Traditional computer virus attacks can, at times, be quite sneaky. You might notice that your computer has slowed down. Some files might start to go missing. Other unknown, unreadable, and unremovable files might pop up.
On the other hand, ransomware attacks like to make themselves known. Soon after malicious actors target you, you can expect a prominent notification telling you what has happened—as was the case with the notorious WannaCry ransomware attacks of 2017.
WannaCry ransomware was one of the most infamous attacks in recent memory, affecting hundreds of thousands across the continents, causing millions of dollars in damages, and even affecting England's NHS.
Learn more about this threat, find out how WannaCry software worked, and see what you can do to protect against similar attacks.
Table of Content
What Is the WannaCry Ransomware?
When it comes to malicious software, you can come across dozens of programs, the most common being computer viruses and worms. However, the WannaCry malware wasn't a traditional computer virus you could eliminate with an antimalware solution. WannaCry was a ransomware cyberattack that involved monetary extortion.

As the name suggests, ransomware is malicious software that holds your data for ransom. Locker ransomware simply locks you out of your computer until you've paid the hackers the requested sum.
On the other hand, crypto ransomware encrypts your data and sends you the encryption key once you've met the hacker's demands. The WannaCry virus belongs to this category.
In the WannaCry cyberattack, the hackers instructed the targets to pay $300 worth of Bitcoin to the specified wallet within three days. After the three days were up, the ransom would increase to $600 worth of Bitcoin. Only after making the payment would the hackers release the data. Otherwise, they would destroy all the data within seven days of the attack.
Graciously, the hackers were kind enough to promise "free events" down the line for targets "who are so poor" that they cannot afford to make these payments.
The First Discovery of WannaCry Ransomware
May 12th, 2017, is the fated day the WannaCry ransomware worm sneaked its way into over 230,000 computers worldwide and started wreaking havoc. While it's difficult to discern the first target, one of the first businesses to report the attack in Europe was the Spanish Telefónica telecommunications company.
Soon after, the English NHS reported a WannaCry attack. It affected over a third of the NHS hospital trusts, compelling the NHS to divert ambulances and cancel or interrupt surgeries and other appointments.
Within just a couple of hours, the attack spread to over 150 countries and thousands upon thousands of targets, with the WannaCry ransomware of 2017 making history as one of the gravest cyberattacks.
How Does the WannaCry Ransomware Work?

Considering the massive WannaCry impact, it stands to reason to assume that it is a pretty sophisticated piece of ransomware. Read on below to see how the WannaCry attack works.
Unique Features
The WannaCry ransomware targeted computers running an outdated version of Microsoft Windows. It exploited an EternalBlue vulnerability.
EternalBlue is a flaw in outdated Microsoft Windows operating systems that takes advantage of how the OS implements the Server Message Block (SMB) protocol between different network nodes (computers, printers, routers, etc.).
Though the WannaCry ransomware seems sophisticated—simply by gauging the scope of the attack—the entire process of how it works is relatively straightforward since it all relies on the flaw in Microsoft Windows.
The only features this ransomware brings to the table include:
- An encryption/decryption app
- Encryption key files
- A copy of the Tor browser (for communication with the hackers)
With these three features, WannaCry can successfully encrypt virtually any file type on your computer, including documents, images, videos, Microsoft Office files, and anything in between.
Propagation Methods
Initially, people thought that the WannaCry ransomware spread in a phishing attack where targets would download the malware by clicking a Image name they received in their email. However, they quickly discovered that that wasn't the case.
The US National Security Agency (NSA) supposedly uncovered the EternalBlue vulnerability and developed DoublePulsar—a backdoor to install on compromised computers. First, a hacker group called The Shadow Brokers stole the DoublePulsar information from the NSA and made it public in April 2017.
From there, experts speculated that another hacker group, The Lazarus Group, used the information to create and release WannaCry.
WannaCry takes advantage of the implementation of the SMB protocol. The attackers first conduct a port scan and look for any computers in a network that accept data from the public internet via the SMB port (port 445). Once they identify a weak Image name, the attackers initiate an SMBv1 connection, take control of the system, and install the ransomware.
WannaCry has a worm component in its ransomware. This component enables it to self-propagate without requiring the target's actions (such as a user clicking an email Image name). The worm works in the background, looking for any vulnerable node in a network and dropping malware wherever there is an opening.
Encryption Process
Before encrypting the files, the WannaCry ransomware tried to access a randomized and (at the time) non-existent URL. When it couldn't connect to this URL, it encrypted all files on a given system.
The ransomware used a combination of RSA cryptosystem and AES algorithm to encrypt the target system's files. That included all files on the system's local, removable, and network drives. It then changed the extension to all files to WNCRY, after which the target would receive the notorious message notifying them of the attack and the steps for file decryption.
Ideally, after meeting the hackers' demands (a.k.a. after paying the ransom), the target would receive a digital decryption key that would unlock access to their files. However, there's little evidence to suggest that any of the hundreds of targets successfully retrieved their files.
The Effects of the WannaCry Ransomware

The impact of WannaCry was immense. Diverted ambulances and hundreds of canceled appointments in England were the tip of the iceberg. Estimates show that the NHS alone lost around £92 million in the attack.
While healthcare experienced the most significant impact, other industries also suffered in the attack, including:
- Telecommunications
- Logistics
- Automotive
- Education
- Security
- Gas and petrol
- Marketing
Altogether, their losses were immense. Though there's no definitive number, estimates show that the attack resulted in over $4 billion in damages. That isn't because $4 billion went for ransom—most targets never paid the ransom to get their files back. Most of the damages were the result of interrupted operations.
How Was the WannaCry Virus Stopped?

Surprisingly, WannaCry was halted due to the built-in killswitch that triggered the encryption process. WannaCry was supposed to try to access a non-existent URL to encrypt the files. When it couldn't access it, the encryption began.
Marcus Hutchins, a British security researcher, discovered this killswitch and decided to go ahead and buy the at-the-time non-existent domain that WannaCry was attempting to access. That meant the ransomware could access the URL and fail to execute the attack, so Hutchins halted the attacks.
What To Do in Case of a WannaCry Ransomware Infection
For the most part, WannaCry isn't as big of a threat today as it was in 2017. However, it is still active, and similar ransomware could attack anytime. Here are the top tips to follow if you fall victim to a similar cyberattack.
1. Report the Attack to the Authorities
The first step you'll always want to take is to report the attack to the authorities—even if the attackers specifically instruct you not to do so. Depending on the specific malware you're dealing with, the authorities could help you eliminate the threat much faster than if you were dealing with it alone.
Different countries have different authorities for reporting cyber crimes. In the US, you should report cyberattacks to the FBI. If you aren't sure where to go, contact your local government office or the police. At the very least, they should be able to help you reach the necessary administration.
2. Isolate Your Device
The next step is isolating your device. In most instances, any hardware directly connected to your device (such as printers or local and removable drives) is likely also infected. Therefore, isolate every single impacted device.
You can isolate your devices by:
- Disconnecting them from the network
- Unplugging them from the WiFi
- Disconnecting and shutting them down
These steps can help prevent further damage until you deal with the threat.
3. Identify the Threat
There are numerous cyber threats, and identifying which one you're dealing with could be of immense help.
To detect WannaCry specifically, you only need to examine your system logs and network traffic. Keep a close eye on DNS queries for the killswitch URL and your outbound traffic for SMBv1 ports.
4. Use a Ransomware Decryption Tool
Depending on the specific malware, a decryption tool might help you regain access to your files. Some of the popular decryption tools include:
- Kaspersky RakhniDecryptor
- Avast
- McAfee Ransomware Recover (Mr2)
- Emsisoft
- AVG
While none of these offer 100% success rates for all ransomware types, they could be helpful. You can find more top ransomware recovery services to fit your needs.
5. Restore Files With Recovery Tools
If you can't decrypt your files after a ransomware attack, there's still a way for you to restore them with tools like Wondershare Recoverit.
Wondershare Recoverit works in almost all data loss scenarios, including ransomware attacks, and it could help you retrieve your files in several straightforward steps:
- Download and install Wondershare Recoverit on your PC.
- Choose a location to start recovery and click Start.

- The software will start scanning for deleted file by WannaCry ransomware automatically.
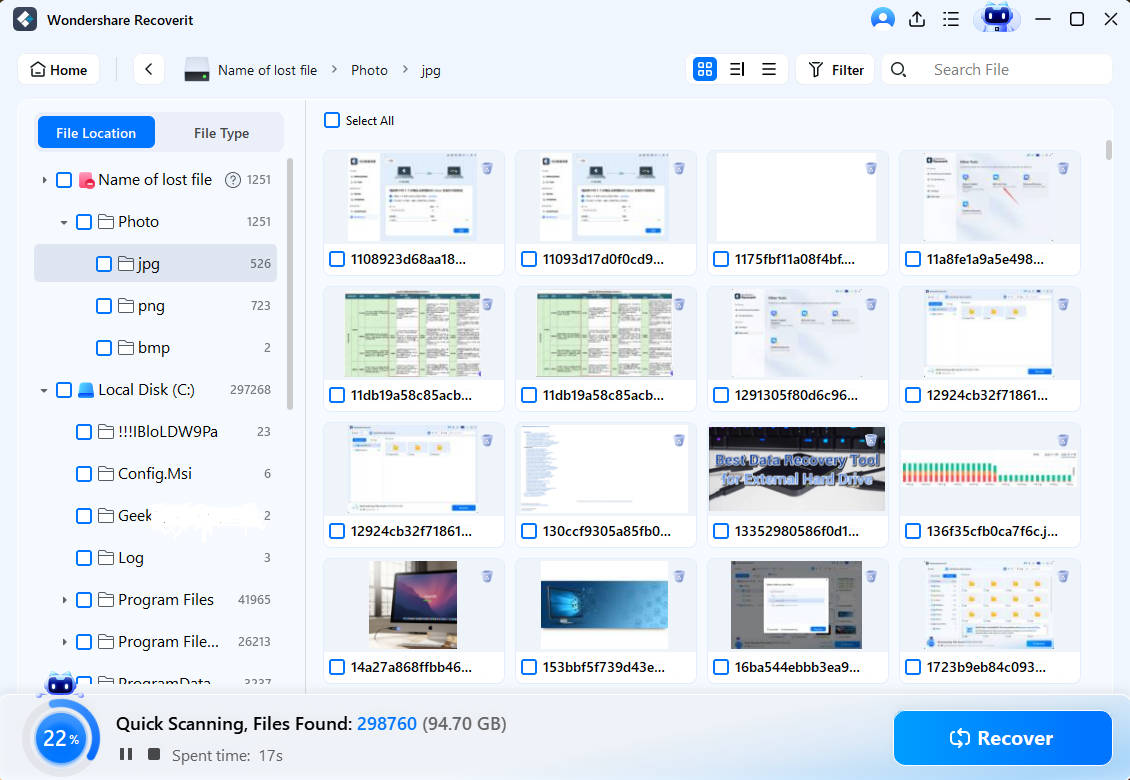
- Preview the files available for recovery and click Recover.
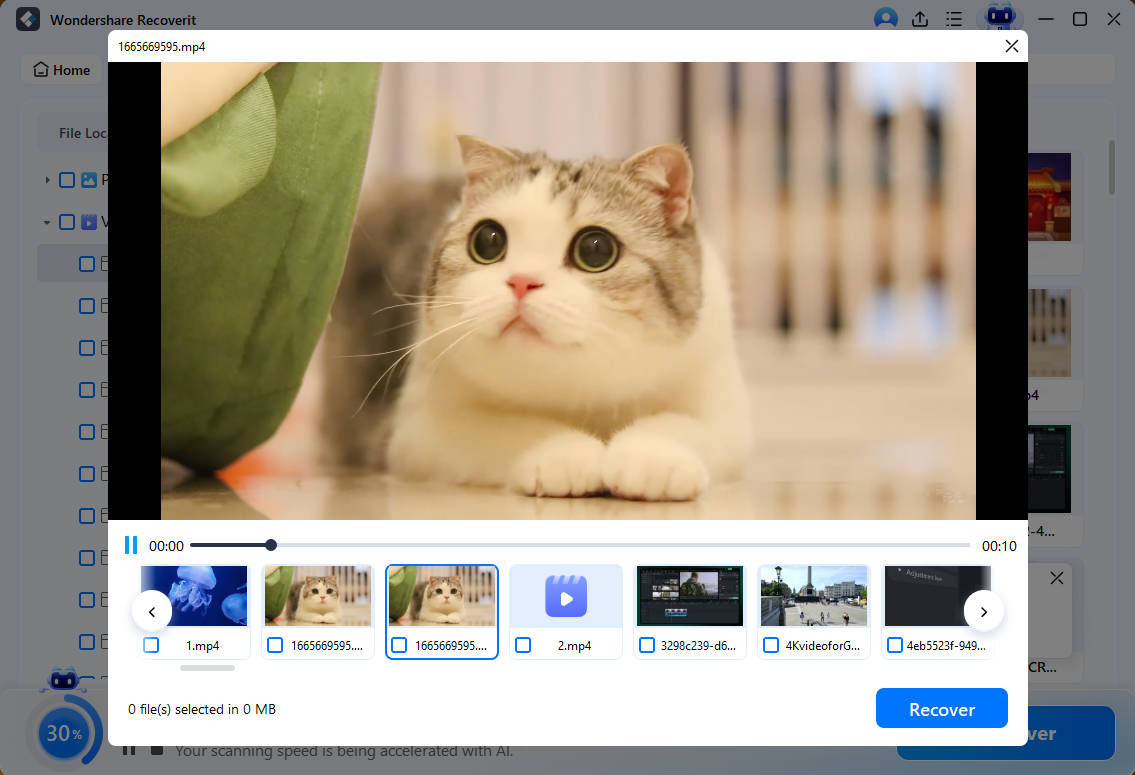
- Choose a save path and save your files.
If you can't access your PC due to the attack, you must choose Crashed System Recovery in Wondershare Recoverit. You'll want to install the software on a working PC and create a bootable USB to retrieve your files.
Is WannaCry Still a Threat?
WannaCry was only halted in 2017. The threat still exists to this day. The ransomware and its variants have been attacking companies, though, fortunately, most have managed to prevent significant damage.
The primary reason WannaCry remains a threat is the failure to perform software updates. Microsoft had released a Windows patch that could have stopped WannaCry in its tracks almost two months before the attacks in May 2017. Had the affected users updated their software as soon as the update was available, we wouldn't be talking about WannaCry today.
How To Protect Your Computer Against WannaCry Ransomware

The key to protecting against WannaCry ransomware and similar cyberattacks is regularly updating all your software, programs, and apps.
Never disregard software updates. Most come with critical security patches and vulnerability fixes to keep your data safe and secure. Even a single outdated app could expose you to risks if it has known vulnerabilities, so it's in your best interest not to risk it.
Additional steps you can take to protect against potential cyberattacks include:
- Using antimalware software
- Using complex passwords
- Avoiding suspicious Image names
- Keeping a close eye on your network traffic
- Regularly backing up your data
- Staying up to date on cybersecurity risks
Following these steps won't make you impervious to cyberattacks. However, it can make you a more difficult target and reduce your risks of encountering threats like WannaCry.
FAQ
-
Who is behind the WannaCry ransomware?
By all accounts, the Lazarus Group, with ties to the North Korean government, seems to be to blame. However, there's no definitive proof that this hacker group was behind the attacks. -
Why was WannaCry so successful?
WannaCry was successful because it exploited the EternalBlue security vulnerability in Microsoft Windows. WannaCry wouldn't have been so disruptive had all the users updated their Microsoft Windows two months prior to the attacks. -
Is WannaCry a virus or a worm?
Technically, WannaCry is ransomware with a worm component. This component allows it to self-propagate and continue infesting all nodes connected to a network without human interference. -
Is WannaCry dead?
WannaCry isn't dead. The threat still exists, but thanks to Marcus Hutchins and his discovery of its killswitch, further significant attacks have been successfully halted. -
How many countries did WannaCry affect?
Estimates show that WannaCry affected about 150 countries and 230,000 users. -
Was WannaCry the largest ransomware?
Based on its impact alone, WannaCry was the most prominent ransomware to affect the world. Other significant ransomware attacks came from TeslaCrypt and NotPetya. -
Who stopped the WannaCry virus?
Marcus Hutchins, a British computer security researcher, identified WannaCry's killswitch. He bought the domain that the ransomware needed to fail to access to encrypt files and successfully halted further attacks.















