generation
As you probably know, ChatGPT is fluent in code and can, unfortunately, craft malware and other types of malicious code. It can also do that fast, with the precision and sophistication of a gifted coder. Even worse, it can turn some of its own adaptive capabilities into code.
AI has advanced vectors that enable self-patching, which could be a complete game-changer for cybercriminals. Why? Because applied to malicious code, self-patching can help malware become undetectable and untraceable. AI could teach it to update its own code in real-time.
🤖Data poisoning
Attackers can turn AI against you by means of data poisoning, which can be administered in two ways. One is to insert fake information into the training algorithm and have AI spread incorrect, misleading, and dangerous information or see malicious code as good software.
But criminals with access to AI training sets are bad news in more ways than one. The second way they can use data poisoning for attacks is to detect and exploit vulnerabilities. Training algorithms can be manipulated into generating a point of entry for adversarial AI attacks.
🔨Password cracking
Password cracking is traditionally associated with brute force attacks, where hackers use trial and error to guess the correct combination of letters and symbols in a password. But now, AI can guess random strings at incredible speed, especially after you feed it the right information.
👓Deepfake generation
Everyone knows how easy it is to copy someone's likeness using AI, but we don't think enough about this in terms of fraud and disinformation.
For example, malicious actors can use AI to trick your bank into giving away your information - and your money. Deepfakes can also spread misinformation and create confusion about critical issues and events, such as terrorist attacks, pandemics, bomb threats, etc.
🎯Social engineering
In close relation to identity theft and generation are social engineering attacks such as phishing. AI can write you a persuasive email "from your boss” asking you to send him your login credentials. It could become virtually impossible to distinguish fake messages from authentic emails.
In fact, an AI-enhanced phishing attack has yielded a success rate of over 60% in a recent experiment by Prompt Engineering Institute. In the experiment, AI is able to use targets' data to create demographic and psychographic profiles and generate synthetic personas with matching personalities.
👀Vulnerability discovery
More often than not, new software is being developed and shipped with built-in vulnerabilities. AI could be easily programmed to search for and automatically detect these weak points.
AI Hacking Tools

- XXXGPT
- Wolf GPT
- FraudGPT
- WormGPT
As if all this wasn't already dangerous enough, ChatGPT is no longer the only potential threat to your cybersecurity. Hackers are using the AI and LLM principles to develop their own AI tools that are easy to use and designed specifically for malicious activity.
The most recent examples of so-called black hat AI tools are XXXGPT and Wolf GPT.
XXXGPT and Wolf GPT are dubbed ChatGPT's evil step-cousins. Made by hackers and intended for hacking, these tools allow anyone to generate and use malware with complete confidentiality. Their users don't even need extensive technical knowledge or hacking experience.
In particular, XXXGPT equips hackers with ATM and POS malware, botnets, crypters, cryptostealers, infostealers, keyloggers, and RATs (Remote Access Trojans). This AI hacking tool assists theft, ransom, data theft, identity theft, and fraud. Also, it gives you the tools to hide your malware and identity.
Wolf GPT is similar. In addition to cryptographic malware that is virtually impossible to detect and fend off, this tool provides complete anonymity to hackers. It's also widely used for orchestrating and executing phishing and other types of social engineering attacks.
Before XXXGPT and Wolf GPT, there were others, which are still being actively used for cyber attacks. Some of the most notorious AI hacking tools besides these two are FraudGPT and WormGPT, both of which are primarily used to generate deceptive content used in phishing attacks.
How to Defend Against AI Hacking

Is there anything you can do to protect yourself from AI hacking? Cybersecurity experts have shared several recommendations that make sense. Here's what you need to do:
📍Never miss an update
Nobody's stressed about AI threats more than software developers. Most of these teams work double shifts to keep your critical systems safe from harm. The only thing you need to do is run your updates when they are available. These security patches are essential to your safety.
📍Use random passwords
The unbreachable password is 12 characters long and includes a combination of upper-case and lower-case letters, numbers, and symbols. It's also a random string that cannot be guessed based on your personal information, lifestyle, hobbies, likes, or social media activity.
📍Have a reliable antivirus
Major antivirus tools are already being updated with mechanisms to anticipate and block AI attacks, especially malware. If you don't have antivirus software or have been thinking about getting a different one, now is a good time to do your research and choose the best.
📍Watch out for phishing
Phishing messages are usually poorly written and include many grammatical and spelling errors, but AI has become fluent in all human languages and discourses. The best way to spot AI phishing is by looking for urgent calls to action, attachments, or Image names that require your attention.
📍Practice data safety
Learn to take better care of your data – whenever you can, avoid sharing your personal information, sensitive files, and passwords online. Employ encryption tools like BitLocker and back up your data regularly. If you do not have the habit of keeping data backups, Use tools like Wondershare Recoverit to reverse data-loss scenarios caused by AI hacking.
Recoverit can rescue lost documents, images, videos, audio, emails, and other types of files, from virtually any device and in any data loss scenario, including virus/malware attacks. It is an effective and versatile solution that is also very easy to use:
- Download Wondershare Recoverit from the official website and install it on your computer.
- After you launch Recoverit, select a location where you want to start the recovery process.

- Selecting a desired location on your computer will initiate an all-around scan of that drive.
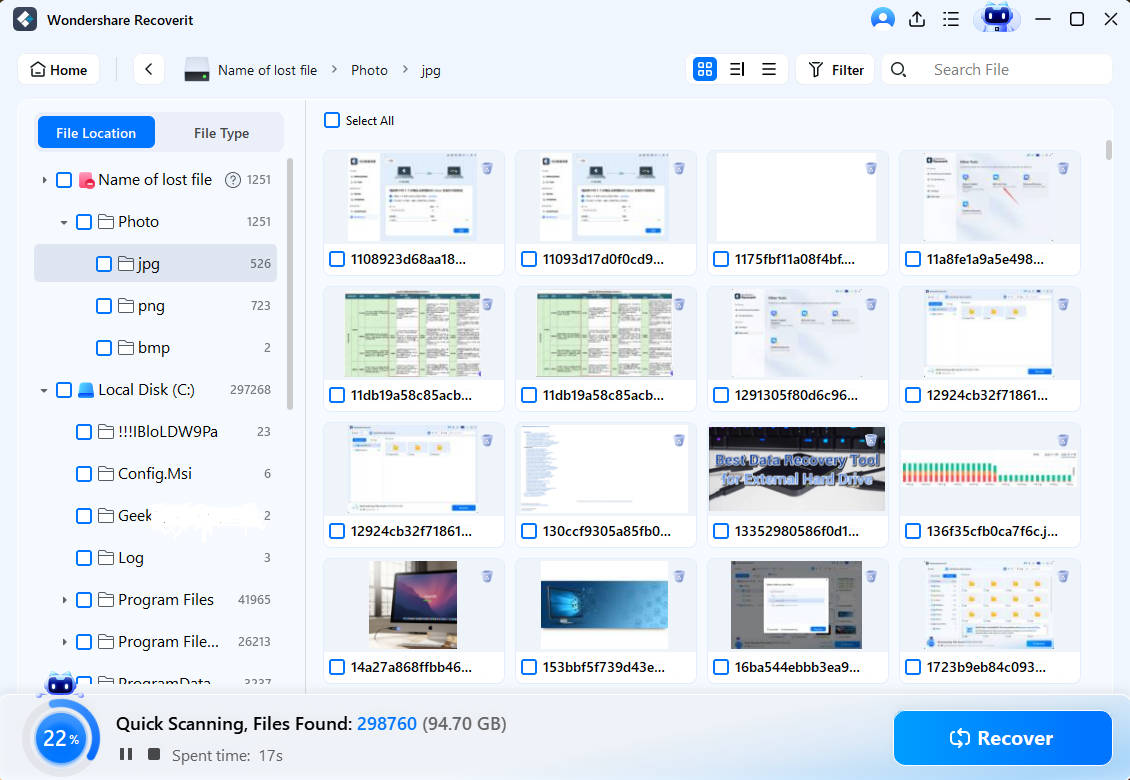
- While the scan is in progress, you can watch your lost files being dug up on the screen.
- You can press Pause or Stop at any moment and click Preview to check recoverable files.
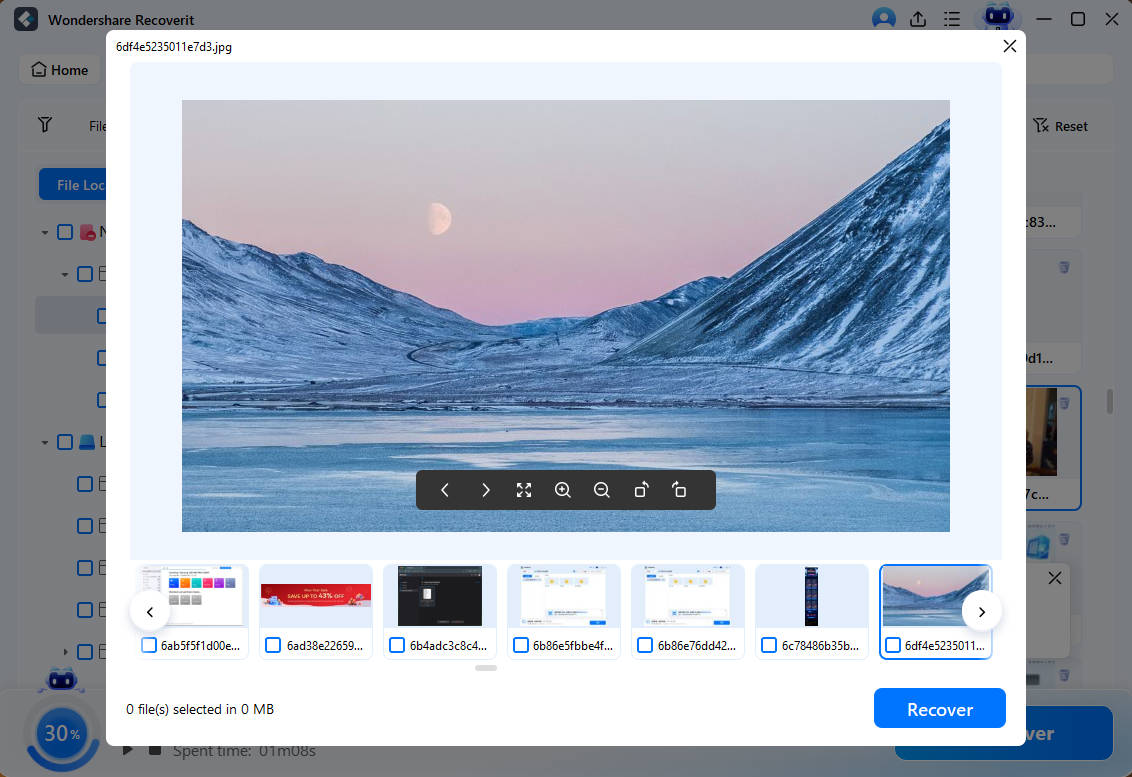
- Select the files that you want to keep and click Recover to save them to your computer.
- To finalize data recovery, choose a safe destination for retrieved files and click on Save.
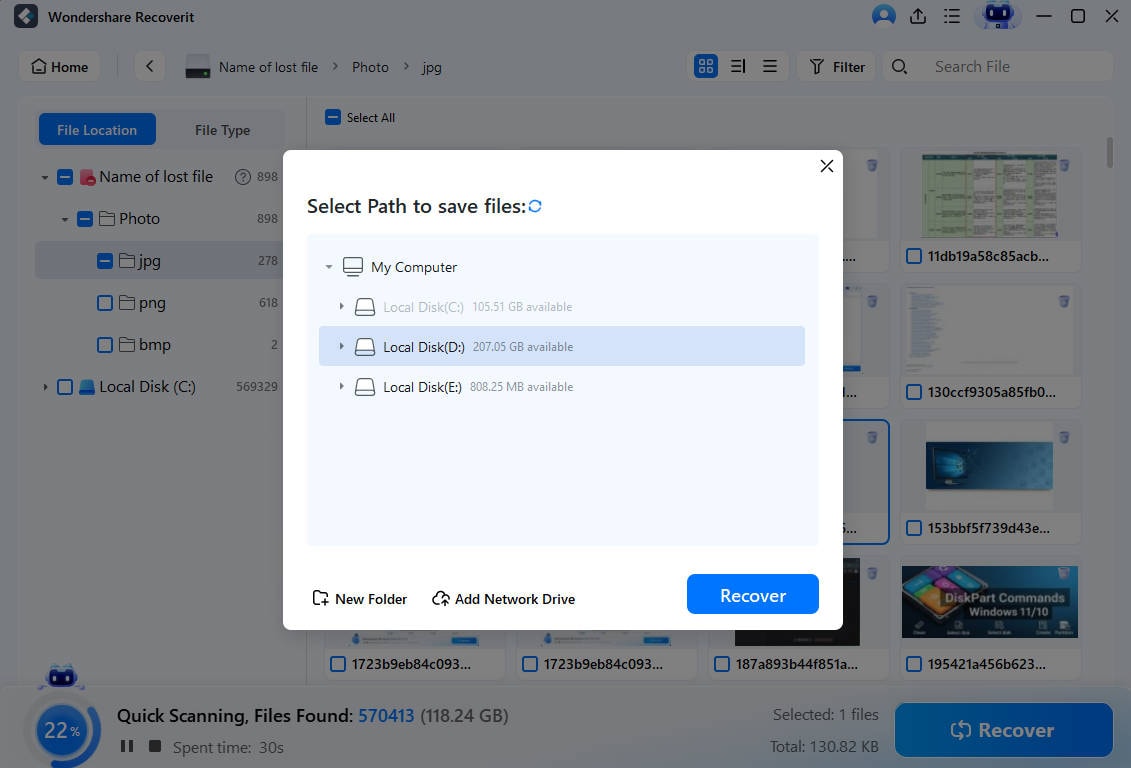
📍Learn about AI and ML
Know your enemy. Subscribe to popular AI and ML blogs and stay in the loop with recent threats. Some of the best learning resources on this topic include OpenAI, Machine Learning Mastery, Distill, The Berkeley Artificial Intelligence Research, MIT News, and There's an AI For That.
📌Train your employees
Whether you're running a small business or a large organization, you must teach your employees to avoid making mistakes that can make your entire network vulnerable. It especially applies to recognizing phishing and social engineering attacks and handling sensitive data.
📌Normalize security audits
Savvy organizations have already updated their security policies to include new guidelines on how to use AI-powered tools and what to do in response to AI-driven attacks. In addition to that, you should also conduct regular security audits that will help you reveal potential weaknesses.
📌Employ a security expert
A security breach can cost you a lot of money and time. Many victims of cyber attacks end up losing their reputation and customers as well. The price of all that is way bigger than the price of employing a cybersecurity expert, which is what many smart companies are doing right now.
📌Join collaborative defense
Company heads and IT teams are joining academic institutions, government agencies, and AI experts in a collaborative defense network where they share practical knowledge, real-life experience, and proven practices that help keep AI attacks at bay. Find a partner from your industry.
Conclusion
AI hacking is a real threat that should not be taken for granted, but there's hope. Malicious attacks, no matter how automated, efficient, or sophisticated, can be predicted and stopped with the right combination of caution, prevention, vulnerability assessment, and active defense.
For this to work, we need our good judgment and the best cybersecurity tools. Collaborative defense is showing exemplary results as well. AI is yet to play its most important part in cybersecurity, where it can help us analyze behavior, identify anomalies, and predict cyberattacks in time.
FAQ
-
What is the difference between AI hacking and ethical hacking?
AI hacking is when someone uses artificial intelligence to gain unauthorized access to networks, computer systems, or devices. Black hat AI hackers use AI tools to carry out cyberattacks, spread malware, and steal confidential data for their own profit. When we talk about hacking, it usually involves illegal activity. Ethical hacking, on the other side, uses the same techniques and tools for a different purpose – to find system vulnerabilities before they get explored by black-hat hackers. -
Is your data safe with AI?
Is your data safe with AI? It depends. AI platforms and tools are trained on enormous datasets that include information posted online throughout the years. This data is harvested from search engines and social media pages, as well as online forums and forms. Its security depends on many factors, such as how developers use it, where it is stored, and who else can access it.



 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















