Recovering HHJK files is a major problem for computer users. Harmful software can lock important documents, photos, and videos, making them unusable. This causes stress for both individuals and businesses. Files with the .hhjk extension are fully encrypted and cannot be opened with regular programs.
Recover HHJK file operations require quick action and the right tools. Time is crucial when dealing with encrypted files. Waiting too long can make recovery harder. Some temporary files may get deleted. Your system might suffer more damage. This guide will show you simple steps to restore your files safely.

HHJK Ransomware attacks are becoming more common each day. Cybercriminals target individuals and companies alike. But you don't have to pay these criminals. There are proven methods to recover HHJK file data without giving in to their demands.Paying the ransom doesn't guarantee file recovery. Many victims never get their files back even after payment. Some criminals disappear after receiving money.
In this article
Part 1: What is HHJK Ransomware?

What is HHJK Ransomware is a question many victims ask after an attack. Many victims wonder what HHJK Ransomware is after being attacked. It belongs to the STOP/Djvu ransomware family and locks personal files by adding the .hhjk extension. These files become unreadable until they are decrypted. The ransomware family has created many versions, each with a different file extension. HHJK is one of the latest variants.
HHJK Ransomware spreads through malicious email attachments and fraudulent software downloads. Once inside your system, it rapidly encrypts important files, including documents, photos, and videos. The process takes only a few minutes. After encryption, the ransomware displays a ransom note on your desktop and in affected folders. This note provides instructions for contacting the attackers, along with payment details and deadlines.
Recovering HHJK files is essential because the ransomware alters their structure. Encryption makes files look corrupted or damaged by scrambling their original content with complex algorithms. These algorithms are extremely difficult to decrypt without the correct key. However, with the right strategies, you can often restore HHJK file data without paying the ransom. Professional recovery tools and backup systems can help retrieve lost information. Some files may be partially recoverable, and in some cases, shadow copies remain intact after the attack.
With that said, let's move on to the ransomware itself and see how it functions.
| Ransomware | Hhjk malware |
| Malware Type | Encryption ransomware; File Encrypter; Crypto Virus; |
| Ransomware Message | _readme.txt file on your Desktop (the document asks you to contact manager@time2mail.ch or supportsys@airmail.cc and pay $490 – $980 to decrypt files) |
| Detection Names | Gen:Heur.Mint.Zard.52 (Ad-Aware); Win32:AceCrypter-V [Cryp] (Avast); Win32:AceCrypter-V [Cryp] (AVG); TR/Stop.deamv (Avira); Gen:Heur.Mint.Zard.52 (BitDefender); Win32/Filecoder.STOP.A (ESET-NOD32); HEUR:Trojan-Ransom.Win32.Stop.gen (Kaspersky); Trojan.MalPack.GS (Malwarebytes); Packed-GDV!9603B8FF454A (McAfee); Ransom:Win32/StopCrypt.PBM!MTB (Microsoft); |
| Infection Symptoms | – Documents, photos, music, videos, and other file types have an additional extension – .hhjk (i.e., image1.jpg.hhjk); – Files can't be opened; – There's a "_readme.txt" file on your Desktop demanding payment for decryption; – Your Antivirus software displays one of the abovementioned detection names; |
| Infection Methods | – Clicking on malicious ads; – Clicking on suspicious Image names in email messages; – Opening suspicious email attachments; – Opening or running suspicious .exe, .run, .zip, .rar, .doc, .xls, .pdf, and .js files; – Downloading files from third-party websites; – Using Peer-to-Peer networks (torrents); |
| Removal Methods | – Scan your PC with a trustworthy antimalware or antivirus software (programs mentioned in detection names); – Remove the Hhjk ransomware from your system; – Restore files with one of the methods below; |
As you can see, the Hhjk ransomware has multiple distribution methods and can infect your computer through emails, attachments, executable files, third-party apps, torrents, etc. Preventing such an infection will require staying vigilant regarding your incoming email messages, websites you visit, and files you download. Otherwise, you'll have to rely on Hhjk file recovery methods.
Part 2: Understanding HHJK File Infections
HHJK file recovery starts with understanding how the infection spreads. The ransomware uses several methods to enter your computer system. Knowing these methods helps you avoid future infections. Most attacks happen due to user mistakes. Cybercriminals exploit human behavior and system weaknesses.
Common infection methods include:
- Malicious email attachments that look legitimate from banks or shipping companies
- Fake software updates from untrusted websites claiming security fixes
- Infected USB drives and external storage devices from unknown sources
- Compromised remote desktop connections with weak passwords
- Malicious advertisements on websites that download files automatically
- Peer-to-peer file sharing networks containing infected torrents
- Cracked software and illegal downloads from suspicious sites
- Vulnerable network security settings without proper firewall protection
- Social media links that redirect to malicious download pages
- Compromised websites that inject malware through browser vulnerabilities
- Email attachments disguised as invoices, receipts, or legal documents
Part 3: How to Recover Hhjk Files?
Acting quickly is crucial for recovering HHJK files successfully. Your initial actions play a significant role in determining how much data can be restored. Stay calm, but move fast to prevent further damage. Many users make early mistakes that complicate the recovery process, so it's important to follow the correct steps.
The following guide outlines the process for recovering HHJK files. Each step is essential for improving your chances of success. Following them in order ensures the best results, while skipping steps can lower the likelihood of recovery. Keep track of every action you take, as detailed notes can be useful if professional assistance is needed later.
Now that we know more about the Hhjk ransomware, we can jump straight into Hhjk file recovery, where we'll show you what to do if this tedious ransomware has already infected your computer. Follow the guide below, and you'll get your vital data back.
Isolate the Device
In any malware infection situation, the first thing to do is to isolate the infected device. It means disconnecting all external storage devices from the computer and disconnecting the computer from your home network to prevent the spread of ransomware and the infection of additional files.
Identify the Infection and Remove It
After successfully isolating your computer from the rest of your storage and network devices, you can move on to the infection identification. The Hhjk ransomware can be recognized in two ways:
- The extension on the encrypted files, which will always be .hhjk;
- The detection names your computer's antivirus tool displays, like the ones in the table above.
From there, you can use the antivirus to safely remove Hhjk ransomware from your computer and focus on decrypting the infected files.
Use Ransomware Decryption Tools
While there's no official Hhjk ransomware decryption software, the fact that Hhjk belongs to the Djvu ransomware family means you can use Emsisoft's Djvu decryptor to get your files back, and here's how:
- Download Emsisoft's STOP Djvu Decryptor, install the app on your computer, and follow the prompts.
- Click the Decrypt button and watch the app do its job from the status view window.
If you need help, Emsisoft also provides a detailed how-to guide for using the decryptor app, which you can find on the company's official website. And if the app can't see and decrypt all your files, you can also employ a dedicated data recovery tool.
Recover Hhjk Files With a Recovery Tool
If you lose data after a Hhjk ransomware infection and want to retrieve it, you can use professional data recovery software. While Djvu decryptor might or might not work for Hhjk ransomware, an app like Wondershare Recoverit will undoubtedly retrieve your lost files, as it was created to work during virus and malware infections, among other data loss situations it supports.
It can quickly and safely recover over 1,000 file types from 2,000+ storage devices, and using it for Hhjk file recovery is remarkably straightforward. Here's how you can do that:
- Open the app, tap Hard Drives and Locations, and choose a disk to recover data from.

Alternatively, right-click a folder in File Explorer and tap Scan for deleted files with Recoverit.
- The app automatically launches a deep scan of the selected folder or disk drive.
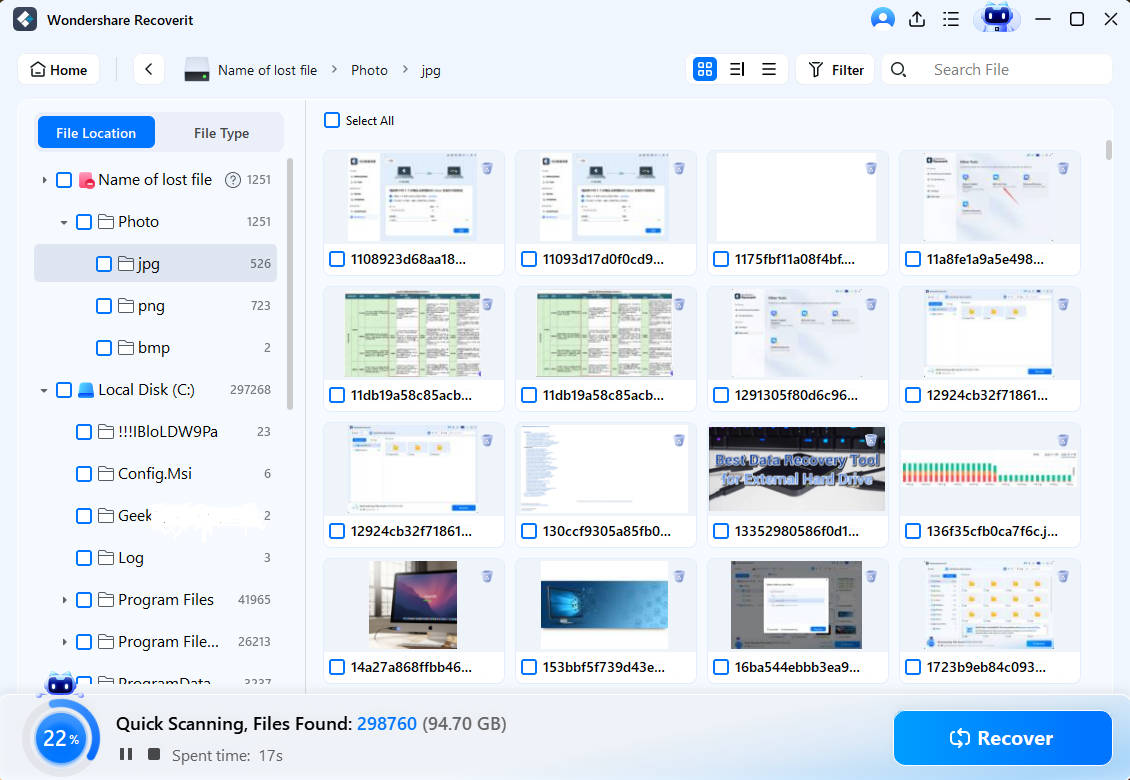
- Modify file filters to search for specific data.
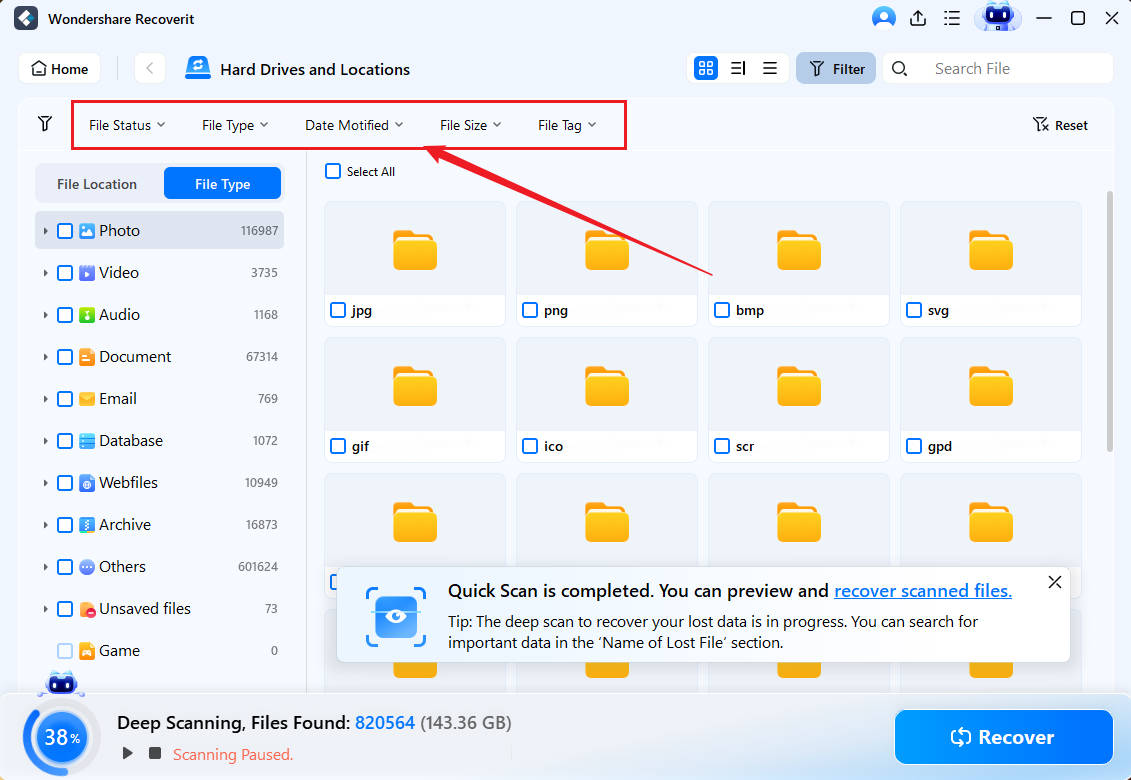
- Use keywords to search for specific files.
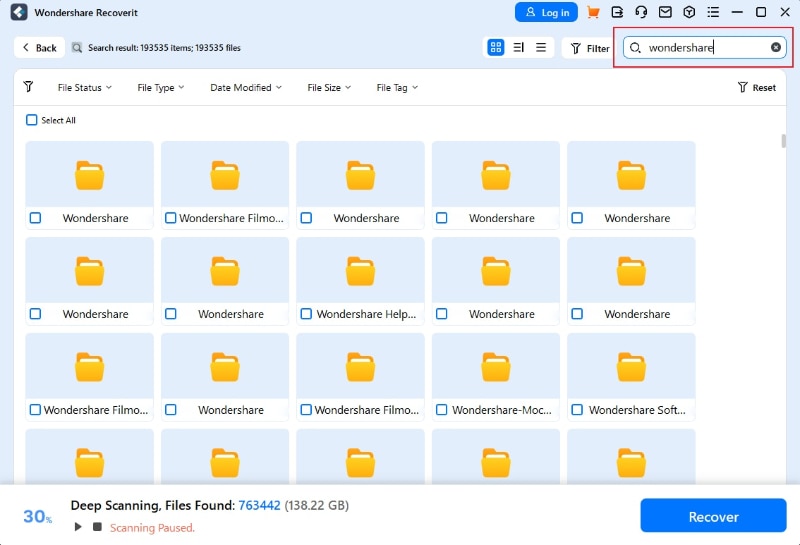
- The app lets you preview discovered files so you can be sure those are the files you're looking for. If they are, hit the Recover button.
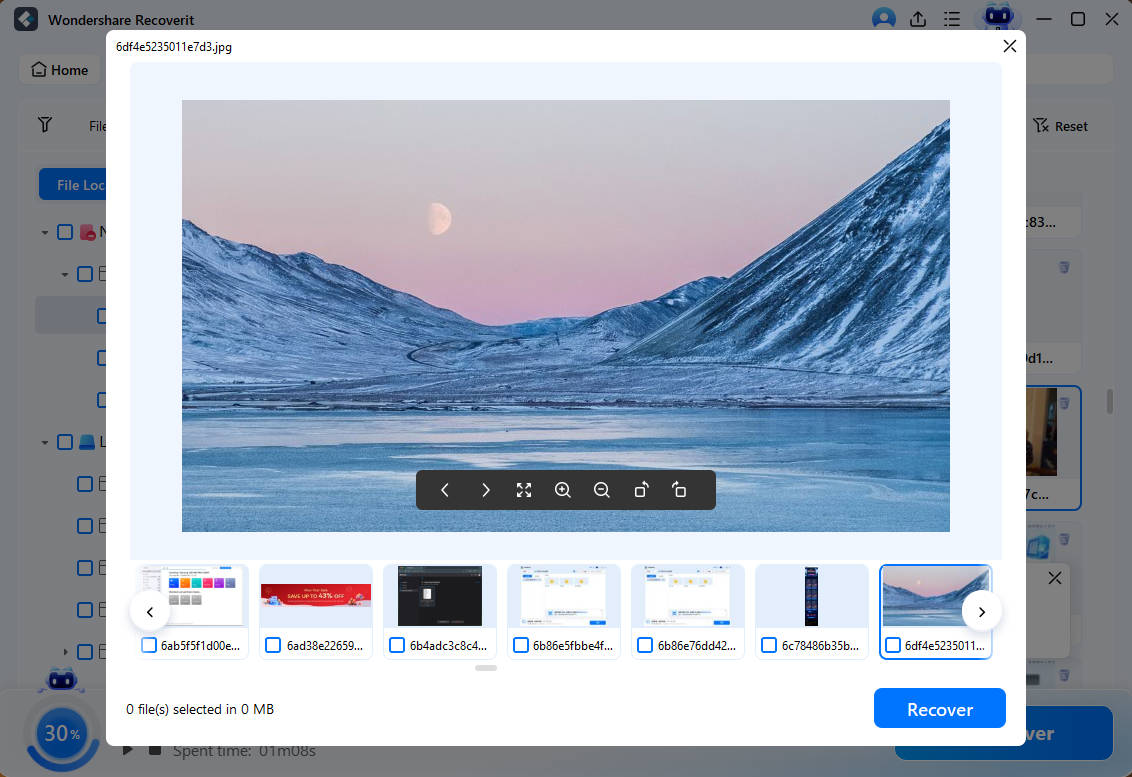
- Select the discovered items after the scan, or pause and stop the scan at any moment and hit Recover to save the files.
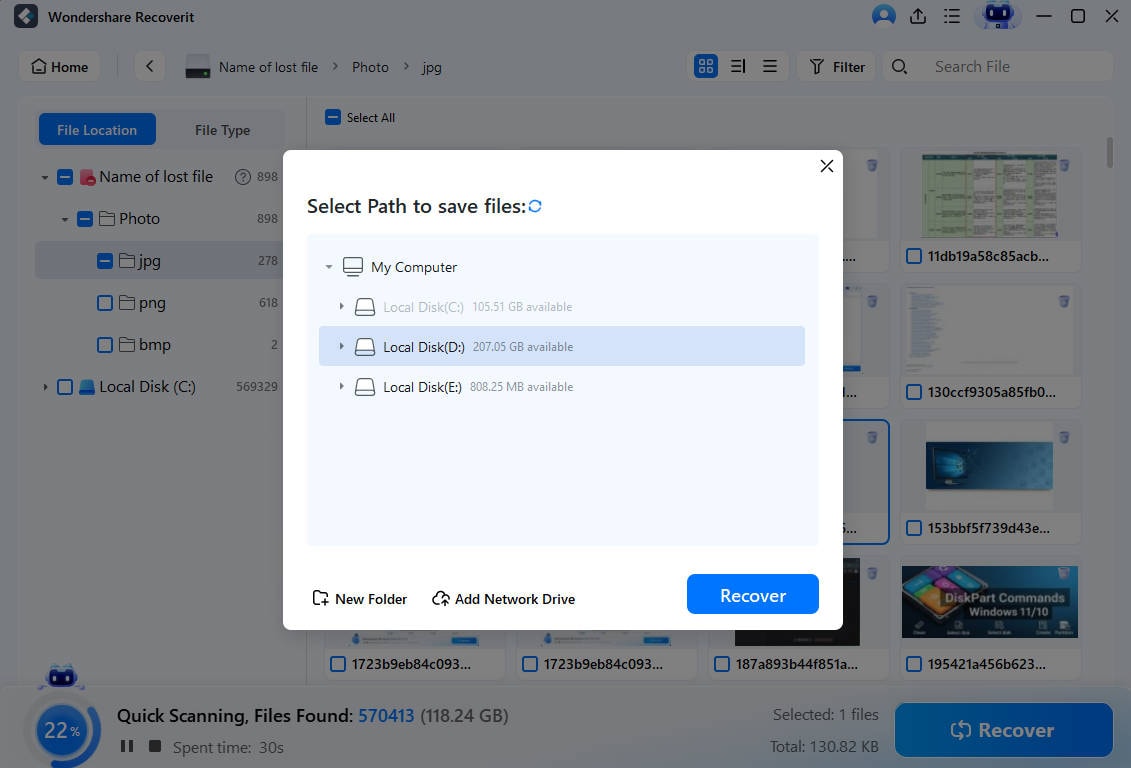
That's all you'll need to do, and you can get your files back within a few minutes, depending on the size of the scanned folder or drive.
Create Data Backups
Restoring lost files from your backups is another method for handling Hhjk file recovery. You can use Windows built-in backup tools or third-party apps with a more user-friendly interface. Wondershare UBackit is one of them.
Part 4: Pro Tips: How to Avoid Ransom Attacks in the Future
Learning how to avoid Ransom attacks in the future protects you from repeat incidents. Prevention is always better than attempting HHJK file recovery after an attack. The cost of prevention is much lower than recovery. Good security habits become automatic with practice. These strategies will strengthen your digital security significantly.
Effective prevention strategies include:
- Create regular backups on offline storage devices that disconnect after each backup session
- Keep your operating system and software updated with automatic updates enabled whenever possible
- Use reputable antivirus software with real-time protection and regular definition updates
- Avoid clicking suspicious email links and attachments, especially from unknown senders
- Download software only from official vendor websites and verify digital signatures when available
- Enable firewall protection on all network connections and configure it to block unnecessary ports
- Use strong, unique passwords for all accounts and enable two-factor authentication where possible
- Keep offline backup copies stored in a different physical location
- Monitor your network for unusual activity and unknown devices
- Update router firmware regularly and change default passwords
- Use email filters to block suspicious attachments and links automatically
Scan and Remove the Ransomware
Before recovering HHJK files, the first step is to eliminate the active ransomware threat from your system. File restoration should only begin after the malware is completely removed, as active ransomware can encrypt newly recovered files or spread to other connected devices. Perform a full system scan using trusted antivirus software such as Malwarebytes, Norton, or Kaspersky to ensure thorough removal.
- Restart your computer and press F8 while it starts up to access Safe Mode. Some newer systems may require different methods to enter Safe Mode. Safe Mode runs only the necessary system files, blocking the ransomware from disrupting the removal process.
- Use your antivirus or malware removal tool to scan the system thoroughly. Do not delete files immediately—quarantine them first to allow recovery in case an important file is mistakenly removed.
- After ensuring no essential files are affected, remove the quarantined ransomware files completely. Reboot your system to exit Safe Mode and verify that the ransomware has been successfully removed.
This method enhances security and reduces the chances of interference from malware during the recovery process.
Restore Lost data from Backups (If Available)
Backup restoration is the most reliable method for HHJK file recovery. Check all your backup sources before proceeding. This includes cloud storage, external drives, and network backups. Look for automatic backups you might have forgotten. Windows File History creates automatic backups. Time Machine does this on Mac computers.
Verify that your backups are clean and uninfected before restoration. HHJK Ransomware sometimes spreads to connected backup devices. The infection can happen weeks before you notice it. Check backup dates to find clean versions. Scan backup files with antivirus software first. Use a different computer for scanning if possible.
Then restore your data to the cleaned system carefully. Start with a few test files first. Make sure the restoration process works correctly. Don't restore everything at once. This gives you chances to stop if problems occur. Keep multiple backup versions if space allows. Older backups might have files you forgot about.
Conclusion
HHJK file recovery is possible with the right approach and tools. Quick action and proper techniques can save most of your important data. Many victims successfully recover their files without expert help. The key is staying calm and following proven methods. Don't pay the ransom, as this only encourages more criminal activity. Payment doesn't guarantee file recovery. Some criminals take money and disappear. Others demand additional payments later.
How to avoid Ransom attacks in the future should be your priority after recovery. Implement strong security measures and maintain regular backups. Create multiple backup copies in different locations. Test your backups regularly to ensure they work. Remember that prevention costs less than recovery and causes much less stress. Good security habits protect you from many other cyber threats too. Start building these habits today before you need them.
Try Recoverit to Recover HHJK Files
Security Verified. Over 7,302,189 people have downloaded it.
FAQ
-
Q1: Can I recover HHJK files without paying the ransom?
Yes, you can often recover HHJK file data without paying criminals. Use professional recovery software, restore from clean backups, or try file recovery tools. Many users successfully retrieve their files through these methods. HHJK file recovery is possible in most cases with patience and the right approach. Free decryption tools sometimes become available for older ransomware variants. Security researchers work constantly to break ransomware encryption. Check websites like NoMoreRansom.org for free decryption tools. Some files might be recoverable from system restore points or temporary folders. -
Q2: How long does HHJK file recovery take?
HHJK file recovery time depends on several factors including file size and system speed. Small files may recover in minutes while large databases take hours. The recovery software speed and your computer's processing power affect the timeline. Most users complete recover HHJK file operations within a few hours. Hard drive health also affects recovery time. Damaged drives take much longer to scan. SSD drives usually work faster than traditional hard drives. Network-attached storage might take longer due to connection speeds. Be patient and let recovery tools complete their work. -
Q3: What should I do immediately after discovering HHJK Ransomware?
Disconnect from the internet immediately to prevent further damage from HHJK Ransomware. Unplug network cables or turn off WiFi right away. This stops the ransomware from downloading additional malware. It also prevents data theft that sometimes happens with ransomware. Don't restart your computer or try to open encrypted files. Restarting might complete the encryption process. Opening files can trigger additional malware features. Run antivirus scans in Safe Mode and document the infection for authorities. Take photos of ransom notes and error messages. Start your HHJK file recovery process only after removing the active threat completely.


 ChatGPT
ChatGPT
 Perplexity
Perplexity
 Google AI Mode
Google AI Mode
 Grok
Grok






















